What’s new in UserLock 9.7
Working Hours Reports
With Version 9.7, UserLock introduces easy-to-read reporting options that offer a detailed view of working hours for all users on your network. Every connection event, across all session types are considered to build an accurate picture of each users working hours by day, week or month.
Accurately tracking working hours can help Human Resource Teams react as users approach overtime thresholds, ensure labor regulation compliance (for example in the U.S, the Fair Labor Standards Act (FLSA) for employee timekeeping), and reduce potential liability for unpaid hours.
Reports can also help quickly detect suspicious or unauthorized access from an employee’s Active Directory account.
Security is also an iterative process. The Working hours report can be used to adjust UserLock’s own access control rules. Restrictions that control when and how a user can connect to the network can be easily revised - or temporary rules defined - that respond to changing events.
Working Hours History
A detailed daily overview of the hours worked by users on your network. View the time a user first logged on (or unlocked) during the day, the time a user last logged off (or locked) during the day and the total session times – active, locked and combined.
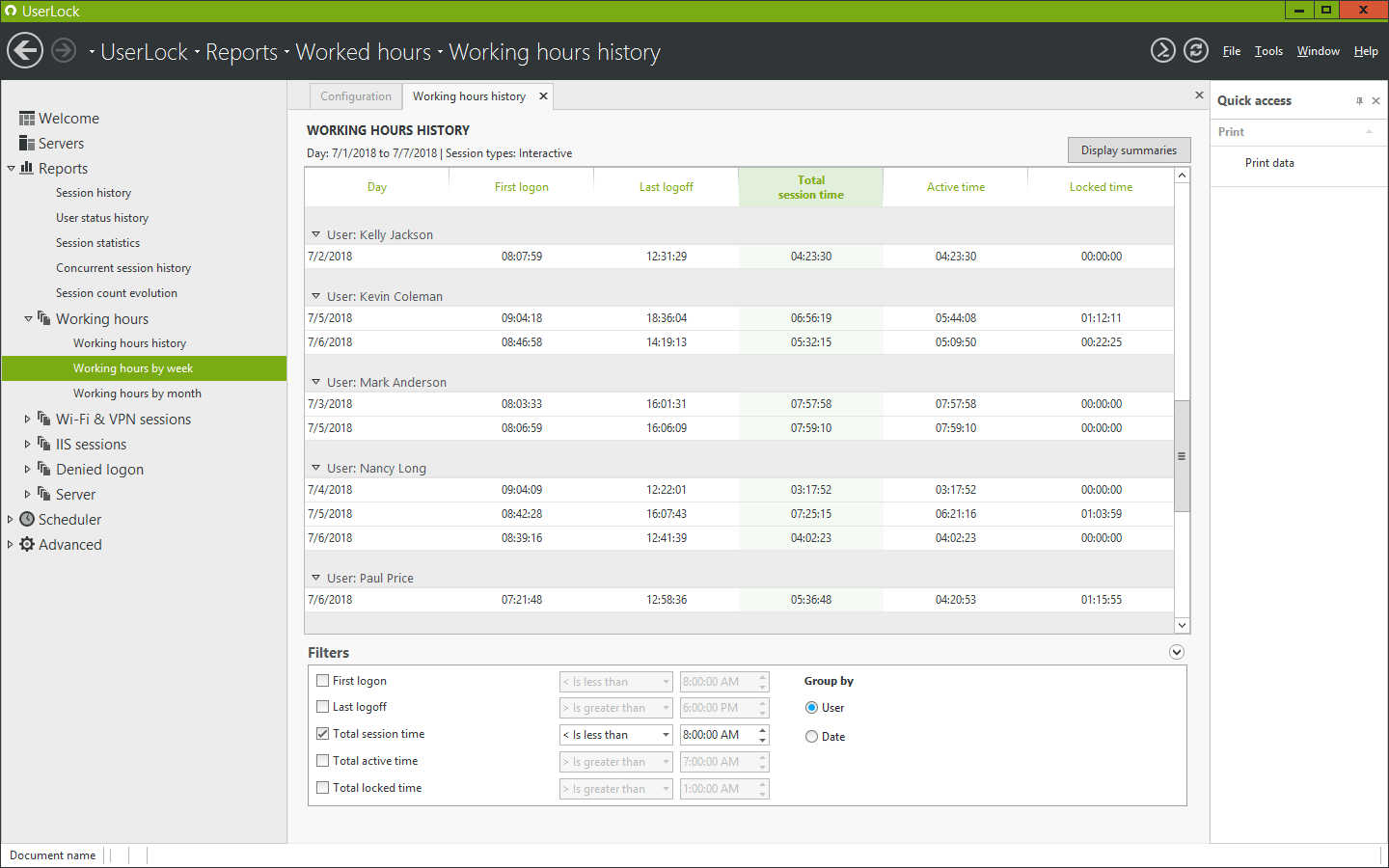
With this new report, UserLock allows you to keep a permanent eye on your users. You can use the reports to better track and control the number of hours worked during the day for each user in your network – including scheduled rest periods.
Working Hours by Week
A more global view offers detailed statistics by user per week. You will be able to see the total connection time over the defined period (active, locked and combined session totals), the average times of the first login (or unlocking) and the last logoff (or locking) and the total number of days worked during the period.
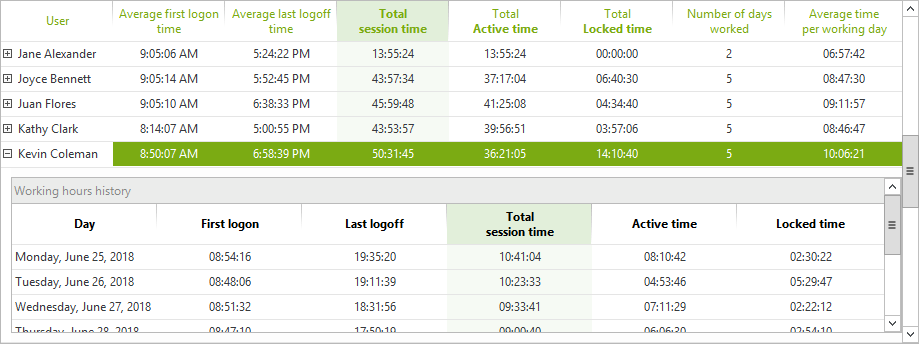
This report is accompanied by a graph that displays the details of the hours worked for any selected user. For each day, active session time is displayed in blue and locked session time is displayed in grey. This illustrates clearly the users daily activity including start and finish time. Locked session time can be interpreted in context with the organization and a users’ role (scheduled rest periods, meetings etc.)
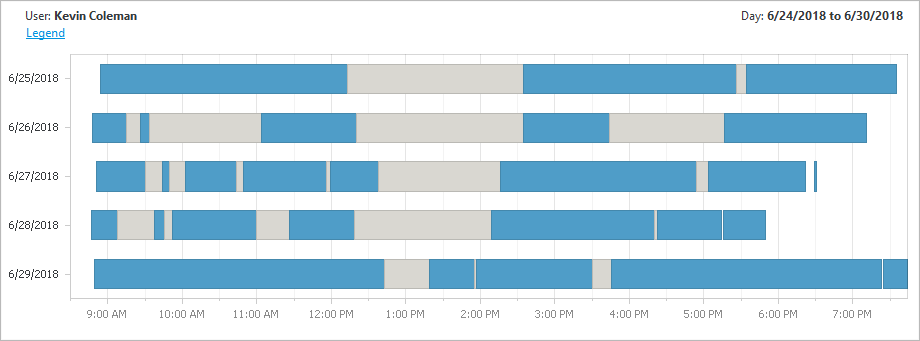
This report allows you to do a more detailed analysis of your users' working hours and detect suspicious or unauthorized access events.
Working Hours by Month
Get detailed statistics for each user per month. As for the report per week, you will be able to see the total connection time over the defined period (active, locked or combined session totals), the average time of the first login and the last logoff and the total number of days worked during the period.
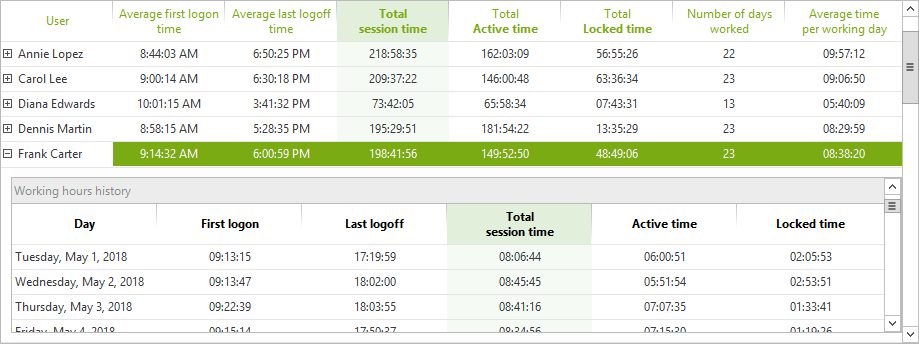
This report is accompanied by a graph that displays the total hours worked for the selected user each day. In contrast to the previous report, all active session times for each day are accumulated and likewise for locked session time. These two totals are then represented as a stacked column chart.
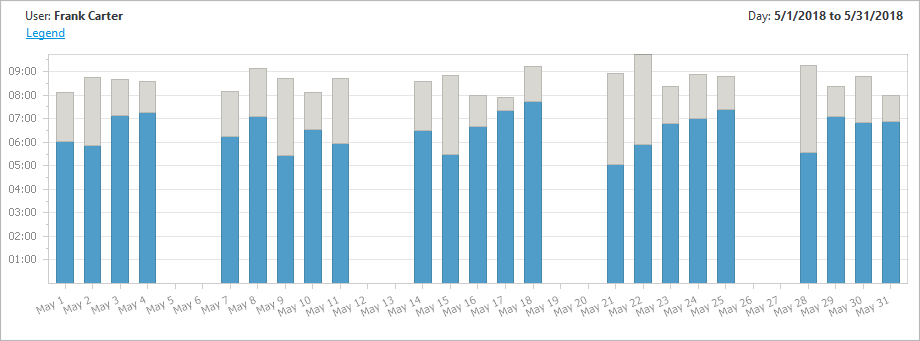
This report allows you to do a more global analysis of your users' working hours. You get a broader and less detailed view than in the previous report.
For all three reports, powerful filtering options let you customize your report to focus only on the relevant data you need. Filter users by specific times (first logon, last logoff, total session time etc.), group the information by user or date, select only specific session types. Quickly drill down and find users who do not meet certain criteria without having to reload the report.
With these new reports, UserLock gives you more control of your users working hours. If your company has a flexible hours policy or your users sometimes work from home, you'll be able to check that they're doing the right amount of hours every week / month. So, if a user is doing too many hours or not enough, you can detect it and fix it.
You will also be able to support HR investigations or investigations in the event of a breach by providing accurate and detailed information about who was connected on which day, at what time and for how long.