Multi-factor authentication
UserLock allows you to implement Multi-Factor Authentication (MFA) in your environment which requires a user to authenticate with an additional (second) factor. You can create granular access policies to specify MFA on certain connection types, and with different frequencies for your users, groups or OUs.
UserLock supports the following MFA methods:
- Push notifications with UserLock Push app,
- TOTP through authenticator applications and programmable tokens,
- HOTP with security tokens from Yubico.
Here in the protected account, you can configure MFA based on sessions types, connection types, and how often to prompt users:
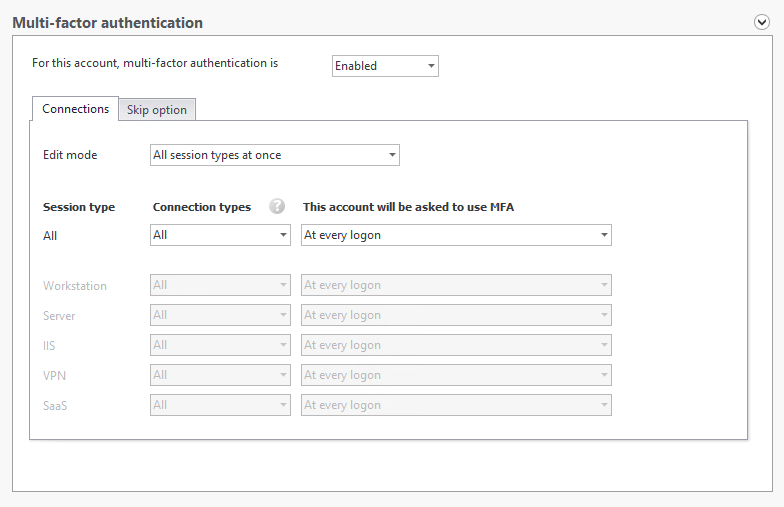
To implement MFA, please see our use cases section for complete guides relating to different session types.