Enroll users with Token2 HOTP
Help users activate and use a Token2 HOTP hardware token as a second factor of authentication (MFA) with UserLock.
Token2 HOTP is a hardware token that generates HMAC-based One-Time Passwords (HOTP) for MFA.
Unlike time-based tokens (TOTP), HOTP codes are generated sequentially — making them ideal when system clocks are not perfectly synchronized.
UserLock manages Token2 HOTP configuration entirely on the server side, ensuring a simple setup with no client configuration required.
When users authenticate, they simply touch their Token2 device. The token automatically enters the authentication code, preventing typing errors.
Note
🚩 Before following this guide:
We recommend reading How to implement MFA for general recommendations, communication tips, and preparation steps to ensure a smooth rollout.
To use Token2 HOTP with UserLock:
A Token2 device supporting HOTP (for example, Token2 T2F2-ALU).
The device must be plugged into a USB port on the user’s computer during logon.
The first MFA enrollment must be performed through a direct local session (not via RDP).
Once configured, the Token2 can be used for RDP, IIS, SaaS, or VPN sessions.
Important
Enrollment from a remote session (RDP, IIS, or VPN) is not supported.
Note
💡For a detailed list of compatible Token2 devices, see Token2’s official compatibility list
Before enrolling, make sure that MFA is enabled for the user account in UserLock.
Note
See Access policy management to learn how to apply an access policy in UserLock.
See MFA policy reference for details on MFA policy rules and options.
Plug the Token2 HOTP device into the computer’s USB port.
(Do not connect via RDP for this step.)Log in to the Windows session.
When prompted by the UserLock Desktop Agent, select USB Token as the MFA method.
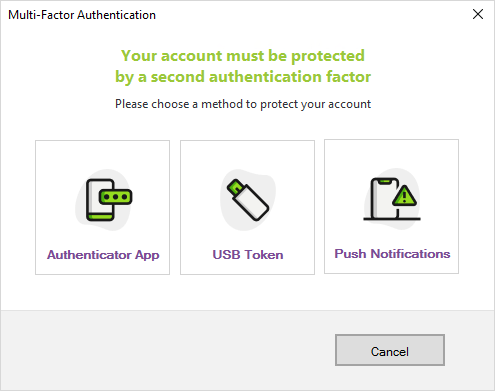
The agent automatically detects the Token2 device:
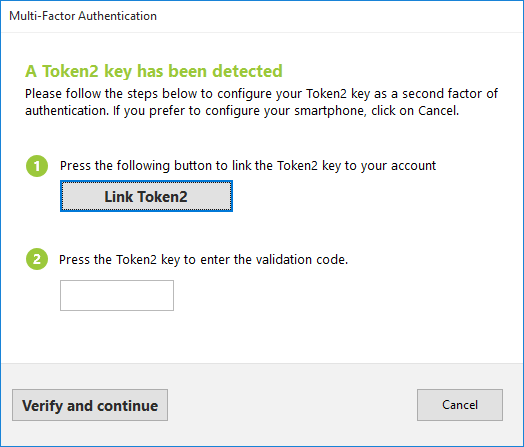
and programs it using the MFA secret. The process runs securely in the background — the secret is never displayed.
Once linked, the Token2 status updates to Success in the dialog box.
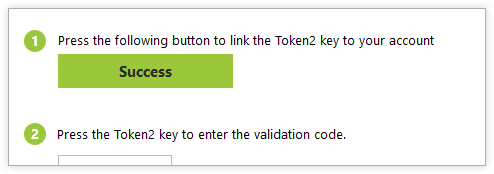
The cursor appears in the authentication code field — simply touch the Token2 device.
The token automatically enters a 6-digit code, validating the MFA setup.
✅️ Enrollment is now complete. Future logins can occur through RDP or other remote sessions.
For subsequent logins:
Plug the Token2 HOTP into a USB port.
Log in to Windows (local or RDP session).
When prompted for MFA, touch the Token2 button:
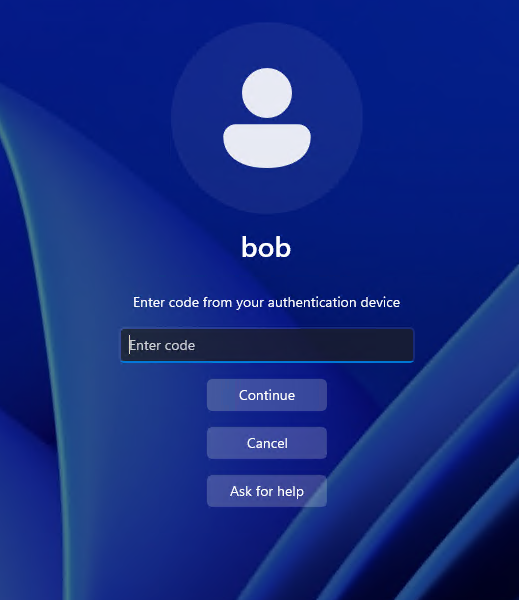
The token enters the 6-digit code automatically, and authentication completes.
Enrollment must be done locally (not via RDP).
After enrollment, users can log in remotely using their Token2 HOTP device.
Administrators or users can:
Use a backup MFA method (e.g. Authenticator App or Recovery Codes), if configured.
Use the optional Ask for Help feature to notify an administrator.
The admin can then:Reset the MFA key
Temporarily disable MFA
Assist in activating a replacement token (e.g. YubiKey)
If a user previously used a TOTP method:
Reset the user’s MFA key.
Reconfigure MFA using Token2 HOTP as described in this page.
Choose HOTP when:
Your UserLock server runs on a virtual machine with irregular clock synchronization (e.g. Hyper-V environments).
You want to avoid time-based synchronization errors that may occur with TOTP.
Limitation | Description |
|---|---|
Enrollment restricted to local sessions | Cannot enroll Token2 HOTP via RDP, IIS, SaaS, or VPN. |
Virtual machine support | Supported on VirtualBox (configuration and authentication). |
HOTP desynchronization | May occur after multiple offline logins. By default, a 6-code offset is allowed. Adjust via the Max HOTP code count advanced settings parameter. |