Service
This section groups the settings related to notifications sent by the UserLock service and the impersonation account used for privileged operations.
Note
To access this page, go to Server settings ▸ General.
You need at least read permission on Server settings to view this page.
Notifications help administrators monitor the health and configuration of UserLock proactively. They provide immediate visibility on critical events, so you don’t have to rely solely on periodic log reviews.
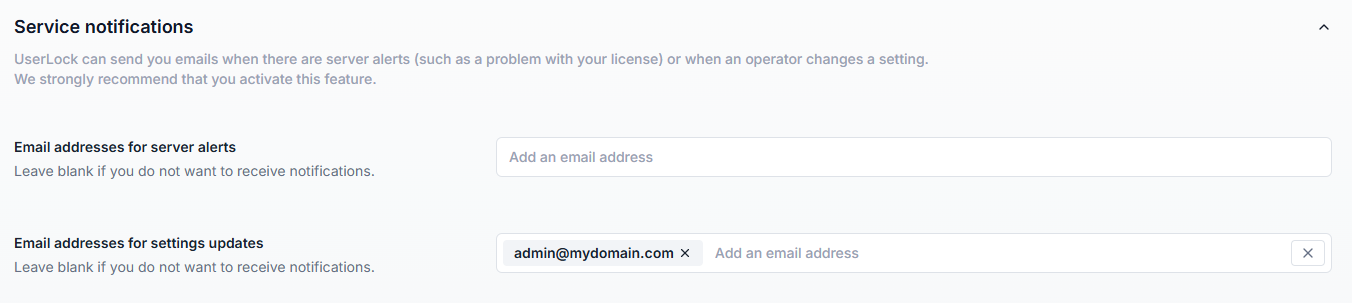
You can configure two types of email alerts:
Sent when there are operational or licensing issues, for example:
License expiration or exceeded license count
Service availability problems
General server alerts
Configure recipients in the Email addresses for server alerts field.
Leave blank if no notifications are required.
Sent when operators make changes to UserLock settings, such as:
Modifying permissions
Editing server properties
Changing access policies or messages
Updating agent distribution settings
These actions are always logged in:
the Windows Application event log (UserLock Admin Actions under the Applications and Services Logs section),
the UserLock database (see Administration reports).
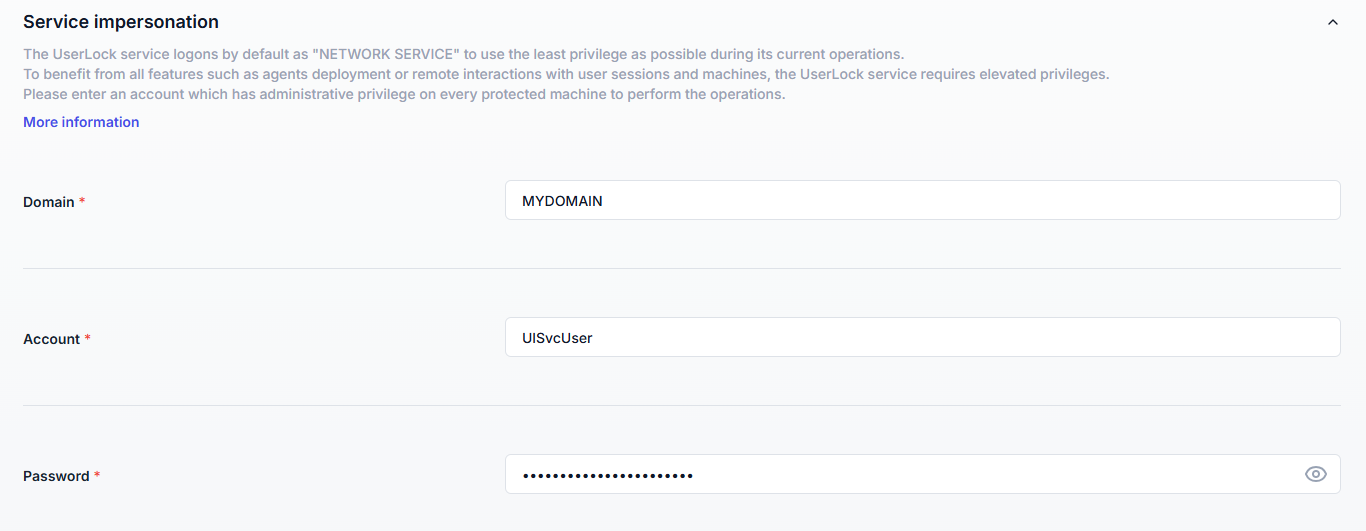
By default, the UserLock service runs as the built-in Network Service account (least privilege).
However, some operations require higher rights. That’s why the configuration wizard prompts for an impersonation account with the necessary privileges.
This account is used by the service for:
Deploying all agent types
Applying access control rules (lock/logoff sessions)
Automatic logoff with Logoff disallowed sessions
On-demand system operations (lock/logoff/shutdown/restart)
Synchronization between Primary and Backup servers
Database connections in Windows authentication mode
This section displays the credentials entered during the corresponding Configuration Wizard step and allows you to edit or change them if necessary.
Every time you change the information, a test is performed on the provided credentials. If there is a problem, an error message is displayed below the password field.
Note
No modifications are made to your Active Directory or schema.
The impersonation account is used only by the UserLock service. Desktop Agents always run as Local SYSTEM.
The account <domain>\<UserLock server name>$ must have read rights on user and computer objects in AD.
The impersonation account must have permission to log on as a service. Before changing this setting, log in to the UserLock server, open Local Security Policy (secpol.msc), go to Local Policies > User Rights Assignment, and ensure that the target account is in the Log on as a service list and not in the Deny log on as a service list.
Always configure server alerts: never leave the notification fields blank, or you might miss license expiry or service outages.
Use a dedicated impersonation account with only the required rights (not a personal domain admin).