Apply MFA for IIS Apps
UserLock can enforce multi-factor authentication (MFA) on IIS-based applications such as Outlook Web Access (OWA), RDWeb, SharePoint, CRM, or custom intranet sites. When a user signs in, the IIS UserLock agent redirects them to a dedicated MFA web application where they enroll and validate their MFA code before accessing the protected resource.
The IIS applications must be protected by the UserLock IIS agent using HTTP Module technology.
The IIS MFA feature must be installed on the IIS server.
The IIS MFA server must be accessible both internally (private network) and externally (Internet).
The external router/firewall must allow traffic to the IIS MFA port and redirect it to the server.
Example: An Exchange Client Access Server typically meets these requirements.
Run the UserLock console.
In the Environment ▸ Machines page, go to the line of the IIS server that will be hosting the IIS applications to protect with UserLock. In the IIS agents columns, open the agent button and click on Install.
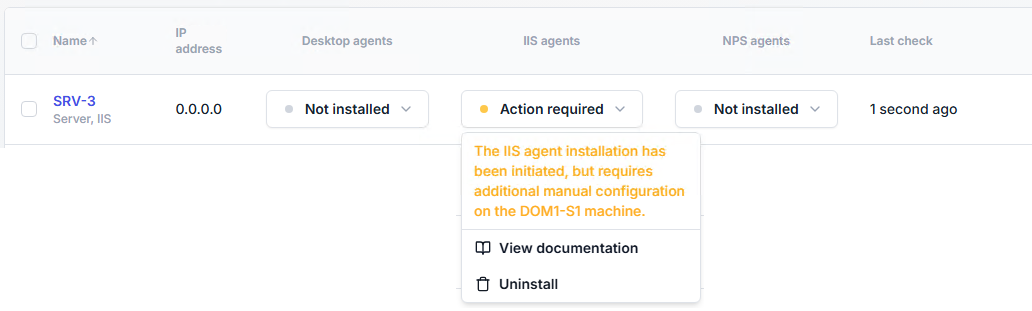
On that IIS server, configure each application to use the UserLock IIS agent (HTTP Module). See protecting IIS applications with UserLock agent.
The IIS MFA feature is now included in the default UserLock installation.
If UserLock is not installed on the server:
Run the UserLock installer and select Custom setup.
From Modules, select IIS MFA.
If UserLock is already installed:
Open Control Panel → Programs → UserLock → Change.
Add the IIS MFA feature.
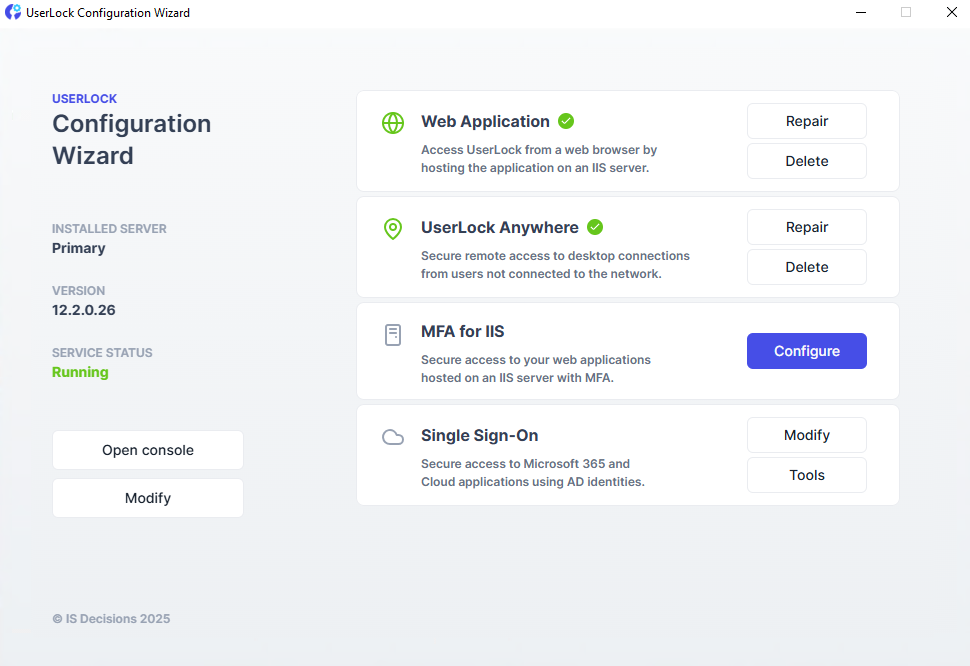
Launch the Configuration Wizard from the Start menu.
Click Configure next to MFA for IIS.
Select the IIS website where the MFA app should be added.
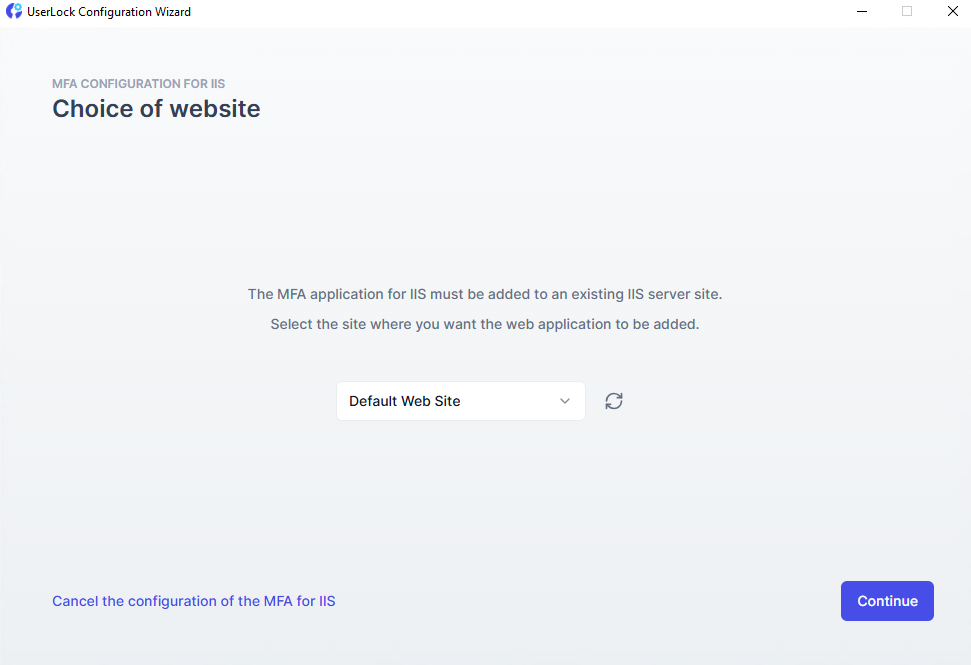
Complete the wizard to deploy the application.
Open the UserLock console.
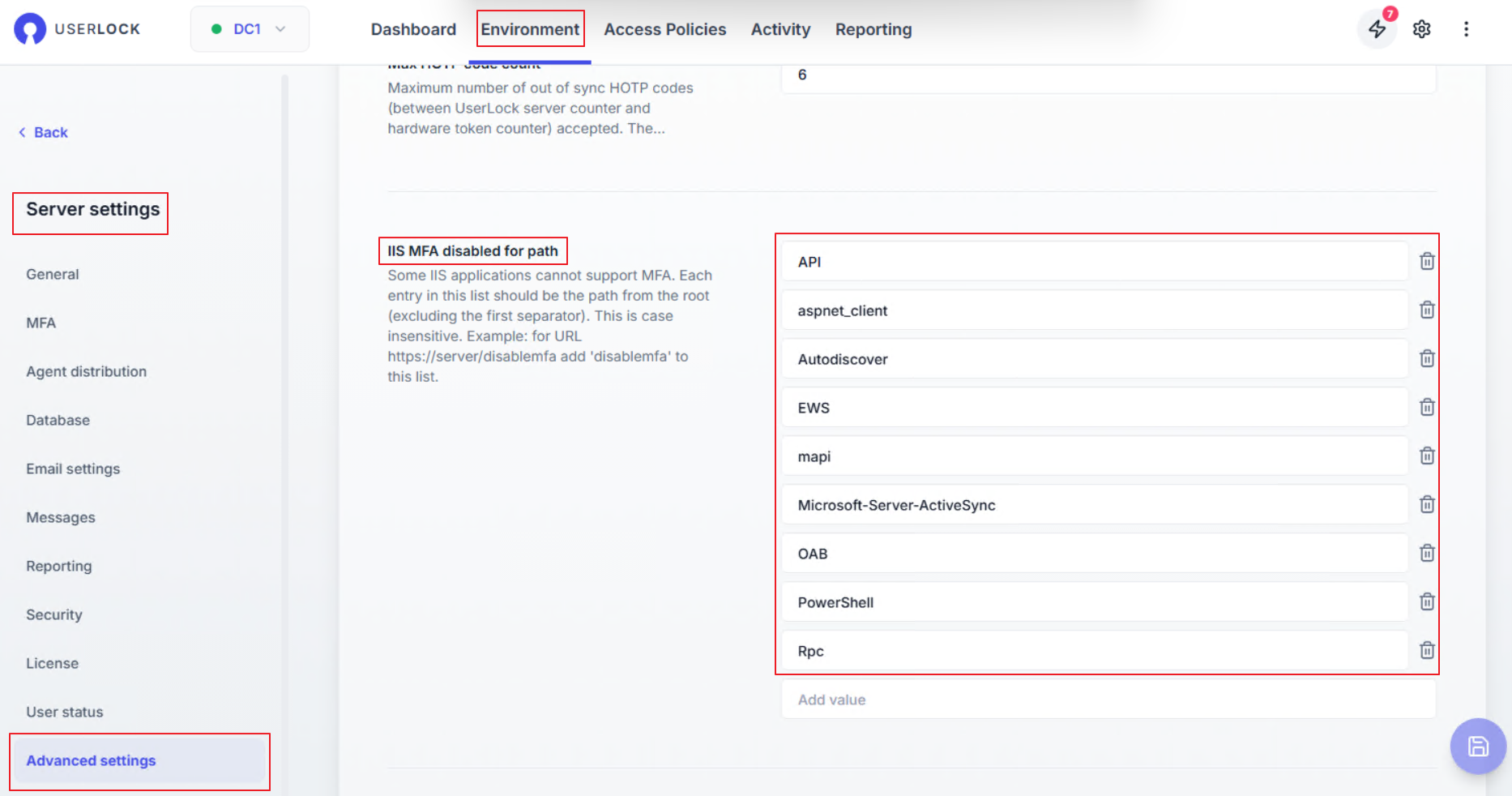
Go to ⚙️ Server settings ▸MFA
Enter the URL of the IIS MFA app you configured.
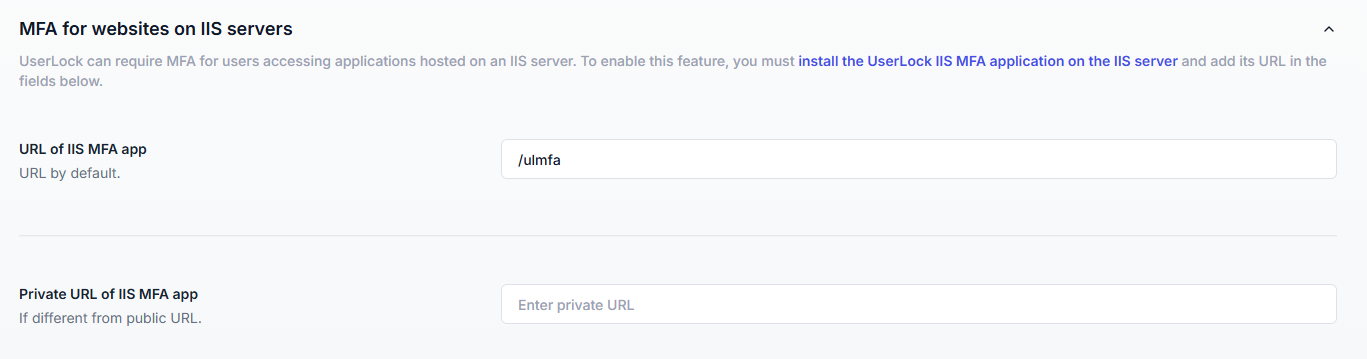
Use Test to validate the connection (this button only appears if you enter an absolute URL).
Click Save button to save.
To enforce MFA on IIS connections, you need to create a new access policy.
👉️ Follow the general steps described in Configure an access policy until you reach the Policy type selection. At this step, choose Multi-factor authentication.
You will then arrive on the MFA rules form.
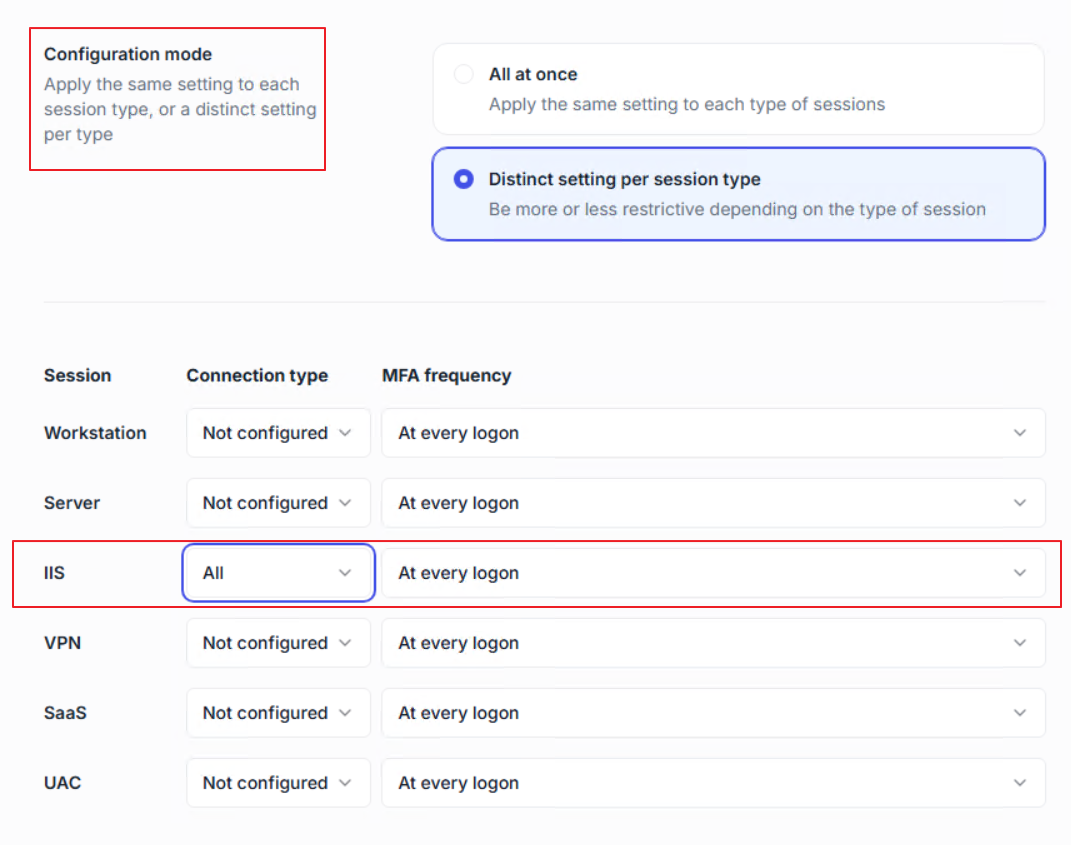
Set MFA application to Enabled.
Choose configuration mode:
All at once (same settings for all session types)
Distinct setting per session type (recommended, so you can configure MFA separately for IIS connections).
Configure IIS session rules
For Connection type, choose whether MFA applies to all IIS logons, only remote ones, or only from outside IPs.
For MFA frequency, select how often MFA is required (at every logon, at first logon of the day, when connecting from a new IP, etc.).
Save the rules
The policy is now active and will enforce MFA on IIS connections.
Note
For the detailed meaning of the Connection type and MFA frequency options, see the MFA policies reference.
Browse to the protected IIS application (e.g., OWA).
On the first login, the user is prompted to complete their MFA enrollment (QR code).
On subsequent logins, only MFA validation is required.
Useful resources
For Microsoft Exchange, IIS MFA supports OWA and Exchange Control Panel (ECP) only.
Unsupported Exchange apps remain excluded by default in the advanced settings.