Multi-factor authentication
Multi-factor authentication (MFA) is one of UserLock’s most important security features. MFA policies let you require additional verification on user connections to protect accounts against compromised credentials.
Enable MFA flexibly across any scenario — whether for all users, all administrators, privileged accounts, or specific user groups.
Apply stricter MFA rules for external connections (such as VPN or RDP), and lighter ones for workstation logons.
Allow users to log in seamlessly on their usual workstation but require MFA when connecting from a new IP.
Combine MFA with other restrictions (time, machine, geolocation) for layered access control.
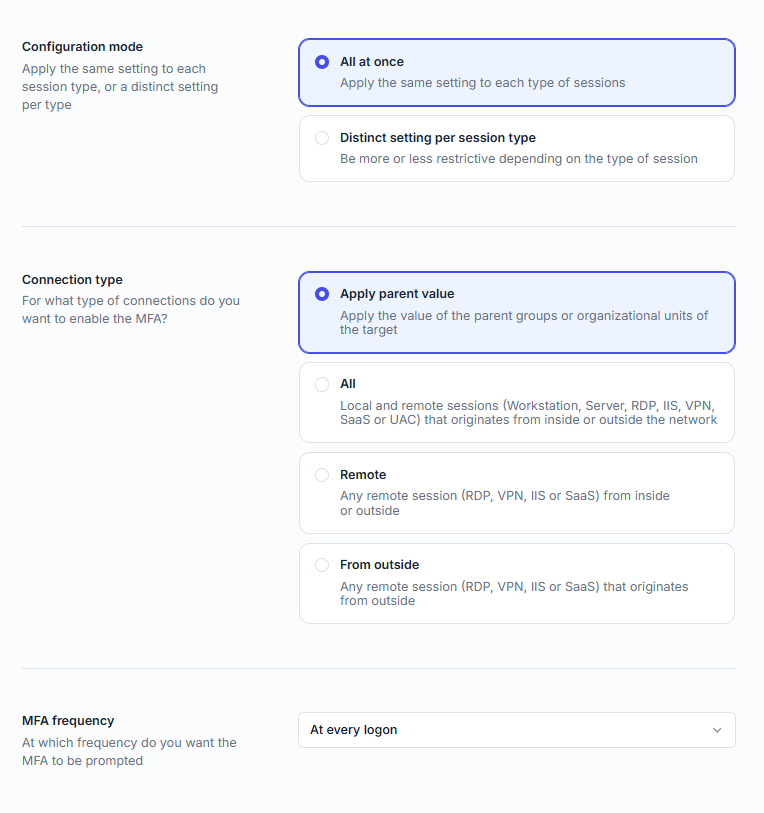
MFA policies can be applied at the user, group, or organizational unit (OU) level.
MFA status and configured methods for each user can be reviewed in the User dashboard and the Environment ▸Users view.
Available MFA methods (push, authenticator app, USB keys, recovery codes, etc.) are configured separately in the Server settings ▸ MFA.
Messages shown to end users (configuration, errors, help requests) are configured separately in the Server settings ▸ Messages.
A dedicated MFA report is available in the Reporting section.
MFA help requests (if enabled) appear in the Activity ▸ MFA Help Request page.
Define how often MFA is required:
All | Enforce MFA on both local and remote sessions. |
|---|---|
Remote | Enforce MFA only on remote sessions (RDP, VPN, IIS, SaaS). |
From outside | Enforce MFA only on remote sessions originating from an external IP address. |
Apply parent value | Inherit the rule from the parent group or OU policy. |
You can define how often MFA is required for a user:
At every logon | Prompt on every logon, unlock, or reconnection. |
|---|---|
At the first logon of the day (once per IP address) | Prompt once per day, unless the IP changes. |
When logging on from a new IP address (once per address) | Prompt the first time a new IP address is used. |
After a given time since last MFA connection (per IP address) | Prompt again after the defined delay. |
After a given time since the last logon (per IP address) | Prompt again based on time since last logon. |
Never | MFA is never enforced. |
Not configured | No rule, unless inherited from a parent policy. |
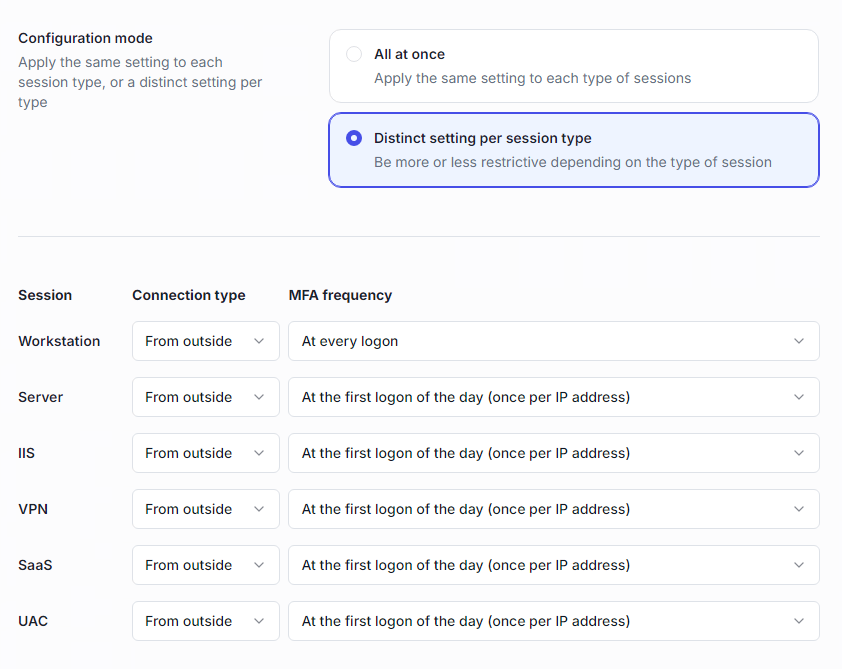
You can apply the same rule to all session types or define distinct rules per type.
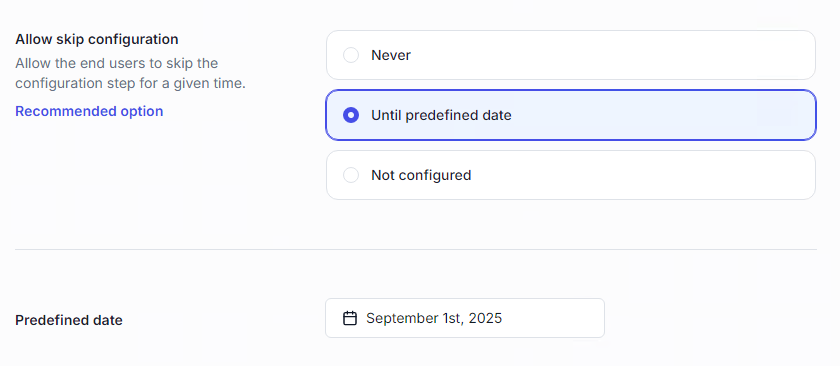
Administrators may allow users to skip MFA enrollment until a specific date to ease onboarding. After this date, login is denied until MFA is configured.
This option is supported for interactive and IIS sessions (as well as VPN if UserLock VPN Connect is used).
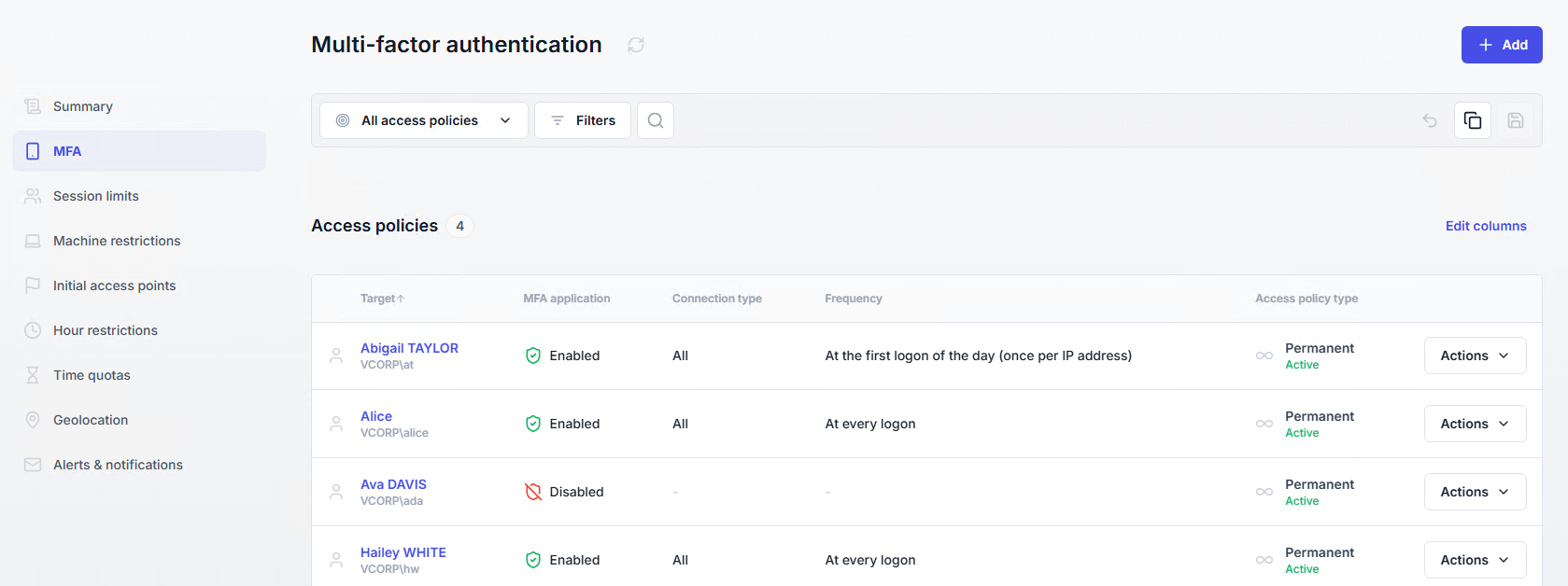
All defined MFA policies can be viewed under the Access Policies > Multi-factor authentication page.