What’s New for UserLock 11
What's new in UserLock 11.2
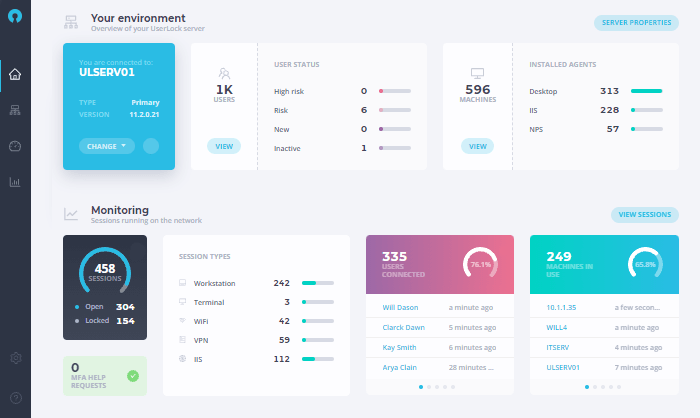
New UserLock Web App
With the new UserLock Web App, IT teams and help desks can access UserLock from anywhere to easily, quickly monitor and respond to network session activity.
Administrators can use the application from any computer, simply with a web browser, without having to install the UserLock desktop console.
The new UserLock Web Application is just the first step in a redesigned UserLock interface. Our goal is to integrate all features into a single application, which can be accessed from a desktop or Internet browser, allowing you to manage MFA and user access seamlessly from anywhere.
For now, this UserLock web application already allows you to:
- Manage machines and servers and the agents installed on them
- View Active Directory users and manage their MFA configurations
- Monitor and react to all active sessions and connected users
- Receive and respond immediately to MFA help requests
- Drill down into granular reports, with improved filtering capabilities, on logon events, MFA events, and denied logons
- Verify in real-time UserLock administrator actions to machines and sessions
If you are users of the old UserLock web console, you'll notice that the interface has been significantly changed. Several elements have been renamed, removed or moved, and many new features have been added to improve the user experience. It is not currently possible to view or modify your protected accounts, nor to schedule or export reports. Soon, these features will be available, as well as further improvements that will make it even easier for you to secure network access.
We hope you will enjoy the changes. Send your feedback direct from the application , take and send screenshots, or tell us what new features you are looking for.
To use the Web App in parallel to your use of the full-feature desktop software, download UserLock 11.2.
What's new in UserLock 11.1
- New SaaS applications for SSO
- SSO Certificate Rollover
- SSO Disaster Recovery
- Diagnostic MFA IIS Test
- Retrieve the real IP address of a client who accessed via RD Gateway
- Configure a Non-Supported SaaS Application
- Download UserLock
New SaaS applications for SSO
Using the existing AD credentials of the user, UserLock’s combination of SSO and MFA offers unrivaled protection against unwanted access for Office 365 and other SaaS apps.
With the release of 11.1 additional enterprise applications are now available for the UserLock SSO platform.

SSO Certificate Rollover
UserLock SSO connects to SaaS applications using the SAML protocol. A certificate is used in this protocol to ensure that requests are authentic. Shared by all SaaS providers, this certificate is an essential element of security and must be limited in duration and renewed regularly.
The time duration of this certificate can now be set during configuration. Afterwards, the certificate will automatically renew and can be activated by the administrator with a single click.
See details here.
SSO Disaster Recovery
Disaster recovery is an essential function for UserLock SSO. Any disruption to the SSO service causes immense inconvenience to both the IT administrators and the Help Desk Team.
UserLock 11.1 allows the configuration of one or more SSO backup servers in order to limit possible interruptions. Once configured, the backup server can be quickly activated in case of a failure of the primary server.
See details here.
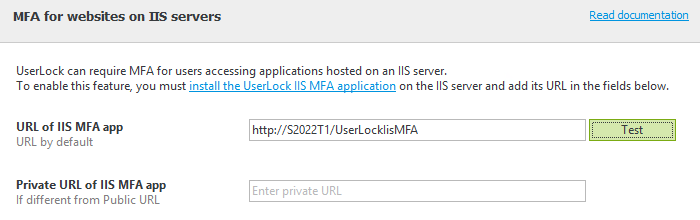
Diagnostic MFA IIS Test
It is now possible to verify the URL for IIS MFA by simply clicking on the new ‘Test’ button.
Retrieve the real IP address of a client who accessed via RD Gateway
To enable this feature, install the NPS agent on the NPS server authenticating the RD Gateway.
Configure a Non-Supported SaaS Application
UserLock SSO allows you to now configure a custom SaaS application using Saml protocol with a dedicated configuration file.
See details here.
What's new in UserLock 11.0
- UserLock SSO and MFA for Microsoft 365 and Cloud Applications
- Access Management for Microsoft 365 and Cloud Applications
- MFA for Microsoft IIS applications
- MFA recovery codes
- Enforce MFA for logins from any machine without a network connection
- MFA | Alternative methods for multi-factor authentication
- MFA | HOTP for machines without network connection
- MFA | Using Token2 ALU, NFC and Bio for multi-factor authentication
- MFA | Using VPN with RADIUS Challenge for multi-factor authentication
- UserLock Anywhere | New web application to better protect remote connections
- UserLock Anywhere | Remotely logoff and lock user sessions over the Internet
UserLock SSO and MFA for Microsoft 365 and Cloud Applications
UserLock Single Sign-on (SSO) provides secure access to Microsoft 365 and cloud applications, using on premise Active Directory credentials. It allows a user to log in only once with their existing AD identity to access both the on premise network and multiple cloud services.
Combined with UserLock’s Multi-Factor Authentication (MFA) organizations can now retain Windows Server AD as their identity management solution - while extending it to work with the cloud.
Supporting Security Assertion Markup Language 2.0 (SAML) protocol to enable federated authentication of Microsoft 365 and other cloud applications, administrators can easily configure each cloud application directly from the UserLock console.
By combining SSO and MFA, UserLock 11 offers seamless access and secure connections to Windows logons, RDP access, VPN sessions, IIS sessions and cloud applications for all users.
Access Management for Microsoft 365 and Cloud Applications
Restrictions based on login context and real-time session management further help verify the identity of an AD user and protects all attempts to access cloud resources.
- Control access to cloud applications with geolocation and workstation restrictions.
- Track and report on who logged in to which cloud application, from which IP address and when.
- Alert on login events that may warrant further investigation, such as a denied login.
MFA for Microsoft IIS applications
Multi-factor authentication (MFA) can now be set up to protect user access to Internet Information Services (IIS) for Windows Server.
The UserLock “Agent Distribution” engine automatically detects servers on which “Internet Information Services” are installed and run. Using “Http module technology” and designed to work on IIS7 and higher, MFA can be used to protect a single web application such as Outlook Web Access, or a whole intranet site.
MFA recovery codes
Unique MFA recovery (backup) codes serve as one-time passwords that allow a user to validate MFA and regain access.
Administrators can choose a certain number of single-use recovery codes that are displayed immediately after a user has enabled MFA.
Note that they can only be used when the user is connected to the network.
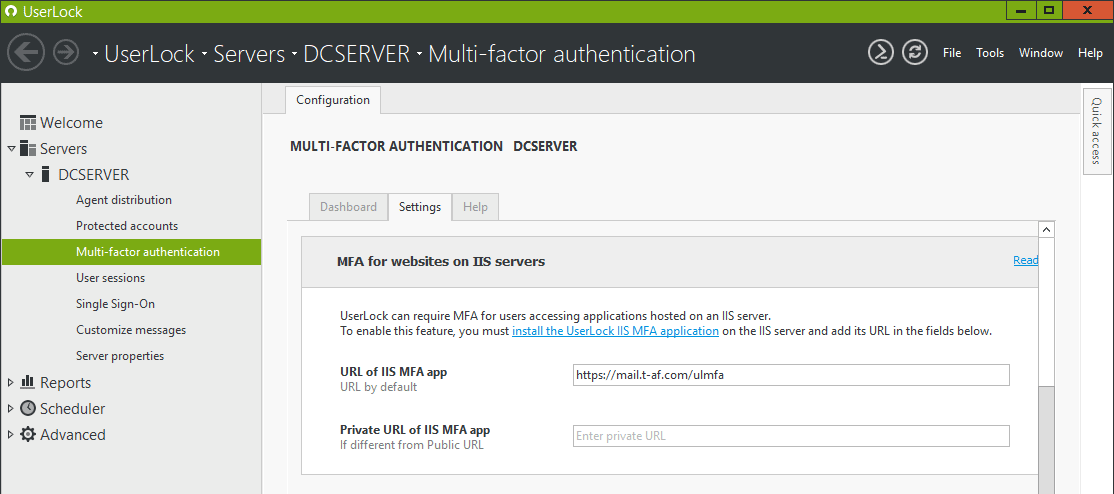
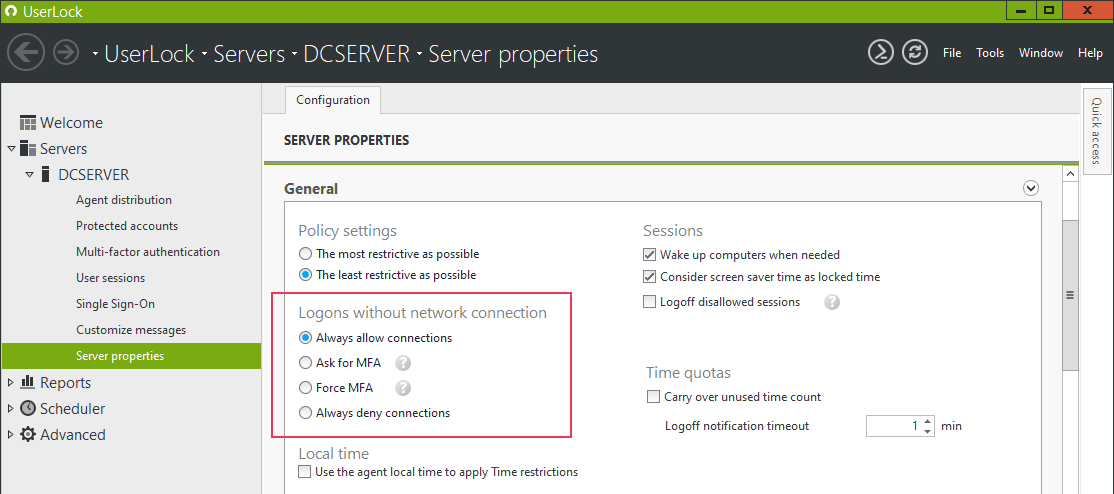
Enforce MFA for logins from any machine without a network connection
UserLock offers a new option to ‘enforce MFA’ on machines without a network connection, i.e. without contact to the UserLock server.
“Force MFA”
This new option will deny logins for users who have not yet enrolled in MFA and authenticated while connected to the network.
The existing option “Ask for MFA – if not configured, allow connection” continues to allow login for users who have not yet enrolled in MFA and authenticated while connected to the network.
Note: MFA enrollment is not possible outside the network
MFA | Alternative methods for multi-factor authentication
With UserLock 11, users can now configure an alternative form of authentication to prevent them from being locked out of the account if a primary method is lost or forgotten.
Administrators can choose to force - or disable - a second method needed. For example, a smartphone authenticator application such as Google Authenticator can be set up alongside a YubiKey hardware token.
MFA | HOTP for machines without network connection
Users can now authenticate with HOTP (HMAC-based one-time password) tokens such as YubiKey without a network connection. Previously only TOTP (Time-based one-time password) tokens were possible without a network connection.
Note: The user must have previously logged on to the machine, while connected to the network
MFA | Using Token2 ALU, NFC and Bio for multi-factor authentication
UserLock now supports the use of Token2 (second-generation: ALU, NFC and Bio) as a second factor authentication. These Token2 T2F2 Security keys are physical tokens using HOTP (HMAC-based one-time password).
MFA | Using VPN with RADIUS Challenge for multi-factor authentication
UserLock’s multi-factor authentication for VPN sessions now supports the Remote Authentication Dial-In User Service (RADIUS) Challenge.
The RADIUS Challenge can prompt for the one time password in a separate second step, after the user has successfully entered their login credentials. VPN solutions that support “RADIUS Challenge” include Open VPN, Palo Alto, Fortinet, Pulse Secure Connect SSL…
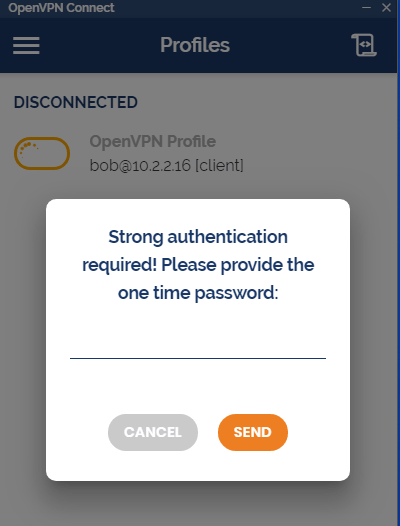
UserLock continues to also support MSCHAP-v2 and PAP authentication. Here users are required to add a comma to the end of the username or password field.
UserLock Anywhere | New web application to better protect remote connections
A new on premise web application for UserLock’s agent/service communication helps ensure UserLock can best protect remote machines.
With the increase in users working remotely, the VPN connection between users and the network is crucial. This new feature allows the UserLock Desktop Agent to communicate with the server through the internet via an IIS application. This will allow UserLock restrictions to continue to be enforced in the event the remote connection through VPN pipes fails.
UserLock Anywhere | Remotely logoff and lock user sessions over the Internet
When enabled this allows contextual restrictions such as logon hours or time quotas to be respected; even if a computer is not connected to the corporate network.