What’s new in UserLock 10
What's new in UserLock 10.2
- MFA for VPN connections
- Offline MFA for users not connected to the network
- IP addresses considered as outside
- Remote Assistance
- Download UserLock
UserLock 10.2
MFA for VPN Connections
Multi-Factor Authentication (MFA) is now available for VPN sessions using Microsoft RRAS (Routing and Remote Access Service) authenticated by the Network Policy Server (NPS).
(Version 10.2 or higher of the UserLock NPS Agent is required)
UserLock supports the use of both MSCHAP-v2 and PAP authentication.
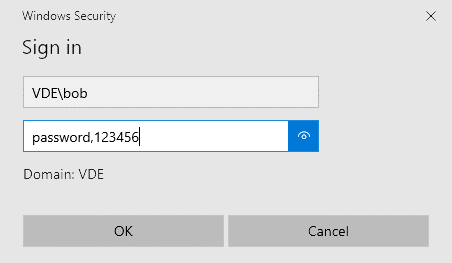
When initiating a VPN connection, users are required to add a comma (“,”) to the end of the username or password field, followed by the MFA code.
We recommend entering the MFA code in the username as it is compatible with MSCHAP-v2 (configured by default) and PAP authentication.
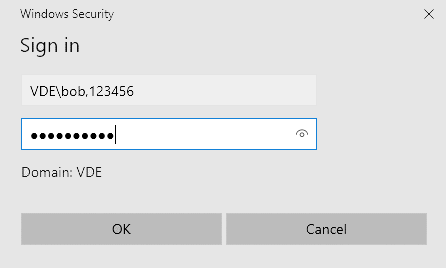
Entering the MFA code in the password is only compatible with PAP authentication.
More information on this use case.
Note: If MFA for VPN is chosen, interactive sessions will also be enabled for MFA. The current version does not allow MFA for only VPN sessions.
Offline MFA for users not connected to the network
Connections from offline machines can now include multi-factor authentication (MFA). This offers further protection to desktop and laptop computer access, when the machine is disconnected from the corporate network.
In addition to requesting MFA, administrators can still choose to always allow or deny offline connections.
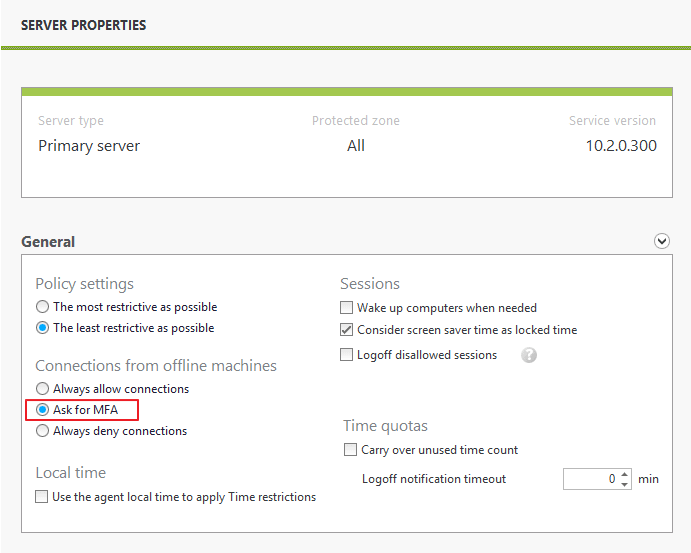
For more details, see the advanced use case "How to manage offline connections".
IP addresses considered as outside
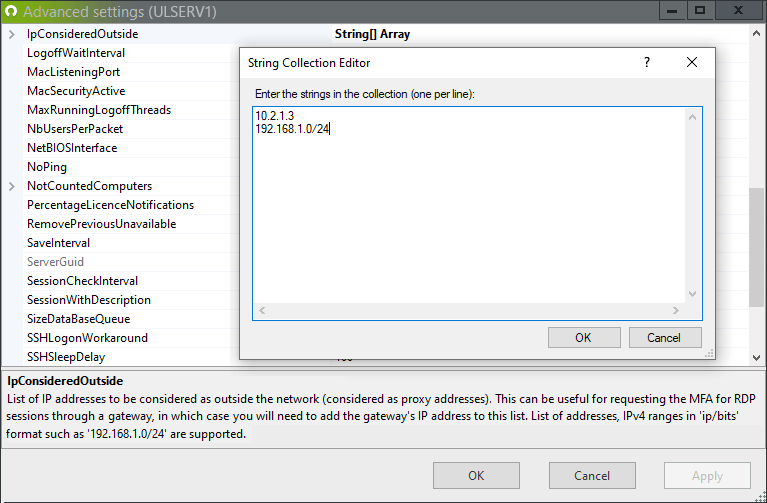
Remote desktop (RDP) connections that pass through a gateway address (RD Gateway, Citrix…) are by default considered as coming from ‘inside the network’. However, for many administrators, these are remote users connecting from outside the corporate network.
To list the IP addresses that should be considered as outside the network, the "IpConsideredOutside" advanced setting (from the UserLock console, press the F7 keyboard key to display the advanced settings dialog box) has been created with the release of UserLock 10.2.
This helps ensure MFA is then enabled on all outside RDP connections – including those through a gateway.
Remote Assistance
The computer command “Remote Assistance” has been added in the ‘Quick access panel’ of User sessions and Agent distribution view.
To be able to use it, the "Remote Assistance" feature must be activated on the computer on which the console is installed (by default, this feature is activated on workstations and deactivated on servers) and "Offer remote Assistance" must be configured in domain policy and allowed in firewalls.
FYI this link explains very well the prerequisites for Remote Assistance.
What's new in UserLock 10.1
- Multi-Factor Authentication (MFA)
- Unlock and Reconnect Management
- Geolocation restriction
- Deny interactive logons if UserLock is inaccessible
- Download UserLock
UserLock 10.1
Multi-Factor Authentication (MFA)
Using YubiKey with UserLock
UserLock MFA now supports YubiKey. This provides an alternative to TOTP authenticator applications or tokens (Token2) since YubiKey use a HMAC-based One-time Password (HOTP) algorithm.
Here is how it works:
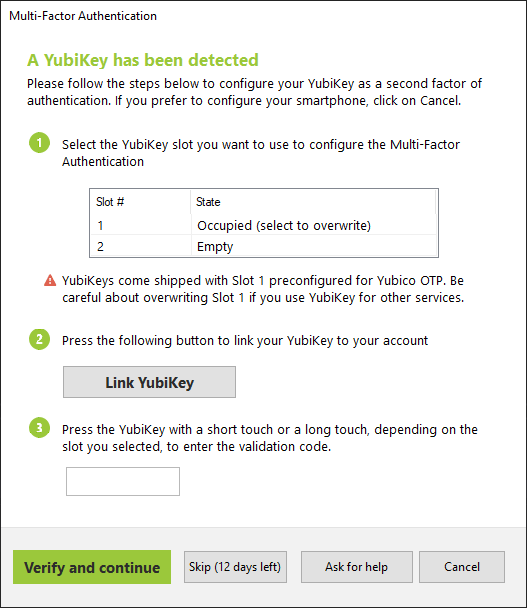
More info about YubiKey: https://www.yubico.com/
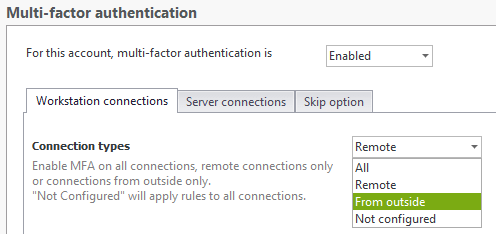
Apply MFA only for Remote Desktop (RDP) logons originating from outside of the network
With the new version of UserLock, you can choose to enable MFA only for RDP logons that originate from outside the local network. The option to apply for every RDP logon remains.
Unlock and Reconnect Management
It is now possible to apply UserLock restrictions - including MFA - when unlocking or reconnecting to a session.
A specific Advanced Setting (press F7 in UserLock desktop console) has been added to disable this new management: ApplyRestrictionsOnUnlock. However, we strongly recommend to keep it enabled as it strengthens your environment security.
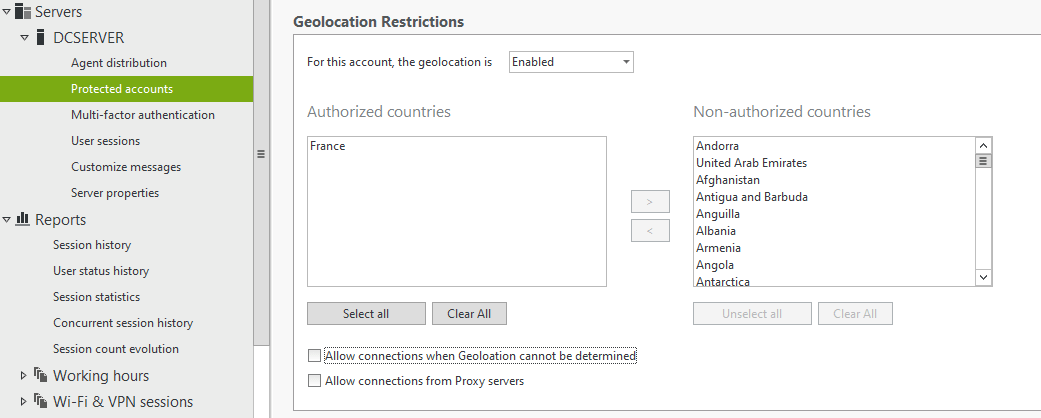
Geolocation restriction
A new contextual restriction is now available in UserLock. The geolocation restriction allows an administrator to restrict remote logons based on location. The restriction will disallow/allow logons from a list of selectable countries.
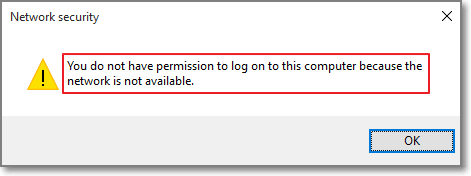
Deny interactive logons if UserLock is inaccessible
UserLock now adds a choice to deny a logon if both the Primary and Backup servers are not available. This stops users from unplugging any network cable and bypassing the protection that UserLock offers.
If UserLock is inaccessible, you can choose to deny interactive connections (logon, unlock and reconnect events) on computers where the Desktop UserLock Agent is installed.
This setting applies to interactive sessions only.
Once UserLock is reachable again, the corresponding session events are sent to the UserLock service. Users will see a notification of this event upon the next successful login, if the welcome message is enabled:
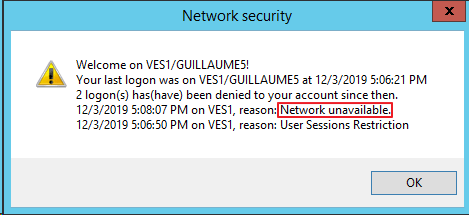
UserLock administrators will see these events in reports, such as logons denied by UserLock for the reason "UserLock inaccessible".
A specific Advanced Setting (press F7 in UserLock desktop console) has been added to enable/disable this new management: DenyInteractiveConnectionsIfUserLockInaccessible.
UserLock 10.0
Multi-Factor Authentication
UserLock allows you to implement MFA in your environment. It is a new restriction that requires a user to authenticate with an additional (second) factor.
UserLock supports MFA through authenticator applications using time-based-one-time-passwords (TOTP). TOTP are widely accepted and aren't easily bypassed like SMS text based authentication. Examples include Google Authenticator and LastPass Authenticator.
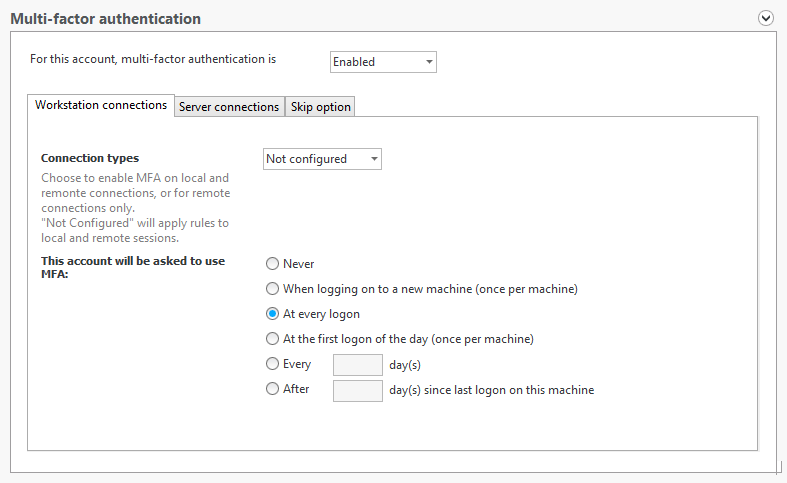
With UserLock 10, administrators can enable MFA for Windows logon and RDP connections to both workstations and/or server connections.
How MFA works
When the user registers a TOTP-supporting device, a unique shared key is created. Both the device and the server can generate a time-based one-time password by processing that key along with the current time. By convention, each TOTP is good for 30 seconds. A user will log in using their regular password, then enter the current one-time password from their device.
Note: The time must be correct and automatically synchronized on the UserLock server. The timezone doesn't affect it.
Deployment
Within UserLock you set a new MFA restriction by user, group or OU.
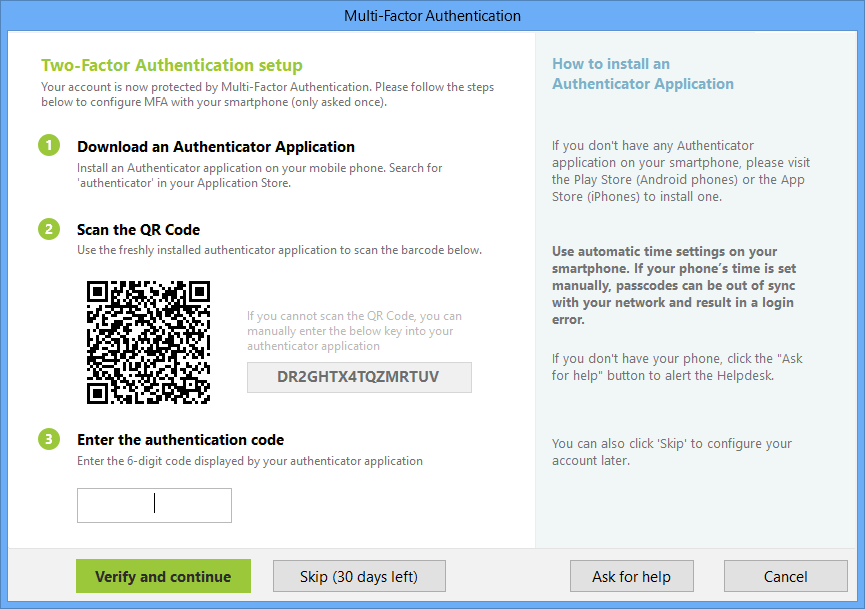
Once the restriction is enabled, the user will be asked to configure this application. Enrollment is intuitive and simple for users to do on their own. They follow a series of simple steps to configure MFA with their smartphone.
- Users will install an authenticator application
- Scan the QR Code that appears at login
- Enter the authentication code
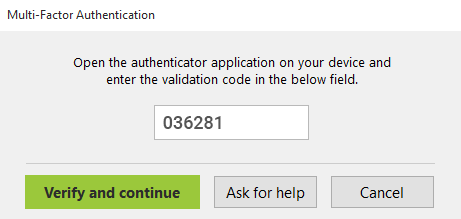
Thereafter, users’ will log in using their normal Active Directory credentials and then when prompted, with a code shown on the app.
A help request can also be added that will immediately notify the administrator by email/popup.
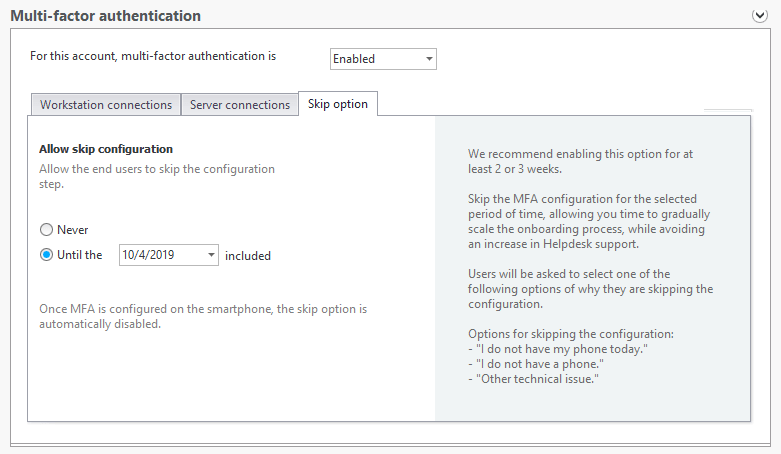
Administrators can also manage the time users have to enroll in MFA with an option to skip configuration. A skip will need ask the user to specify the reason for bypassing MFA configuration.
Customizations for MFA in your environment
With UserLock, administrators can define under what circumstances, MFA is asked for.
- Local logins and/or RDP sessions
- Workstation and/or Server connections
- Frequency
End User messages are also customizable
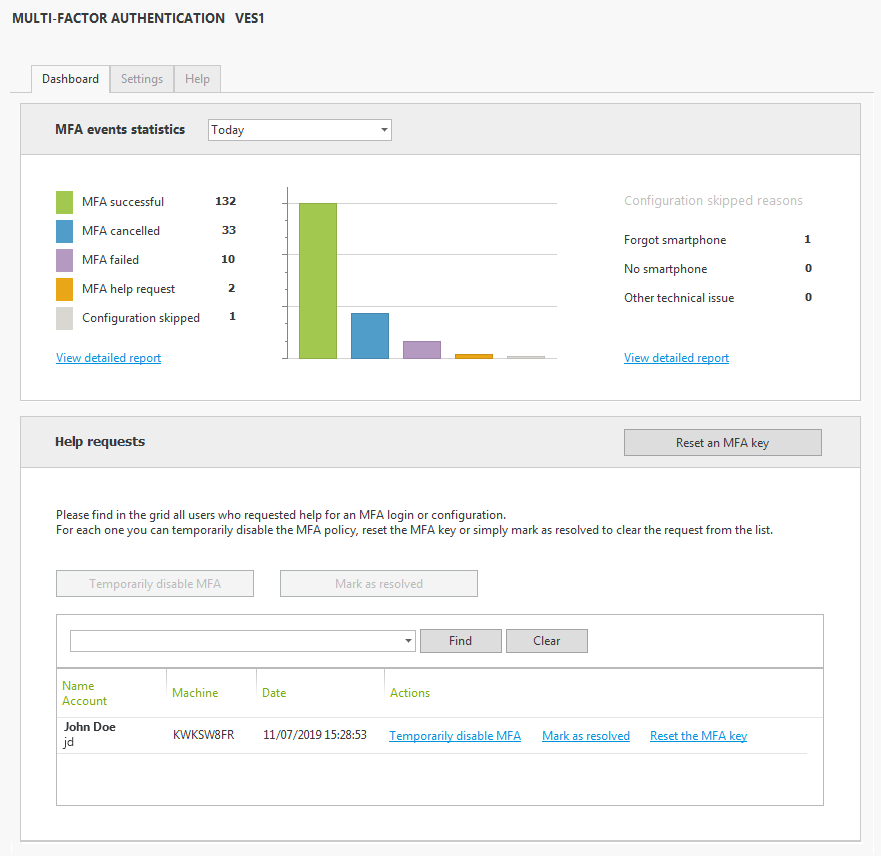
Reporting & Reacting to MFA from the UserLock Dashboard
- Ad-hoc reports are available to manage the use of MFA in your environment.
- Manage real time alerts from user requests for help.
- Reset an MFA key or temporarily disable MFA for a user.