UserLock Frequently Asked Questions
How to clean all UserLock data
Uninstall Agents
Uninstall Desktop Agents
The recommended method is to use the automatic deployer with the "Uninstall" deployment mode. To do this:
Run the UserLock Console.
Browse the "Agent distribution" view:
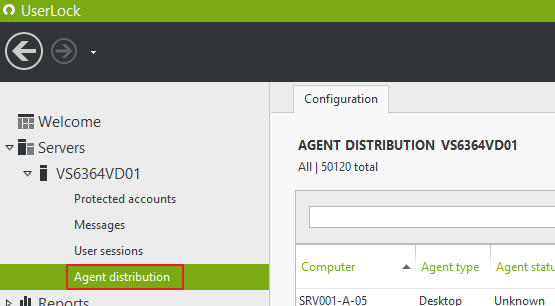
Click on "Properties":
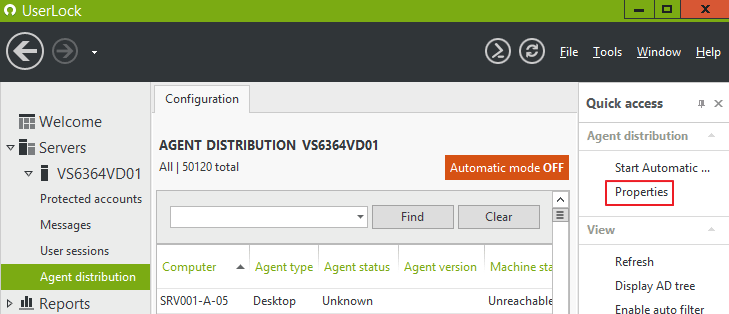
In the "General" section, set the "Distribution" setting to "Undeploy the agent" (learn more), validate through OK:
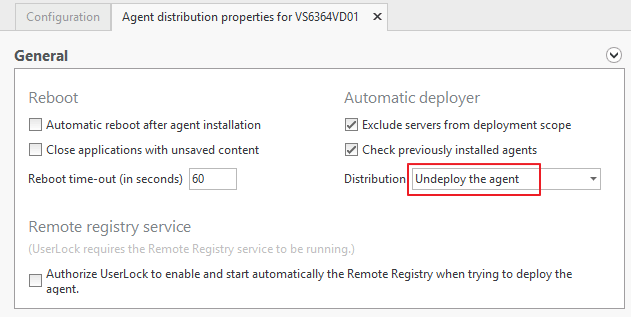
Enable the automatic mode as documented here:
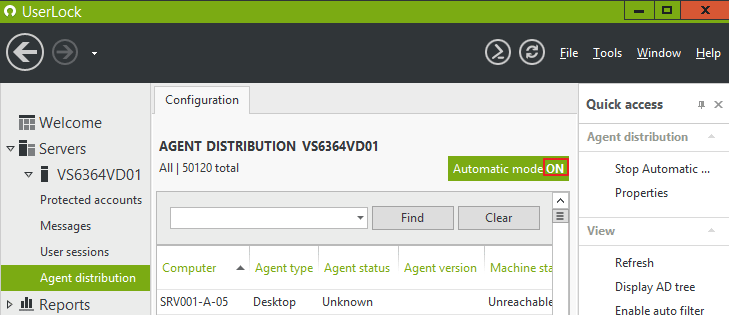
Wait until all Desktop Agents are uninstalled: all computers listed in the "Agent distribution" view should display "Not installed".
Alternatives to uninstall the Desktop Agent:
- Through the console (learn more),
- Manually (learn more - For Mac, see this page).
- Through the MSI technology if you used it for deployment (learn more).
- Through the "Uninstall-UserLockAgent" UserLockPowerShell cmdlet (learn more).
Uninstall NPS Agents
Uninstall all NPS Agents installed. See this page.
Alternatives to uninstall the NPS Agent:
- Manually (learn more).
- Through the "Uninstall-UserLockAgent" UserLockPowerShell cmdlet (learn more).
Uninstall IIS Agents
Uninstall all NPS Agents installed. See this page.
Alternatives to uninstall the IIS Agent:
- Manually (learn more).
- Through the "Uninstall-UserLockAgent" UserLockPowerShell cmdlet (learn more).
Uninstall RRAS Agents
Uninstall all RRAS Agents installed. See this page.
Alternatives to uninstall the RRAS Agent:
- Manually (Learn more).
- Through the "Uninstall-UserLockAgent" UserLockPowerShell cmdlet (learn more).
Uninstall the Backup server (if installed)
Follow the same procedure as in the "Uninstall the Primary server" section.
Uninstall the Primary server
Uninstall the UserLock server using one of the following methods:
- Through the "Programs and Features" Windows component: select "UserLock", then "Uninstall".
- Running the "%ProgramFiles(x86)%\ISDecisions\UserLock\CheckBeforeUninstall.exe" UserLock component. Note that "%ProgramFiles(x86)%\ISDecisions\UserLock\" is the default path for the installation folder of the UserLock package. If the default installation path is not used, here is a way to get it after installation through PowerShell (run PowerShell x64 with the "Run as administrator" option on the UserLock server):
- $userlock = Get-WmiObject Win32_Product | where Name -Like *UserLock*
- $guid = $userlock.IdentifyingNumber
- $installLocationObj = Get-ItemProperty "HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\$guid" -Name InstallLocation
- $installLocation = $installLocationObj.installLocation
- Write-Host $installLocation
Delete remaining files and folders
On all computers where UserLock (including the "Service" component) was installed
Delete the "%ProgramFiles(x86)%\ISDecisions\UserLock\" folder.
Delete the "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\ISDecisions\UserLock" registry key.
Delete the "%ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\" folder.
In EventViewer:
- "Windows Logs" / "Application" log: "UserLock" and "UL2000" event sources.
- "Applications and Services Logs" / "UserLock Admin Actions" log: modification of UserLock configuration: server properties, protected accounts...
On all computers where the Console was installed
Console log file: "%appdata%\ISDecisions\UserLock\Log.txt".
Console configuration: "%appdata%\ISDecisions\UserLock\Default.xml".
Delete the "HKEY_CURRENT_USER\Software\ISDecisions\UserLock" registry key.
On all computers where the Web Console was used
Web Console log file: "C:\ProgramData\ISDecisions\UserLock\Logs\WebConsoleLog.txt".
On all computers where the Desktop Agent was installed
Agent binary file:
- x64 OS and (Vista/Server 2008 or higher) OS: "%windir%\SysWOW64\ULAgentExe.exe".
- x86 OS and (Vista/Server 2008 or higher) OS: "%windir%\System32\ULAgentExe.exe".
- All other cases (XP/Server 2003): "%windir%\System32\ULAgent.dll".
Agent log file:
- x64 OS and (Vista/Server 2008 or higher) OS: "%windir%\SysWOW64\ULAgent.err".
- All other cases: "%windir%\System32\ULAgent.err".
- Virtual store: "%ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\UlAgent-<user login>.err".
Session events not notified live to the UserLock service are temporarily stored in: "%windir%\System32\ULAgent.log".
Program launched for remote logoff and popups binary file:
- x64 OS and (Vista/Server 2008 or higher) OS: "%windir%\SysWOW64\SessionAgent.exe" and "%windir%\SysWOW64\SessionAgentUI.exe".
- All other cases: "%windir%\System32\SessionAgent.exe" and "%windir%\System32\SessionAgentUI.exe".
Program launched for remote logoff and popups log file:
- x64 OS and (Vista/Server 2008 or higher) OS: "%windir%\SysWOW64\SessionAgent.log" and "%windir%\SysWOW64\SessionAgent.log".
- All other cases: "%windir%\System32\SessionAgent.log" and "%windir%\System32\SessionAgentUI.log".
Run "RegEdit", browse the "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" registry key, then delete:
- All registry values beginning with "UserLock" (UserLockCfg, UserLockLastAnalysedEventDate, UserLockLastCheckDate, UserLockServer, UserLockServerBackup, UserLockServerLastUsed, UserLockSessions).
- The "UserLock" sub key (ie the "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\UserLock" registry key).
On all computers where the Mac Agent was installed
Delete the following files:
- /var/log/UserLock.log
- /var/log/UserLock.Auth.log
- /var/log/UserLock.commands_stderr.log
On all computers where the NPS Agent was installed
Agent binary file: "%windir%\System32\ULIasAgent.dll".
Agent log file: "%ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\UlIasAgent.csv".
Delete the "HKEY_LOCAL_MACHINE\SOFTWARE\ISDecisions\UserLock\IAS" registry key.
On all computers where the IIS Agent was installed
Agent binary file:
- HTTP Module: "%windir%\System32\UlHttpModule.dll"
- ISAPI Filter: "%windir%\System32\IisSessions.dll"
Agent log file:
- HTTP Module: %ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\<Application Pool name>.http.txt
- ISAPI Filter: %ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\<HTTP Module name>.isapi.txt
Delete the "HKEY_LOCAL_MACHINE\SOFTWARE\ISDecisions\UserLock\IIS" registry key.
On all computers where the RRAS Agent was installed
Agent binary file: "%windir%\System32\ULRrasAgent.dll".
Agent log file: "%ALLUSERSPROFILE%\ISDecisions\UserLock\Logs\UlRrasAgent.csv".
Delete the "HKEY_LOCAL_MACHINE\SOFTWARE\ISDecisions\UserLock\RAS" registry key.
Special case: For the Desktop UserLock Agent, when UserLock server names are deployed through GPO
See the "Group policy deployment" help page.
Example:
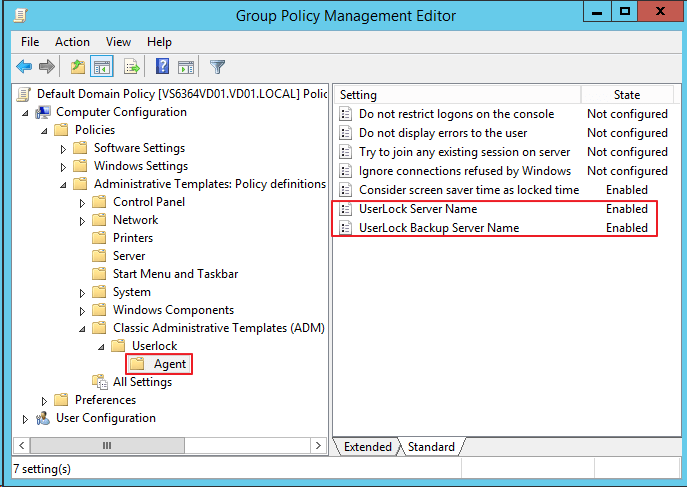
Result (after gpupdate) on a workstation
Full path of the registry key is "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\ISDecisions\UserLock\Agent".
Concerned registry values are:
- "UserLockServerName": name of the Primary UserLock server.
- "BackupServer": name of the Backup UserLock server.
- "LockWhenScreenSaverStart": switch for the Desktop Agent to send a Lock session event when the screen saver starts.
- ...
Example:
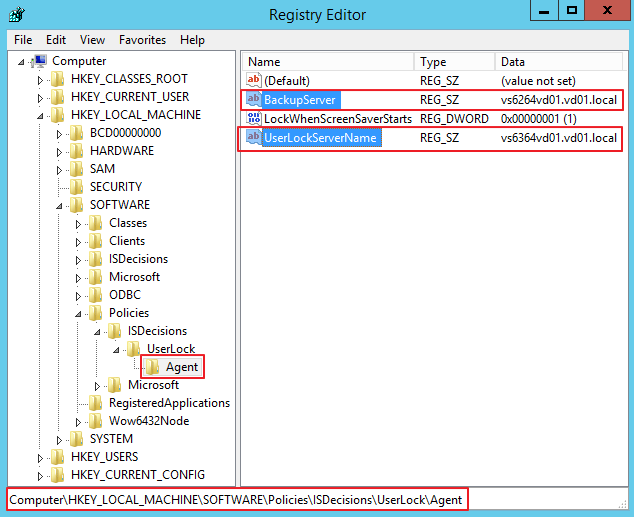
In this case, to remove it, delete GPO settings for UserLock, then update GPO settings on all computers.