What's new in UserLock 9
- Initial access point audit and restriction
- Immediately block all connections for a user
- Restrictions according to machine’s local time zone
- Further risk detection and alerts from specific user activity
- More…
Initial access point audit and restriction
In Version 9, UserLock introduces the concept of an initial access point. Any session which is a new point of
entry to the network will be considered as the initial access point for the user initiating the connection. UserLock
can analyze users new connections to detect if this is a new point of entry in the network or a connection performed
from an existing session.
Consider the following scenario of user connections to a network protected by UserLock:
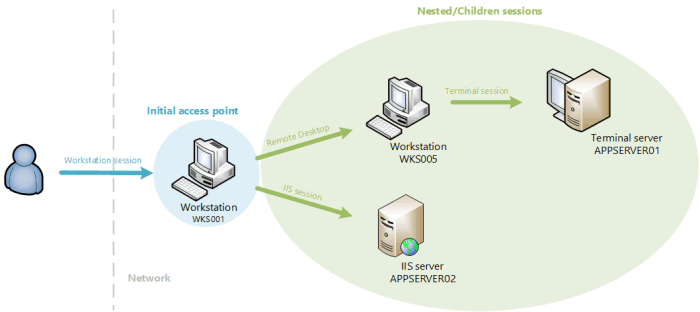
UserLock now has the ability to analyze what is the sequence of the user connections to determine from which initial access point the user enters the network. The result is displayed in real time in the ‘User sessions’ view through two new columns differentiating initial access point and children/nested sessions.
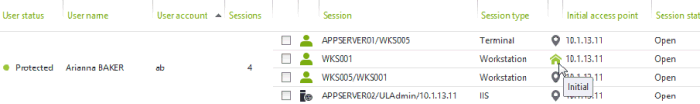
New icons tag sessions to indicate if they are an initial access point or a nested session:
-
 The corresponding
session is an initial access point of the user (entry point in the network).
The corresponding
session is an initial access point of the user (entry point in the network).
-
 The corresponding session is not an initial access point
and has been opened from an existing parent session.
The corresponding session is not an initial access point
and has been opened from an existing parent session.
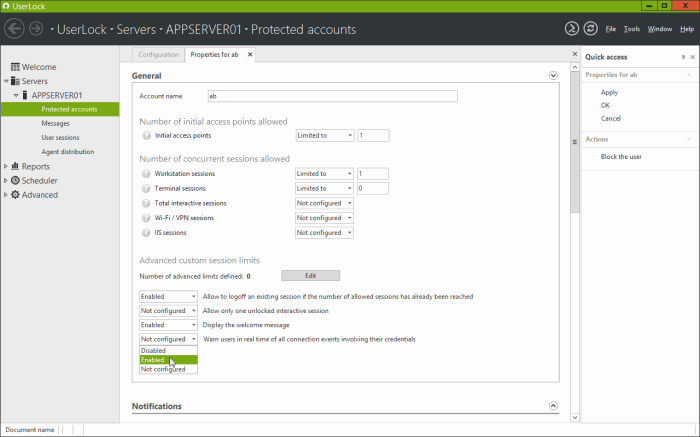
You can limit the number of initial access points to ensure that a user will have a single point of entry in the network. In that case,
a user already connected to a workstation won’t be able to open any connection from another location in the network. Only a new
connection from his current workstation will be authorized.
Then to go further, you can choose from an initial access point,
which types and how many nested/children sessions a user can open.
Immediately block all connections for a user
For any specific user, you can block all logon attempts and close all existing sessions remotely, to react quickly to compromised or suspected compromised credentials. Just select the user from the ‘User sessions’ view and click on ‘Block the user’.
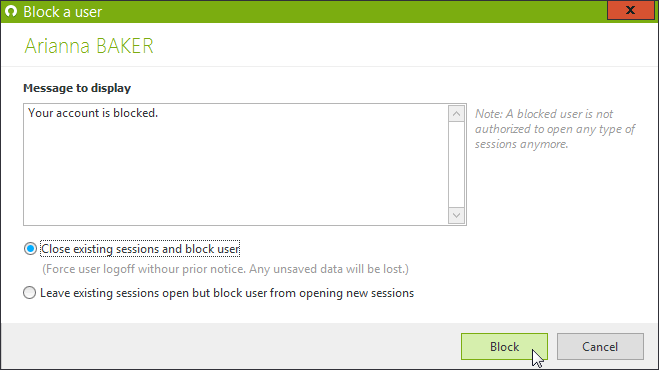
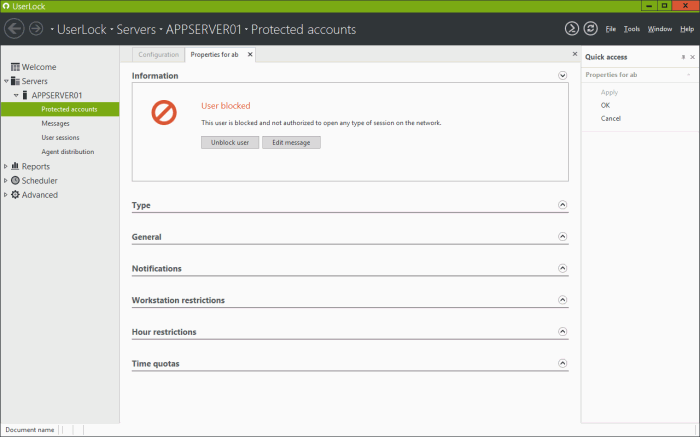
Until the user is unblocked, all connection attempts will be denied.
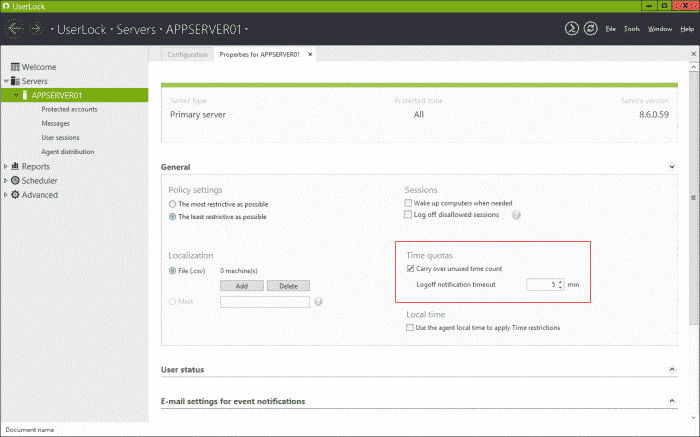
Restrictions according to machine’s local time zone
If UserLock monitors and protects machines from different time zones, a new option allows you now to apply the time restrictions according to
each client machine’s time instead of the UserLock server time.
This option is enabled with a simple check box in the ‘Properties’ view
of the UserLock server.
Further risk detection and alerts from specific user activity
UserLock can now detect, alert and display as ‘high risk’ behavior when a user has simultaneous connections from inside and outside the local network (private and public IP address), which is in many cases an abnormal situation.
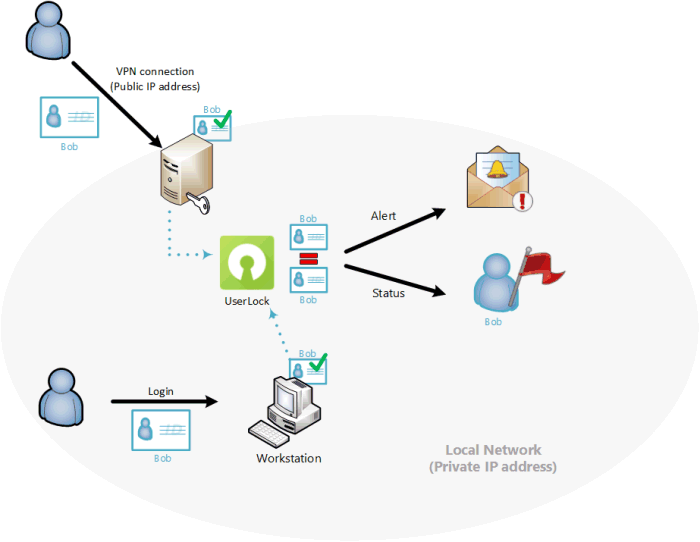
Example of a user owning a Workstation session in the local network while a VPN connection is open from outside.
In the same way, UserLock can now detect, alert and display as a ‘risk’ situation, users opening a new session from an existing session with different credentials.
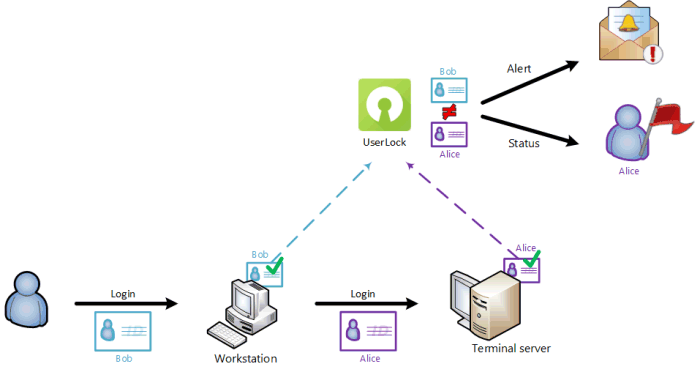
Example of a user opening a Terminal session from a Workstation session impersonating with valid but different credentials.
More...
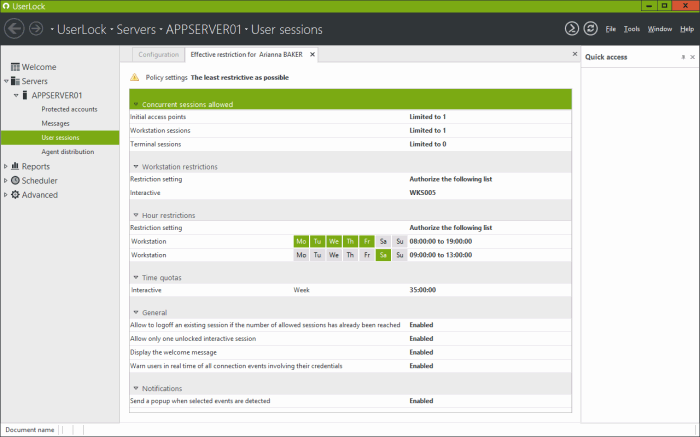
- The UserLock interface can now display a view ‘Effective restrictions’ to easily check which restrictions are applied to a specific user. On previous version it was necessary to iterate over all protected groups to check if a user was a member or not, and what restrictions were applied. Now you just need to right click on the username from the ‘User sessions’ view to display what restrictions are applied.
-
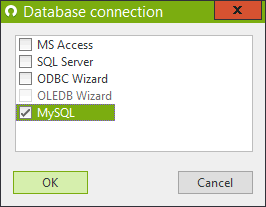
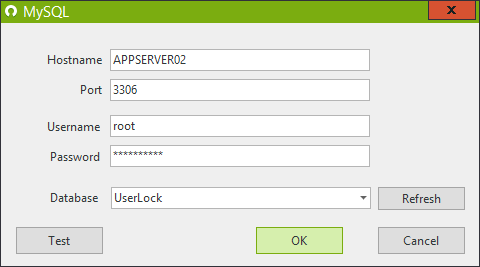
The UserLock database connection builder now supports MySQL database system 5.6 and newer versions.
- All kinds of sessions are now displayed in the session view by machine. Previously only interactive sessions were displayed.
- The ability to filter history reports according to a machine organizational unit.
- The ability to display the ‘Session count evolution’ report for all computers with a name matching a wildcard pattern.