How to apply MFA for VPN
Two methods are available in order to secure VPN sessions with UserLock:
-
RADIUS Challenge
If your VPN client supports Radius Challenge, this method is recommended to provide the best user experience. The user will be prompted to enter the OTP code in a second step after providing their credentials. -
VPN/MFA using RRAS method
Users can receive a push notification or enter a OTP password in the user name or password field to authenticate with MFA for VPN connections.
For a better UI experience for the user to authenticate with MFA, users can install the VPN connect tool. Click here for instructions.
Pre-requisites
- A Network Policy Server (NPS) with the latest UserLock NPS agent installed (at least Version 10.3 for RRAS and Version 11.0 for RADIUS)
- For RADIUS Challenge: VPN connections managed by a VPN server solution supporting RADIUS challenge for which the RADIUS authentication and RADIUS accounting are configured to use the NPS server. The authentication protocol to use is PAP.
- For RRAS method: VPN connections managed by Microsoft Routing and Remote Access Service (RRAS)
To enable MFA for VPN connections, the users must:
- belong to a pre-defined Active Directory group
- belong to a protected account to which MFA has been applied
- have previously logged on to the network using MFA
1. VPN/MFA using RADIUS Challenge
The following is a list of VPN solutions that support the Radius Challenge that have been verified by our team. Check with your VPN solution to see if they are compatible.
- OpenVPN
- Palo Alto
- Fortinet
- Pulse Secure Connect Secure SSL
- To enable RADIUS Challenge, go to the advanced settings by pressing F7 in the UserLock console, and change the setting "MfaVpnChallenge" to True.
This setting will apply to all VPN connections of users protected by UserLock MFA.
NOTE: If you have activated MFA Push method:
UserLock will wait for the Push validation for 5 minutes by default. If the time has expired a challenge will be sent to the VPN client and the user will prompted to enter a TOTP or HOTP code.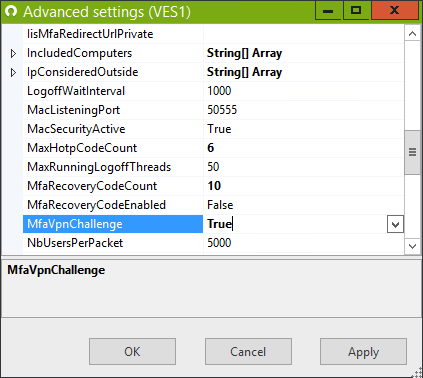
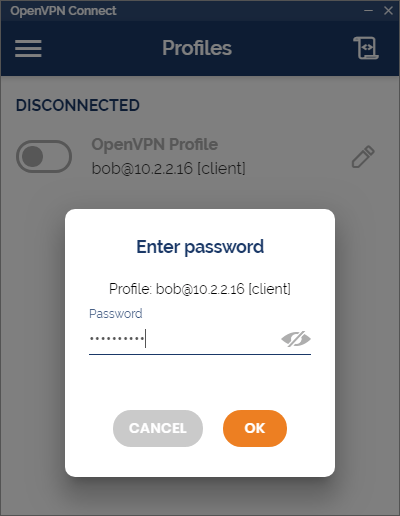
- In this example, we are using the RADIUS Challenge for OpenVPN. When the user connects to VPN, they will first be prompted to enter their password.
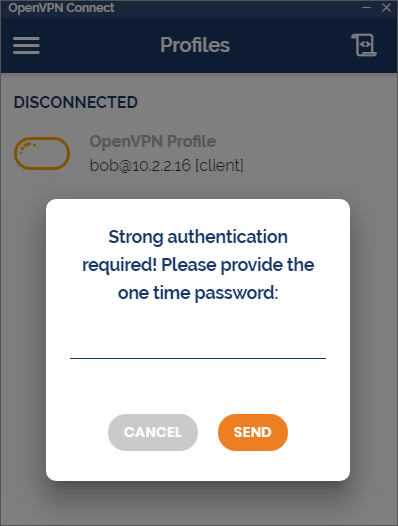
- In the next step, the user will be prompted to enter their OTP code to authenticate with MFA.
2. VPN/MFA using RRAS method
MFA for VPN using MSCHAP-v2 by entering the MFA code in the username field
Configuration
-
At the NPS Server, ensure that an active valid policy is in place that grants VPN access to the required users.
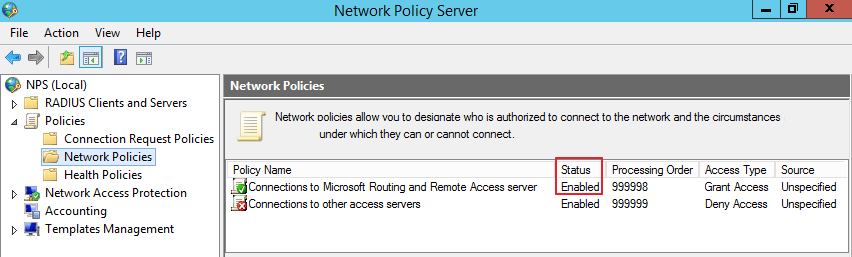
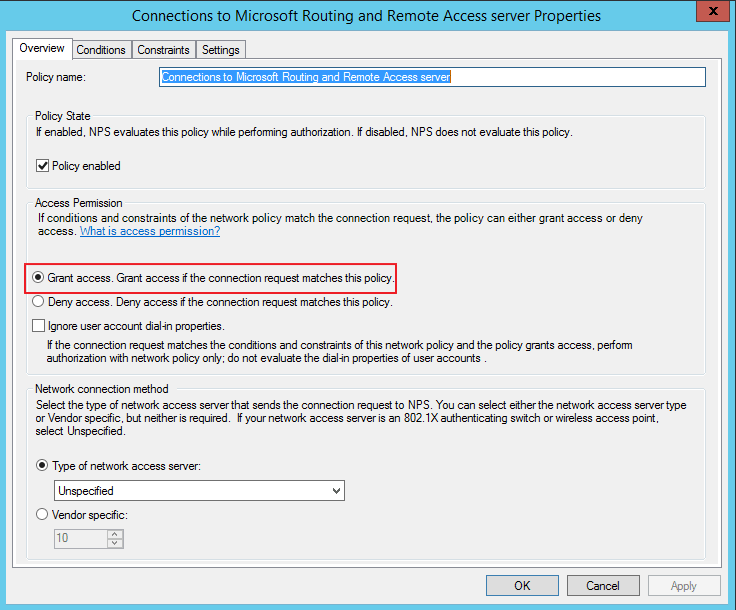
-
In the « Conditions » section add the windows Active Directory group to which authorized VPN users belong
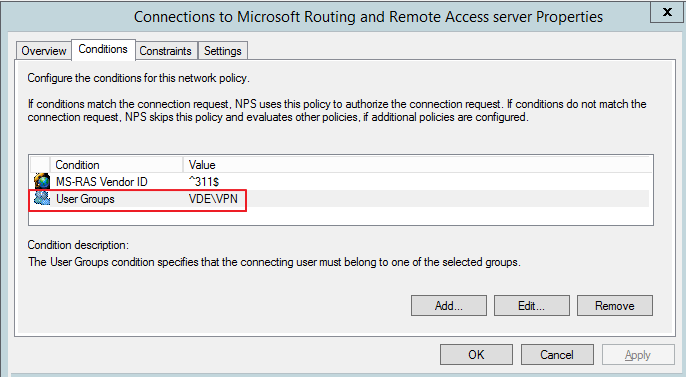
-
In order to connect at the client level ensure the following :
- VPN connection type is set to “Automatic”
- MS-CHAP v2 authentication method is selected
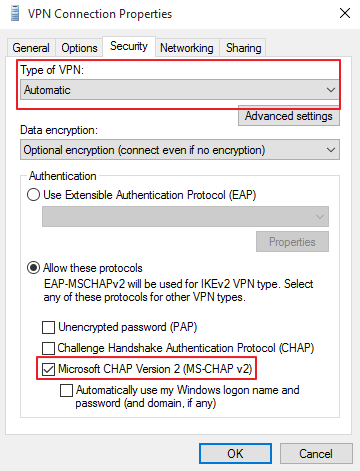
MFA for VPN connections for end users
When a user with MFA enabled connects to a VPN session, they will be required to enter the MFA code when entering their username and password.
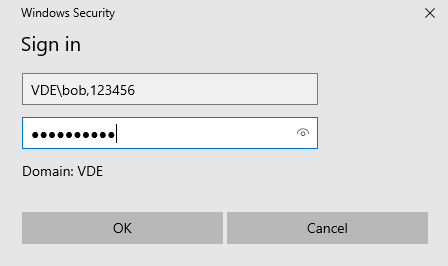
The user will need to enter the MFA code displayed in the authentication app or programmable token in the user name field, using the format:
Username : <Domain>\<username>,<MFA code>
For YubiKey users, they will need to type the comma, and then press on the YubiKey to enter the code.
In the example below, here are the requirements for a typical user
Domain = VDE
Username = Bob
MFA code = 123456
NOTE:
In the user field, a comma «,» is required to separate the username and MFA code.
Since the MFA code changes periodically, it is recommended to enter the password initially and then return to the previous field so that the MFA code is entered lastly.
Alternative method using PAP authentication by entering the MFA code in the password field
It is possible to use the authentication Password Authentication Protocol (PAP) in order to use VPN/MFA.
If this method is used with L2TP or SSTP the communications are encrypted at the time of authentication.
NOTE: This method should not be used with PPTP.
Configuration
-
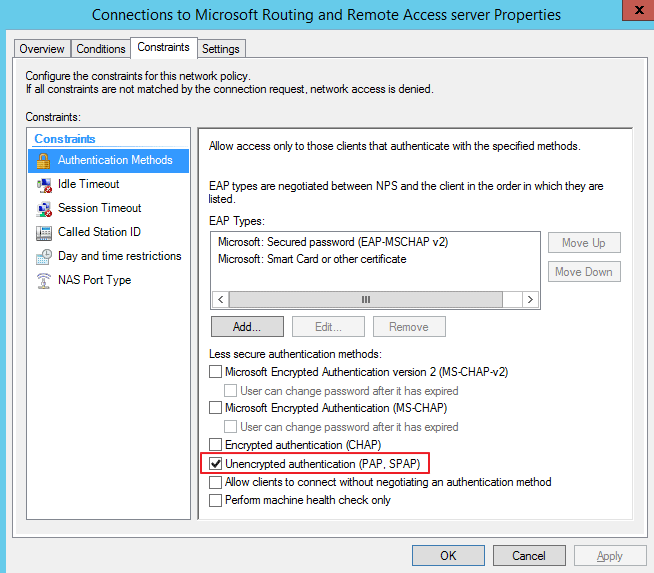
On the NPS Server, ensure that the unencrypted authentication method is solely selected (PAP, SPAP)
-
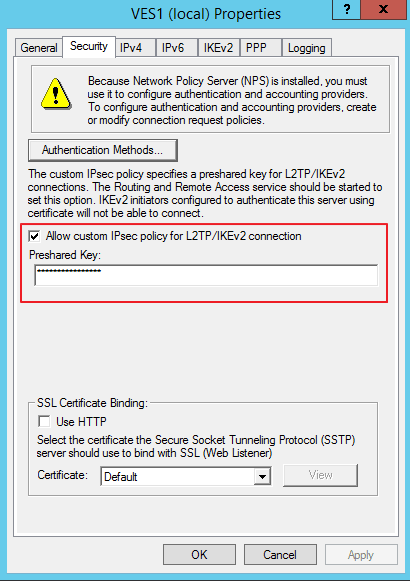
On the Routing and Remote Access Server level ensure that a preshared key has been configured for L2TP connections:
-
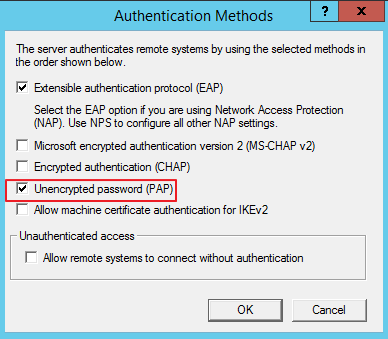
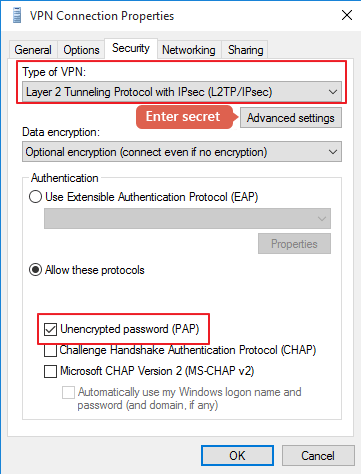
Ensure that the Unencrypted password (PAP) authentication method is selected
-
At the VPN client level ensure that:
- VPN connection type is set to L2TP with IPSec
- Enter the preshared secret key that was preconfigured in RRAS
- Set authentication method to PAP
MFA for VPN connections for end users
When a user with MFA enabled connects to a VPN session, they will be required to enter the MFA code when entering their username and password.
The user will need to enter the MFA code displayed in the authentication app in the password field, after the password, separated by a comma “,”. For YubiKey users, they will need to type the comma, and then press on the YubiKey to enter the code.
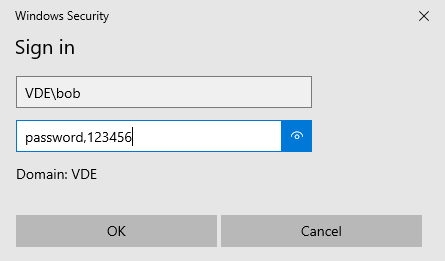
In the user name field: <Domain>\<username>
In the password field: <password>,<MFA code>
In the example below, here are the requirements for a typical user
Domain = VDE
Username = Bob
Password = password
MFA code = 123456
If you use MFA Push for VPN RRAS
The VPN client timeout and the VPN server RADIUS timeout should be configured with a greater value than the MFA push timeout in UserLock.
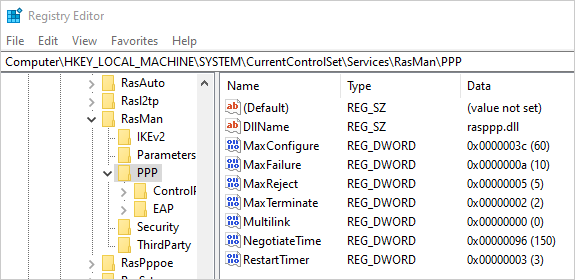
For the Microsoft client VPN the timeout is configured with the following registry value:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\PPP\MaxConfigure = (REG_DWORD)Timeout in s (default value 10 s)
For RRAS the RADIUS timeout is configured in the RADIUS server configuration
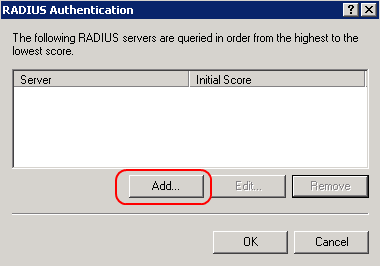
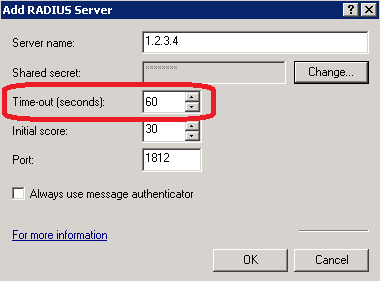
If the NPS server is installed locally it cannot be changed in the RRAS administration console.
Limitations
Once you have configured MFA for VPN sessions, users will be prompted to enter their credentials when accessing shared folders through VPN.
As a workaround, it is possible to avoid this prompt if the client machine is member of the Active Directory by carrying out the following procedure:
On the host machine used for the VPN connection navigate to the following location:
"%USERPROFILE%\AppData\Roaming\Microsoft\Network\Connections\Pbk"
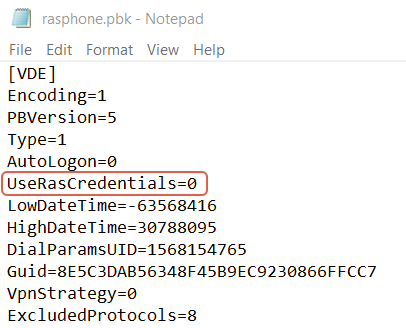
Edit the file “rasphone.pbk”
For the section related to the VPN connection that is used, ensure that the following value is set:
UseRasCredentials=0