Accounts
FileAudit scans the Microsoft Security logs of the audited machine in real-time to capture all access events. By default, the credentials used to connect and scan the machine log are those defined in the FileAudit service.
This scan process requires at least local administrator privileges on the target machine. If the credentials of the service are not sufficient to activate the scan, you can define impersonation accounts to use instead of FileAudit service credentials. If you have defined several audit paths targeting different machines, you can enter an account for each machine in the ‘Accounts’ tab.
Click ‘Add an account’ and provide the correct credentials:
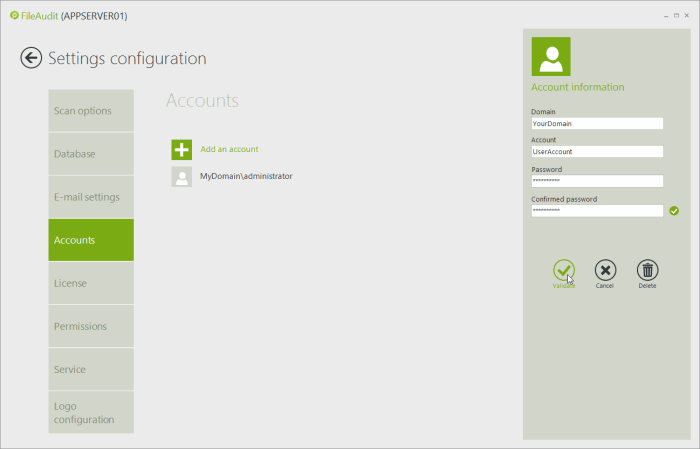
Please note that the Fileaudit service requires that the impersonation account added in the FileAudit console should be part of the local “Log on as a Batch job” policy.
By default, domain administrator accounts (“Administrators”) are part of this policy and it is therefore not necessary to modify this policy using a domain administrator account under normal circumstances, but it may sometimes be necessary to manually add the impersonation account configured in this policy because the permissions linked to this policy have been modified.