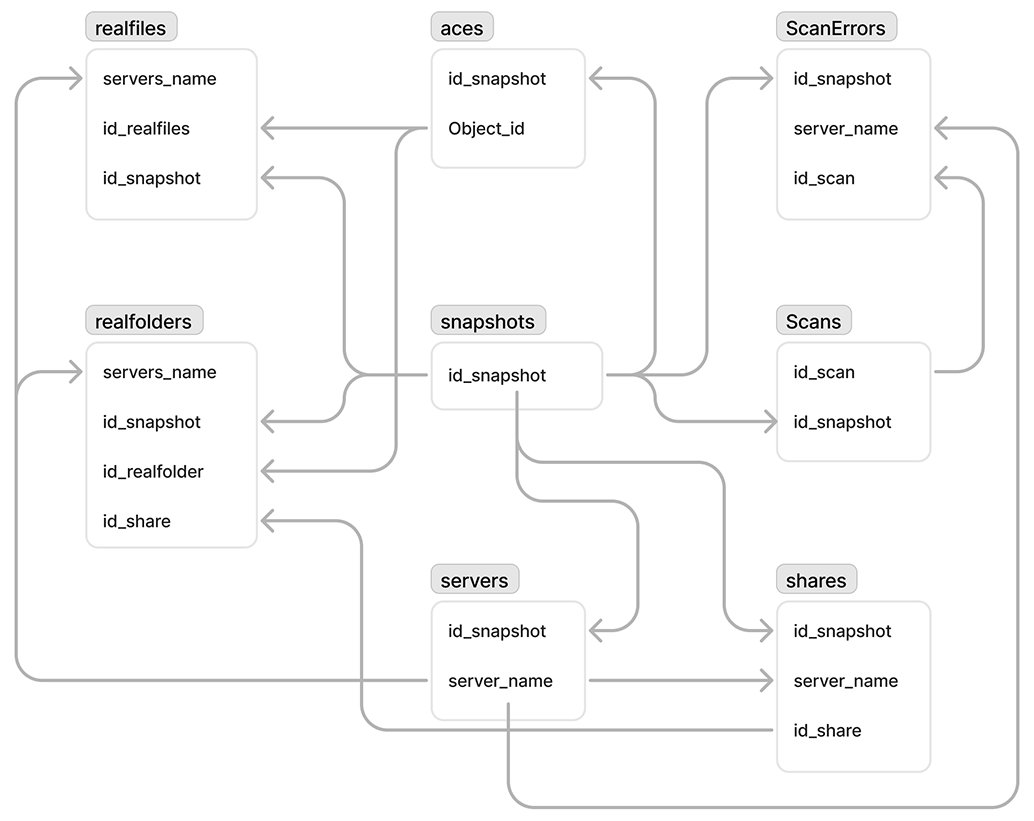
Database reference
- FA_Events table
- FA_LastEvents table
- FA_ALERT
- SNAPSHOTS
- REALFILES
- REALFOLDERS
- ACES
- SCANERRORS
- SERVERS
- Schema
FA_Events table.
The FileAudit database contains two tables. The first table is named FA_Events. The following fields are available in the table:
|
Name |
Type |
Description |
|
Computer |
String |
NetBIOS name of the computer where the audited file/folder is located. |
|
FileName |
String |
Path of the audited file/folder. |
|
UserAccount |
String |
User account that accessed the file/folder. |
|
DomainName |
String |
Domain of the user account that accessed the file/folder. |
|
Process |
String |
Process used to access the file/folder. This field is only available if the access is made locally. |
|
Accepted |
Number |
1 = Allowed / 0 = Rejected |
|
AccessRights |
Number |
Rights used to access the file/folder. See Appendix 1. |
|
Privileges |
Number |
Privileges used to access the file/folder. See Appendix 2. |
|
AccessId |
Number |
Access operation determined by FileAudit. See Appendix 3. |
|
RecordNumber |
Number |
Event record number in the Microsoft Windows Security log. |
|
EventTime |
DateTime |
Local Date & time of the file/folder access. |
|
EventLocalTime |
DateTime |
Field to ignore. Do not use. |
|
ObjectType |
Number |
0 = Unknown / 1 = Folder / 2 = File |
|
ClientAddress |
String |
Client IP address from where the access has been performed. This field is only available if the access is made remotely. |
|
LogonId |
String |
Logon ID of the user access token used to access the file/folder. |
|
Id |
Number |
Primary key automatically incremented for every new record. |
|
ClientName |
String |
Client machine name from where the access has been performed. This field is only available if the ClientAddress field exists. |
|
UniqueId |
String |
Unique identifier per access event |
|
OldFileName |
String |
Precedent file/folder path before a move or rename. This field is only available for cloud objects. |
|
FileUniqueId |
String |
Unique identifier per file/folder, this does not change with a move or rename action. This field is only available for cloud objects. |
|
NewFileName |
String |
New path after a move or rename |
|
OldSd |
String |
The security descriptor of the object before the permissions changes event occurred |
|
NewSd |
String |
The security descriptor of the object after the permissions changes event occurred |
FA_LastEvents table.
This second table is used internally by FileAudit to know which events have not yet been scanned. This allows FileAudit to scan only new events.
|
Name |
Type |
Description |
|
Computer |
String |
NetBIOS name of the computer where the audited file/folder is located. |
|
RecordNumber |
Number |
Event record number of the last event scanned by FileAudit from Microsoft Windows Security log. |
|
EventTime |
DateTime |
Date and time (UTC) of the last event scanned by FileAudit from Microsoft Windows Security log. |
Appendix 1 - AccessRights
AccessRights field is a combination of bits described in the grid as follows.
To exploit this specific field, you need to do a bit of extraction.
|
Bit |
Flag |
Description |
|
0 |
FILE_READ_DATA |
List folder / read data |
|
1 |
FILE_WRITE_DATA |
Create files / write data |
|
2 |
FILE_APPEND_DATA |
Create folders / append data |
|
3 |
FILE_READ_EA |
Read extended attributes |
|
4 |
FILE_FILE_WRITE_EA |
Write extended attributes |
|
5 |
FILE_EXECUTE |
Traverse folder / execute file |
|
7 |
FILE_READ_ATTRIBUTES |
Read attributes |
|
8 |
FILE_WRITE_ATTRIBUTES |
Write attributes |
|
16 |
DELETE |
Delete |
|
17 |
READ_CONTROL |
Read permissions |
|
18 |
WRITE_DAC |
Change permissions |
|
19 |
WRITE_OWNER |
Take ownership |
|
20 |
SYNCHRONIZE |
|
|
24 |
ACCESS_SYSTEM_SECURITY |
Appendix 2 - Privileges
|
Bit |
Privilege |
Description |
|
5 |
SeSecurityPrivilege |
|
|
6 |
SeTakeOwnershipPrivilege |
|
|
14 |
SeBackupPrivilege |
|
|
15 |
SeRestorePrivilege |
Appendix 3 - AccessId
|
Identifier |
Operation |
Description |
|
0 |
Delete |
The file/folder was deleted, moved or renamed. |
|
1 |
Ownership |
A user took the ownership on this file/folder. |
|
2 |
Permissions |
A user changed permissions on this file/folder. |
|
3 |
Write |
The file was opened in write mode. |
|
4 |
Execute |
The file is an executable and was executed by a user. |
|
5 |
Read |
The file was opened in read mode |
|
6 |
System |
An attempt was made to read or write the system access control list of the file/folder. Typically this event just means that a user displayed properties on the file/folder using the Windows Explorer. |
|
7 |
Write Attributes |
A file attribute has been changed. |
|
8 |
Other |
|
|
9 |
Creation (Cloud) |
The file was created |
|
10 |
Move |
The file was moved |
|
11 |
Rename |
The file was renamed |
|
12 |
Lock (Cloud) |
|
|
13 |
Unlock (Cloud) |
|
|
14 |
Copy (Cloud) |
The file was copied |
|
15 |
Download (Cloud) |
The file was downloaded |
|
16 |
Restore (Cloud) |
The file was restored |
|
17 |
Revert (Cloud) |
The file was reverted |
|
18 |
Share (Cloud) |
The file was shared |
|
19 |
Unshare (Cloud) |
The file was unshared |
|
20 |
Check In (Cloud) |
A user checked in a file in Sharepoint Online |
|
21 |
Check Out (Cloud) |
A user tried to checked out a file in Sharepoint Online |
|
22 |
Undo Check Out (Cloud) |
A user discarded a check out of a file in Sharepoint Online |
|
23 |
Destroy (Cloud) |
The file was deleted from trash |
FA_ALERT
This table provide a history with all of the alerts triggered by FileAudit ”Alerts” feature.
|
Field name |
Data type |
Description |
|
AlertType |
number |
Type of the alert (Single or mass alert) |
|
AlertTime |
Datetime |
Time when the alert has been triggered |
|
Status |
number |
Access status (Granted/Denied) |
|
AlertName |
string |
Name of the alert |
|
ServerName |
string |
Name of the server where the alert has been triggered |
|
DomainName |
string |
Domain of the user account that accessed the file/folder |
|
UserName |
string |
Name of the user that accessed the file/folder |
|
Path |
string |
Path(s) of the file(s)/folder(s) where the alert has been triggered |
|
ClientName |
string |
Client machine name from where the alert has been triggered |
|
ClientAddress |
string |
List of clients IP addresses from where the alert has been triggered |
|
AccessType |
number |
List of access types that triggered the alert |
|
MailRecipient |
string |
List of e-mail recipients who have received a notification that the alert has been triggered |
|
Script |
string |
The list of script(s) name(s) executed by the alert |
|
Process |
string |
Process’s name that triggered the alert |
|
EffectiveCount |
number |
Number of events that have been detected to trigger the alert in the case of a mass alert |
|
EffectiveTimePeriodInSec |
number |
Effective time period between the first and the last event that triggered the alert in the case of a mass alert |
SNAPSHOTS
This table lists all the network images available in the database. Each image is identified by the "id_snapshot" field.
|
Field name |
Data type |
Description |
|
id_snapshot |
number |
Identifier of the network snapshot. |
|
shot_time |
datetime |
Time when the scan of the snapshot began. |
|
config_file |
string |
|
|
description |
string |
REALFILES
This table describes all files available on your Windows computers (or a subset if you define file masks or folder restrictions).
|
Field name |
Data type |
Description |
|
Id_realfiles |
number |
Identifier of this file. |
|
server_name |
string |
Name or network address of the related computer |
|
id_snapshot |
number |
Snapshot auto-number. |
|
pathname |
string |
Full path of the file. |
|
filename |
string |
|
|
attribs |
number |
Bit mask specifying the file's attributes (see Appendix) |
|
realsize |
number |
Real size of the file. |
|
compressedsize |
number |
Compressed size of the file. |
|
time_created |
datetime |
Time when the file was created. |
|
time_modified |
datetime |
|
|
time_accessed |
datetime |
|
|
account_name |
string |
Owner of the file. |
|
id_Acl |
number |
Appendix
|
Symbolic constant |
Value |
Meaning |
|
FILE_ATTRIBUTE_ARCHIVE |
0x00000020 |
The file or directory is an archived file or directory. Applications use this attribute to mark files for backup or removal. |
|
FILE_ATTRIBUTE_COMPRESSED |
0x00000800 |
The file or directory is compressed. For a file, this means that the file is compressed. For a directory, this means that compression is the default for newly created files and subdirectories. |
|
FILE_ATTRIBUTE_DIRECTORY |
0x00000010 |
The handle identifies a directory. |
|
FILE_ATTRIBUTE_ENCRYPTED |
0x00000040 |
The file or directory is encrypted. For a file, this means that data in the file is encrypted. For a directory, this means that encryption is the default for newly created files and subdirectories. |
|
FILE_ATTRIBUTE_HIDDEN |
0x00000002 |
The file or directory is hidden. It is not included in an ordinary directory listing. |
|
FILE_ATTRIBUTE_NORMAL |
0x00000080 |
The file or directory has no other attributes set. This attribute is valid only if used alone. |
|
FILE_ATTRIBUTE_OFFLINE |
0x00001000 |
The file data is not immediately available. Indicates that the file data has been physically moved to offline storage. |
|
FILE_ATTRIBUTE_READONLY |
0x00000001 |
The file or directory is read-only. Applications can read the file but cannot write to it or delete it. If this is a directory, applications cannot delete it. |
|
FILE_ATTRIBUTE_REPARSE_POINT |
0x00000400 |
The file has an associated reparse point. |
|
FILE_ATTRIBUTE_SPARSE_FILE |
0x00000200 |
The file is a sparse file. |
|
FILE_ATTRIBUTE_SYSTEM |
0x00000004 |
The file or directory is part of the operating system or is used exclusively by the operating system. |
|
FILE_ATTRIBUTE_TEMPORARY |
0x00000100 |
The file is being used for temporary storage. File systems attempt to keep all of the data in memory for a quicker access, rather than flushing it back to mass storage. A temporary file should be deleted by the application as soon as it is no longer needed. |
REALFOLDERS
This table describes all folders available on your Windows computers (or a subset).
|
Field name |
Data type |
Description |
|
id_snapshot |
number |
snapshot auto-number |
|
server_name |
string |
Netbios name of the server without the 2 backslashes. |
|
id_realfolder |
number |
Identifier of this folder. The field is used to link tables such as aces\object_id |
|
id_share |
number |
Link to the share if the folder is shared (shares table). |
|
pathname |
string |
Full path of the folder. |
|
foldername |
string |
Name of the folder |
|
attribs |
number |
Bit mask specifying the folder's attributes (see Appendix in table realfiles). |
|
time_created |
time |
Time when the folder was created. |
|
account_name |
string |
Owner of the file. |
|
realsize |
number |
Size of the folder including al subdirectories and files (Bytes) |
|
compressedsize |
number |
Currently not scanned |
|
NbFiles |
number |
Number of files in the folder |
|
NbFolders |
number |
Number of subfolders in the folder |
|
time_accessed |
time |
Last accessing time. |
|
rootsize |
number |
Size of all files at the root of the folder |
|
id_Acl |
number |
|
|
id_scan |
number |
ACES
This table contains the ACEs (access control entries) of the total scanned objects (files).
|
Field name |
Data type |
Description |
|
id_snapshot |
number |
auto-numbering of network snapshots. |
|
object_id |
number |
Identifier of a file (see "realfiles") or a share (see "shares"). |
|
type |
number |
Type of access (can be: ACCESS_ALLOWED_ACE_TYPE = 1 or ACCESS_DENIED_ACE_TYPE = 0). |
|
rightmask |
number |
Bit mask describing the type of access: allowed or denied (see Appendix). |
|
aceflags |
number |
|
|
account_name |
string |
Full account name corresponding to the ACE. |
|
Rights |
string |
rwxd read write execute delete access rights |
Appendix
|
Bits |
Meaning |
||||||||||||||||||
|
0 through 15 |
Specific rights. Contains the access mask specific to the object type associated with the mask. |
||||||||||||||||||
|
16 through 23 |
Standard rights. Contains the object's standard access rights and can be a combination of the following pre-defined flags:
|
||||||||||||||||||
|
24 |
Access system security (ACCESS_SYSTEM_SECURITY). This flag is not a typical access type. It is used to indicate access to an ACL system. This type of access requires the calling process to have a specific privilege. |
||||||||||||||||||
|
25 |
Maximum allowed (MAXIMUM_ALLOWED) |
||||||||||||||||||
|
26 through 27 |
Reserved |
||||||||||||||||||
|
28 |
Generic all (GENERIC_ALL) |
||||||||||||||||||
|
29 |
Generic execute (GENERIC_EXECUTE) |
||||||||||||||||||
|
30 |
Generic write (GENERIC_WRITE) |
||||||||||||||||||
|
31 |
Generic read (GENERIC_READ) |
SCANERRORS
The scanner insert in this table all errors and warnings occurring during a scan. An error means that the computer was not scanned. A warning means that information will be missing for the computer.
|
Field name |
Data type |
Description |
|
id_snapshot |
number |
Snapshot auto-number |
|
server_name |
string |
Name or network address of the related computer |
|
EventLevel |
number |
0/1 for warning/error |
|
EventCode |
number |
scan error number see appendix |
Appendix Errors & Warning codes
|
Code |
Symbolic name |
Level |
Description |
|
0 |
SCAN_ERROR_NAME_RESOLUTION |
Error |
Unable to to resolve the name |
|
1 |
SCAN_ERROR_PING |
Error |
Unable to ping |
|
2 |
SCAN_ERROR_NETPATH_NOTFOUND |
Error |
Network path not found |
|
3 |
SCAN_ERROR_REMOTEREG |
Error |
Unable to access the registry |
|
4 |
SCAN_ERROR_ACCESS_DENIED |
Error |
Access denied |
|
5 |
SCAN_ERROR_CONNECT |
Error |
Unable to connect |
|
6 |
SCAN_ERROR_COMPUTER_REC |
Error |
Unable to insert the computer in the database |
|
7 |
SCAN_ERROR_LICENSE_SERVERS |
Error |
Not enough server licenses |
|
8 |
SCAN_ERROR_LICENSE_WKSTAS |
Error |
Not enough workstation licenses |
|
9 |
SCAN_ERROR_OTHER |
Error |
Unspecified error |
|
10 |
SCAN_ERROR_EXCEPTION |
Error |
Unexpected error |
|
100 |
SCAN_WARNING_SMBIOS_INITDENIED |
Warning |
Advanced scan (Initialization denied) |
|
101 |
SCAN_WARNING_SMBIOS_RPCUNAVAILABLE |
Warning |
Advanced scan (RPC server unavailable) |
|
102 |
SCAN_WARNING_SMBIOS_NODATA |
Warning |
Advanced scan (No SMBIOS data) |
|
103 |
SCAN_WARNING_SMBIOS_OTHER |
Warning |
Advanced scan error |
|
104 |
SCAN_WARNING_NOADMINSHARES |
Warning |
No administrative shares |
|
105 |
SCAN_WARNING_DBINSERTION |
Warning |
Database insertion error |
|
106 |
SCAN_WARNING_OTHER |
Warning |
Unspecified warning |
|
107 |
SCAN_WARNING_ERRORSHARES |
Warning |
Unable to scan shares |
|
108 |
SCAN_WARNING_ERRORSERVICES |
Warning |
Unable to scan services |
|
109 |
SCAN_WARNING_EXCEPTION |
Warning |
Unexpected warning |
|
1000 |
SCAN_DOMAIN_ERROR_OU |
Domain Error |
Unable to retrieve computers from the Global Catalog |
|
1001 |
SCAN_DOMAIN_ERROR_LIST |
Domain Error |
Unable to find a domain controller |
|
1002 |
SCAN_DOMAIN_ERROR_CONTROLLER |
Domain Error |
Unable to retrieve computers from the domain controller |
SERVERS
This table describes the list of computers specifying their name, type, comments and service pack.
|
Field name |
Data type |
Description |
|
id_snapshot |
number |
Identifier of the network snapshot. |
|
server_name |
string |
Netbios name of the server without the two preceding backslash characters. |
|
domain_name |
string |
Name of the domain (or the workgroup) to which the servers belongs. |
|
type |
number |
Number composed of a bit mask describing the type of the server (see Appendix 1). |
|
texttype |
string |
A comprehensible text string describing the preceding type value. |
|
comments |
string |
Comments of the server. |
|
maxusers |
number |
Maximal number of concurrent connected users. If this value equals -1, it means that there is no limit. |
|
userspath |
string |
This string contains the path to user directories. |
|
sp |
string |
Describes the actual Windows NT Service Pack installed. |
|
install_date |
date |
Date when the operating system has been installed. |
|
bios_type |
string |
Bios description. |
|
bios_date |
string |
Bios date (useful for Y2K tests). |
|
os |
string |
Active operating system. |
|
OSLevel |
0 = workstation/ 1 = server/ 2 advanced server |
|
|
wmi |
number |
Equals 1 if Windows Management Instrumentation is active on the computer. Otherwise, it is equals to 0. |
|
ram |
number |
Amount of physical memory (MB). |
|
ramUsed |
number |
Memory in use (MB) |
|
dns_hostname |
string |
|
|
dns_domainname |
string |
|
|
dns_nameservers |
string |
|
|
dns_suffixes |
string |
|
|
Manufacturer |
string |
Computer's manufacturer |
|
Model |
string |
Computer's model |
|
Serial |
string |
Computer's serial number |
|
MotherBoard |
string |
|
|
MBSerial |
string |
Motherboard's serial |
|
MBManufacturer |
string |
Motherboard's manufacturer |
|
SmBIOSVersion |
string |
Supported version of the SMBIOS standard |
|
DComEnabled |
number |
0/1 DCOM is disabled/enabled |
|
RegisteredOwner |
string |
Name of the registered user |
|
RegisteredOrganization |
string |
Name of the registered company |
|
LastUser |
string |
Last logged on user (account_name) |
|
SystemRoot |
string |
OS directory (commonly c:\winnt c:\windows) |
|
ProgramFilesDir |
string |
Commonly c:\program files\ |
|
CommonFilesDir |
string |
Commonly c:\program files\Common Files |
|
BootTime |
number |
Time interval (in days) since the last boot of the machine |
|
IdleTime |
number |
Idle Time (in days) since the last boot. % Used processor time = 100-IdleTime/BootTime*100 |
|
ScanTime |
time |
Scan time |
|
IEVersion |
number |
Internet Explorer version |
|
IESPNumber |
number |
Internet Explorer service pack |
|
LanguageId |
number |
Operating system language. See appendix 2 for the meaning of this number. |
|
CanonicalName |
string |
Canonical name of the computer in the Active Directory |
|
Container |
string |
Container of the computer in the Active Directory |
|
ComputerState |
number |
1/0 need a reboot yes/no |
|
ChassisType |
number |
Computer case see appendix 3. |
|
ChipSet |
string |
|
|
Platform |
number |
|
|
Edition |
string |
Edition |
Appendix 1
|
Symbolic constant |
Value |
Meaning |
|
SV_TYPE_WORKSTATION |
0x00000001 |
All LAN Manager workstations. |
|
SV_TYPE_SERVER |
0x00000002 |
All LAN Manager servers. |
|
SV_TYPE_SQLSERVER |
0x00000004 |
Any server running with Microsoft SQL Server. |
|
SV_TYPE_DOMAIN_CTRL |
0x00000008 |
Primary domain controller. |
|
SV_TYPE_DOMAIN_BAKCTRL |
0x00000010 |
Backup domain controller. |
|
SV_TYPE_TIMESOURCE |
0x00000020 |
Server running the Timesource service. |
|
SV_TYPE_AFP |
0x00000040 |
Apple File Protocol servers. |
|
SV_TYPE_NOVELL |
0x00000080 |
Novell servers. |
|
SV_TYPE_DOMAIN_MEMBER |
0x00000100 |
LAN Manager 2.x Domain Member. |
|
SV_TYPE_LOCAL_LIST_ONLY |
0x40000000 |
Servers maintained by the browser. |
|
SV_TYPE_PRINT |
0x00000200 |
Server sharing print queue. |
|
SV_TYPE_DIALIN |
0x00000400 |
Server running dial-in service. |
|
SV_TYPE_XENIX_SERVER |
0x00000800 |
Xenix server. |
|
SV_TYPE_MFPN |
0x00004000 |
Microsoft File and Print for Netware. |
|
SV_TYPE_NT |
0x00001000 |
Windows NT (poste de travail ou serveur). |
|
SV_TYPE_WFW |
0x00002000 |
Server running Windows for Workgroups. |
|
SV_TYPE_SERVER_NT |
0x00008000 |
Windows NT non-DC server. |
|
SV_TYPE_POTENTIAL_BROWSER |
0x00010000 |
Server that can run the Browser service. |
|
SV_TYPE_BACKUP_BROWSER |
0x00020000 |
Server running a Browser service as backup. |
|
SV_TYPE_MASTER_BROWSER |
0x00040000 |
Server running the master Browser service. |
|
SV_TYPE_DOMAIN_MASTER |
0x00080000 |
Server running the domain master Browser. |
|
SV_TYPE_DOMAIN_ENUM |
0x80000000 |
Primary Domain. |
|
SV_TYPE_WINDOWS |
0x00400000 |
Windows 95 or later. |
|
SV_TYPE_ALL |
0xFFFFFFF |
All servers. |
Appendix 2
|
Constante symbolique |
Valeur |
Signification |
|
LANG_NEUTRAL |
0x00 |
Neutral |
|
LANG_ARABIC |
0x01 |
Arabic |
|
LANG_BULGARIAN |
0x02 |
Bulgarian |
|
LANG_CATALAN |
0x03 |
Catalan |
|
LANG_CHINESE |
0x04 |
Chinese |
|
LANG_CZECH |
0x05 |
Czech |
|
LANG_DANISH |
0x06 |
Danish |
|
LANG_GERMAN |
0x07 |
German |
|
LANG_GREEK |
0x08 |
Greek |
|
LANG_ENGLISH |
0x09 |
English |
|
LANG_SPANISH |
0x0a |
Spanish |
|
LANG_FINNISH |
0x0b |
Finnish |
|
LANG_FRENCH |
0x0c |
French |
|
LANG_HEBREW |
0x0d |
Hebrew |
|
LANG_HUNGARIAN |
0x0e |
Hungarian |
|
LANG_ICELANDIC |
0x0f |
Icelandic |
|
LANG_ITALIAN |
0x10 |
Italian |
|
LANG_JAPANESE |
0x11 |
Japanese |
|
LANG_KOREAN |
0x12 |
Korean |
|
LANG_DUTCH |
0x13 |
Dutch |
|
LANG_NORWEGIAN |
0x14 |
Norwegian |
|
LANG_POLISH |
0x15 |
Polish |
|
LANG_PORTUGUESE |
0x16 |
Portuguese |
|
LANG_ROMANIAN |
0x18 |
Romanian |
|
LANG_RUSSIAN |
0x19 |
Russian |
|
LANG_CROATIAN |
0x1a |
Croatian |
|
LANG_SERBIAN |
0x1a |
Serbian |
|
LANG_SLOVAK |
0x1b |
Slovak |
|
LANG_ALBANIAN |
0x1c |
Albanian |
|
LANG_SWEDISH |
0x1d |
Swedish |
|
LANG_THAI |
0x1e |
Thai |
|
LANG_TURKISH |
0x1f |
Turkish |
|
LANG_URDU |
0x20 |
Urdu |
|
LANG_INDONESIAN |
0x21 |
Indonesian |
|
LANG_UKRAINIAN |
0x22 |
Ukrainian |
|
LANG_BELARUSIAN |
0x23 |
Belarusian |
|
LANG_SLOVENIAN |
0x24 |
Slovenian |
|
LANG_ESTONIAN |
0x25 |
Estonian |
|
LANG_LATVIAN |
0x26 |
Latvian |
|
LANG_LITHUANIAN |
0x27 |
Lithuanian |
|
LANG_FARSI |
0x29 |
Farsi |
|
LANG_VIETNAMESE |
0x2a |
Vietnamese |
|
LANG_ARMENIAN |
0x2b |
Armenian |
|
LANG_AZERI |
0x2c |
Azeri |
|
LANG_BASQUE |
0x2d |
Basque |
|
LANG_MACEDONIAN |
0x2f |
FYRO Macedonian |
|
LANG_AFRIKAANS |
0x36 |
Afrikaans |
|
LANG_GEORGIAN |
0x37 |
Georgian |
|
LANG_FAEROESE |
0x38 |
Faeroese |
|
LANG_HINDI |
0x39 |
Hindi |
|
LANG_MALAY |
0x3e |
Malay |
|
LANG_KAZAK |
0x3f |
Kazak |
|
LANG_KYRGYZ |
0x40 |
Kyrgyz |
|
LANG_SWAHILI |
0x41 |
Swahili |
|
LANG_UZBEK |
0x43 |
Uzbek |
|
LANG_TATAR |
0x44 |
Tatar |
|
LANG_BENGALI |
0x45 |
Not supported |
|
LANG_PUNJABI |
0x46 |
Punjabi |
|
LANG_GUJARATI |
0x47 |
Gujarati |
|
LANG_ORIYA |
0x48 |
Not supported |
|
LANG_TAMIL |
0x49 |
Tamil |
|
LANG_TELUGU |
0x4a |
Telugu |
|
LANG_KANNADA |
0x4b |
Kannada |
|
LANG_MALAYALAM |
0x4c |
Not supported |
|
LANG_ASSAMESE |
0x4d |
Not supported |
|
LANG_MARATHI |
0x4e |
Marathi |
|
LANG_SANSKRIT |
0x4f |
Sanskrit |
|
LANG_MONGOLIAN |
0x50 |
Mongolian |
|
LANG_GALICIAN |
0x56 |
Galician |
|
LANG_KONKANI |
0x57 |
Konkani |
|
LANG_MANIPURI |
0x58 |
Not supported |
|
LANG_SINDHI |
0x59 |
Not supported |
|
LANG_SYRIAC |
0x5a |
Syriac |
|
LANG_KASHMIRI |
0x60 |
Not supported |
|
LANG_NEPALI |
0x61 |
Not supported |
|
LANG_DIVEHI |
0x65 |
Divehi |
|
LANG_INVARIANT |
0x7f |
Appendix 3 Chassis type
|
Nombre |
Cas |
|
1 |
Autres |
|
2 |
Inconnu |
|
3 |
Desktop |
|
4 |
Low Profile Desktop |
|
5 |
Pizza Box |
|
6 |
Mini Tower |
|
7 |
Tower |
|
8 |
Portable |
|
9 |
LapTop |
|
10 |
Notebook |
|
11 |
Hand Held |
|
12 |
Docking Station |
|
13 |
All in One |
|
14 |
Sub Notebook |
|
15 |
Space-saving |
|
16 |
Lunch Box |
|
17 |
Main Server Chassis |
|
18 |
Expansion Chassis |
|
19 |
SubChassis |
|
20 |
Bus Expansion Chassis |
|
21 |
Peripheral Chassis |
|
22 |
RAID Chassis |
|
23 |
Rack Mount Chassis |
|
24 |
Multi-system chassis. |
Schema