What's new in FileAudit 5
What's new in FileAudit 5.5
- Detailed Activity Overview – By User
- Detailed Activity Overview – By File or Folder
- Full Event Details
- Report on Archived Databases
- Send notifications and reports to Slack
- Improvements to Scheduled Reports
- Service Improvements
What's new in FileAudit 5.2
- Detect and display the machine name
- Filter access events by Active Directory Group
- Filter access events by object type
- Email notifications in case of a new FileAudit Service Event
- Detect and alert on server inactivity
- Support for Windows Server 2016
What's new in FileAudit 5.0
FileAudit 5.5
The release of FileAudit 5.5 is focused on helping IT administrators better identify and analyze abnormal file activity.
Sometimes the challenge with data breaches is to know they even happened at all, with the average number of days needed to discover a breach being 191 days1. However, should protected data reside on a file server, obvious leading indicators of a breach will exist. By monitoring the access and usage of protected data on file servers, it is possible to detect a data breach based on unusual or abnormal activity.
For more information on how to identify unusual file activity and impede data breaches read the whitepaper The role of File Auditing to Spot and Stop a Data Breach.
1 Ponemon Institute, Cost of a Data Breach Study (2017)
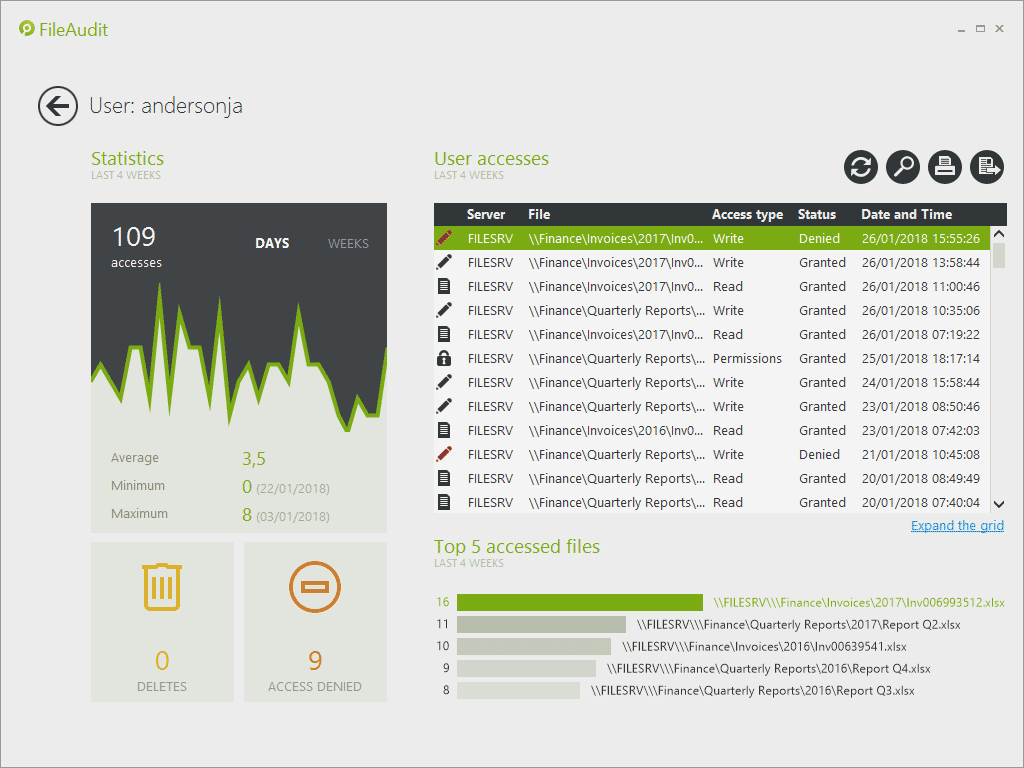
Detailed Activity Overview – By User
This new dashboard provides a detailed activity report on all file and folders a specified user has accessed, or attempted to access.
Click on any user from the File Access Viewer or Statistics to see all events performed in the previous 4 weeks.
The dashboard offers key insights into a users’ access to and usage of audited data:
- A Usage activity chart - and statistics - to easily view the frequency and amount of activity, grouped by days or weeks,
- The Total number of file deletions and refused access events for that specified user,
- A table listing all access events performed by the user,
- The Top 5 accessed files.
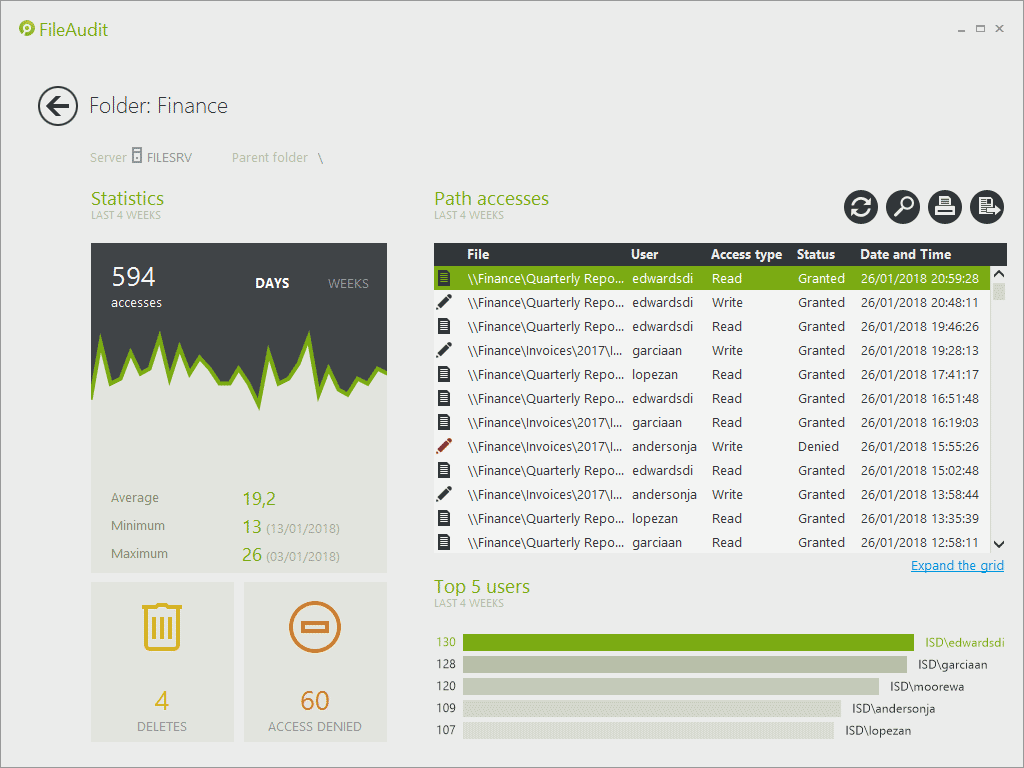
Detailed Activity Overview – By File or Folder
This new dashboard provides a detailed activity report on the access to a specified file or folder from all users.
Click on any file or folder path from the File Access Viewer or Statistics to see all events performed in the previous 4 weeks.
The dashboard offers key insights on the access to and usage of a particular data set:
- A Usage activity chart - and statistics - to easily view the frequency and amount of activity, grouped by days or weeks,
- The Total number of file deletions and refused access events for a specific file or folder,
- A table listing all access events performed for a specific file or folder,
- The Top 5 users who have accessed this file or folder.
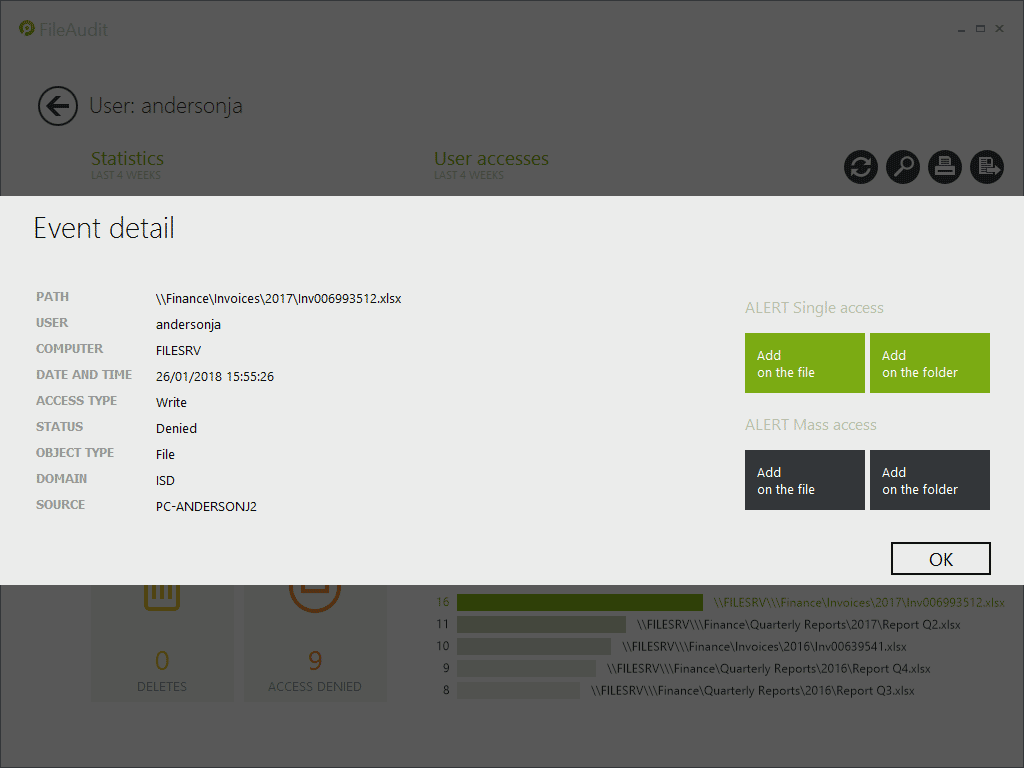
Full Event Details
Double clicking on the access event will now bring up the full event details.
Report on Archived Databases
Should the organization need to access archived records for regulatory compliance or to investigate an historical incident, a new tool (FileAuditReporter) is now available in the installation folder. This tool allows you to easily retrieve, analyze and report on archived data.
Send notifications and reports to Slack
Integrating Slack with FileAudit can help the whole IT team to be more reactive to alerts, track issues and share reports. Any message from FileAudit (alert, scheduled report, warning message) can be sent to a shared channel or direct message in Slack. More info.
Improvements to Scheduled Reports
A new option now exists to keep all historical reports. (You can if required, still automatically overwrite the old scheduled report with the latest version). There is also no obligation to email the report and the exact folder can be defined to where the scheduled reports are saved. More info.
Service Improvements
Ability to restart the FileAudit service when changing remote connection settings. More info.
FileAudit 5.2
Detect and display the machine name
In addition to the IP address, FileAudit 5.2 now provides the machine name from which a user accessed a file/folder through the network. This further strengthens the identification of any access made to help attribute access to an individual user and identify potential suspicious activities.
A list of every access made from a specific machine name can be made using FileAudit’s filtering capabilities. Administrators can apply this criteria from the ‘File access view’. It is also possible to define a machine name as a selected criteria:
- to trigger specific access alerts
- for a scheduled report
Filter access events by Active Directory Group
FileAudit 5.2 has introduced a new filtering criteria that allows you to focus on access events for one or more Active Directory Groups.
From the FileAudit console, browse and identify Active Directory Groups to configure alerts, schedule reports or apply as a criteria from the ‘File Access Viewer’.
Group filters can be used to either exclude or include group members.
Inclusion example
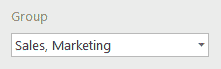
All accesses of Sales and Marketing group members will be displayed.
Exclusion example
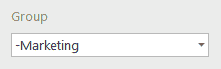
Accesses of Everyone except Marketing group members will be displayed.
Inclusion + exclusion example
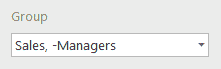
All accesses of Sales group members will be displayed, except for users also members of Managers group.
If there are no common members betweenSales and Managers groups, it will include all Sales members. If all members of Sales are members of Managers, no data will be displayed.
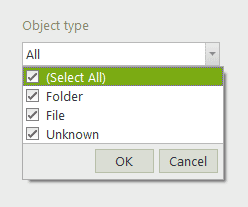
Filter access events by object type
With FileAudit 5.2, administrators can now have the option to distinguish between a file and folder.
You can apply this criteria from the ‘File access view’. Alternatively it can be used when configuring any access alerts or scheduling access reports.
This optimization helps keep your audit trail more meaningful.
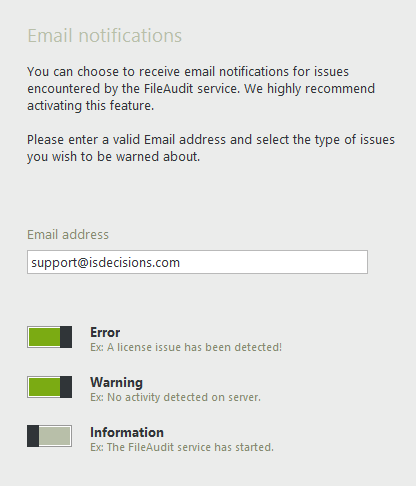
Email notifications in case of a new FileAudit Service Event
Receive email alerts about issues that the FileAudit service has met.
Determine the type of alerts you want to be notified about: Error, Warning and Information.
Detect and alert on server inactivity
An alert warns the administrator when FileAudit has not monitored a file access event for more than three consecutive days on a specific server. This alert is both on the FileAudit console and sent by email.
This can highlight to an administrator an issue that needs to be addressed — for example if the object access audit policy is disabled, the NTFS audit configuration is deleted or the security log is corrupted or misconfigured.
Support for Windows Server 2016
FileAudit 5.2 supports Windows Server 2016.
FileAudit 5.0
Detect the source IP address
FileAudit now detects the IP address of the machine from which the file/folder access has been performed. When the access is performed directly on the file server hosting the file/folder accessed (local access), FileAudit displays in the column ‘Source’ the name of the process from which the user has accessed the file. When the file/folder is accessed through the network, this ‘Source’ column displays the IP address of the machine from which the user has performed the access.
A list of every access made from a specific IP address, and thus a specific machine, can be made using FileAudit’s filtering capabilities. Administrators can apply this criteria from the ‘File access viewer’.
It is also possible to define an IP address in the ‘Source’ field of the ‘Main’ tab:
- As a selected criteria to trigger specific access alerts,
- As a selected criteria for a scheduled report.
Mass access alert
A new type of alert allows administrators to monitor the frequency of an access type to files/folders performed by the same user. Alerts can be triggered when a user performs a number of accesses deemed beyond the tolerated threshold for a defined period of time.
For example, this new type of alert allows administrators to be warned:
- That a user has performed more than 500 read accesses during 1 minute,
- That a user has deleted more than 200 files during 30 seconds,
- Etc.
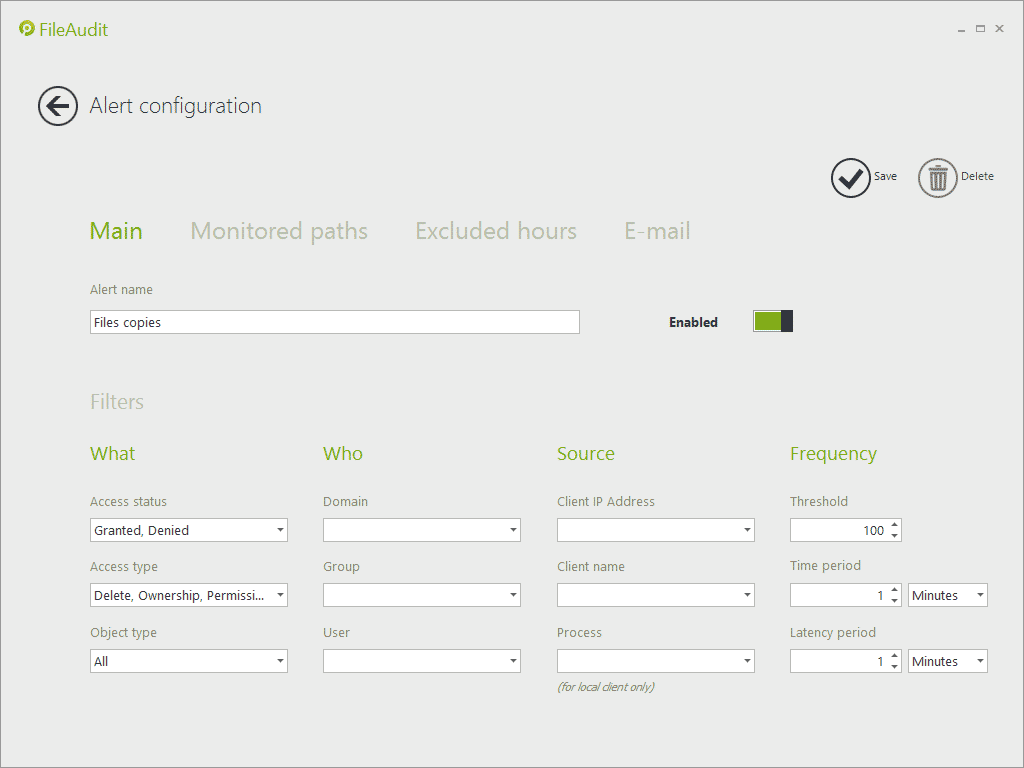
Detect file copying
When a significant number of read accesses are performed during a short period of time, the probability is that the user has executed a copy/paste file operation. The alert indicates the user name, the date and time of the violation as well as the alert parameters, making it easy to further investigate within FileAudit the full access history.
Alert on access out of business hours
When configuring alerts, a new tab allows administrators to define, as additional criteria, the business days and hours during which access to the specified path is considered as normal.
All access out of the hours configured in this tab will then be considered as abnormal and will trigger the alert if the other criteria are also satisfied.
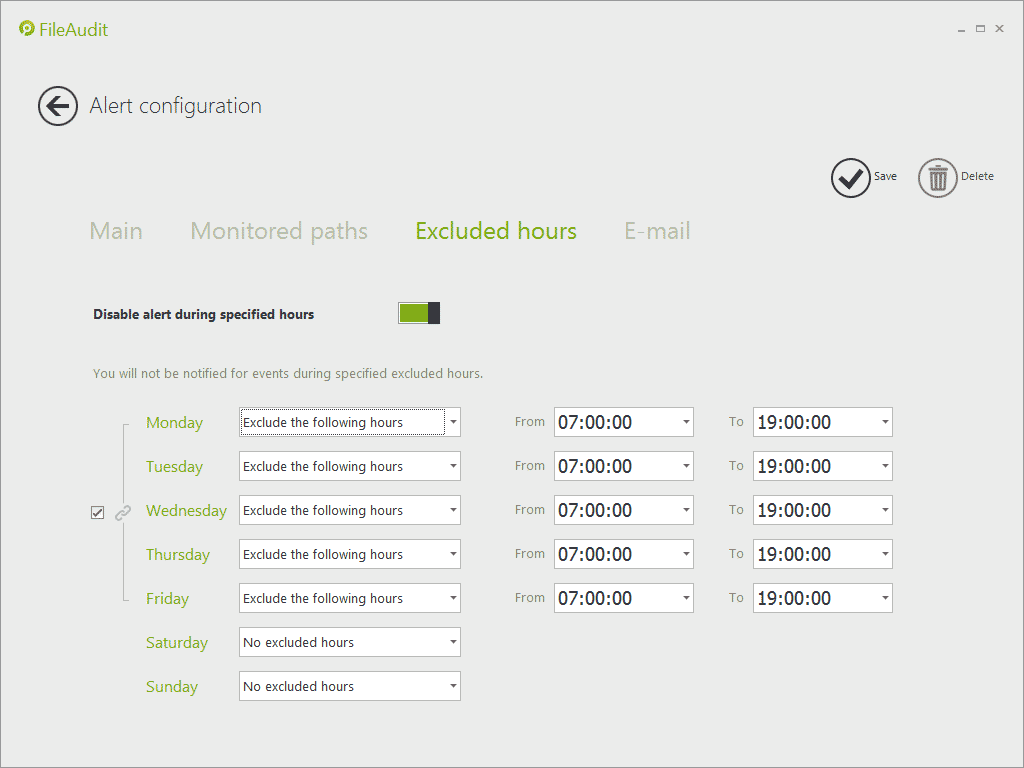
Example of a week for which access to the designated files/folders will be considered as normal. If all criteria defined in the ‘Main’ tab are filled, the alert will be triggered if an access is performed before 8:00 AM or after 7:00 PM from Monday to Friday, or if an access is performed during the weekend.
More features
- FileAudit now supports MySQL as database system.
- Choose the path(s) on which you want to displays access statistics and graphs in the ‘Statistics’ view amongst all the paths registered as audited.
- Add a corporate logo in the printed/exported reports.
- Check the availability of new versions, direct from the FileAudit Console.
- Etc.