Deploying an agent
UserLock agents are required to enforce access policies and track user sessions. The easiest way to deploy them is directly from the UserLock console. For advanced scenarios (IIS, NPS, or manual deployment), see the linked guides.
Useful resources
In the UserLock console, go to Environment ▸ Machines.
Select one or more machines and click on the Actions button.
In the menu, click to Install the Desktop, IIS or NPS agents.
In the upper right corner, the Admin action icon animates. Click it to monitor the installation progress.
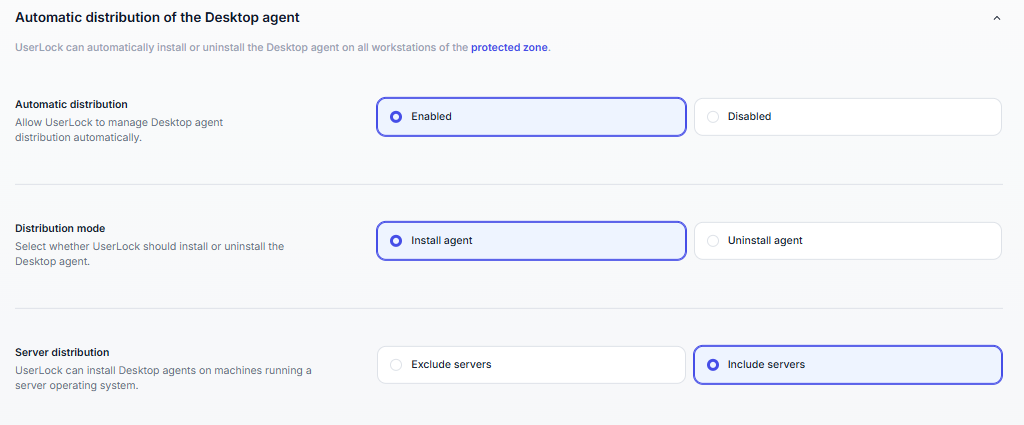
Instead of deploying the Desktop agent manually on each workstation, you can let UserLock handle the distribution automatically.
In the upper right corner of the UserLock console, click on the Settings icon.
In the left menu, click on Agent distribution.
Under Automatic distribution, select Enabled.
Choose the Distribution mode:
Install agent → UserLock automatically installs the Desktop agent on all workstations in the protected zone.
Uninstall agent → UserLock removes the Desktop agent from those machines.
Under Server distribution, decide whether to include machines running a server operating system:
Include servers (recommended if you want server sessions protected).
Exclude servers (recommended if only workstations should be protected).
💡️ Once enabled, every new workstation added to the protected zone will automatically receive (or uninstall) the Desktop agent, according to your settings.
Note
Get more about this feature on the agent distribution settings page.
Agents can also be installed manually in cases where console deployment is not possible. Options include:
Running the installer locally on the machine.
Deploying through a script.
Using Group Policy (GPO).
Manual deployment is typically used for advanced or large-scale scenarios.
See the following guides to help you through manual installation.