Admin actions and configurations
The Admin actions and configurations section describes the administrative capabilities available in UserLock. Administrators can act on sessions, machines, and users, and configure server settings and access policies. All actions and configuration changes are logged for traceability and auditing.
UserLock allows administrators to remotely interact with all user sessions, whether open or locked, through the Active sessions page of the Activity section.
The following actions are available:
Lock | Lock the session, requiring the user to re-authenticate to regain access. |
|---|---|
Logoff | Terminate a session immediately. Compatible with interactive sessions (workstation and terminal) and IIS sessions. |
Reset | Remove the session from UserLock’s monitoring. This action is intended for sessions that are no longer valid (e.g., when a machine suffered a hardware issue preventing proper restart). We recommend using Reset only when certain that the session is no longer pertinent. A reset session is permanently removed from the list of known sessions.
|
Send popup | Display a custom message to the user. Compatible with interactive sessions (workstation and terminal) only. |
UserLock allows administrators to manage agents or control the machine remotely.
The following actions are available:
Install / update agent | Deploy or upgrade the UserLock agent. |
|---|---|
Uninstall agent | Remove the agent. |
Restart | Reboot a machine remotely. |
Shut down | Safely power off a machine. |
Wake up | Power on a machine remotely using wake-on-LAN. |
Machine actions can be triggered from the context menus available in:
the Machines page of the Environment section,
the Machines in use page of the Activity section,
the Machine dashboard.
Warning
By default, the UserLock service runs under the Network Service account to operate with the least privileges possible. Agent deployment and other remote interactions with machines require privilege elevation.
To perform these actions, the UserLock service impersonates the credentials defined in the Service section of the Server settings.
UserLock allows administrators to manage user MFA configurations.
The following actions are available:
Block / Unblock user | Prevent or allow the user to connect to the network. See more information. |
|---|---|
Disable MFA temporarily | Allow the user to connect without MFA for a limited time, typically for troubleshooting or exceptional access. A temporary access policy will be created. |
Resolve MFA help request | Mark an MFA help request as resolved after alternative assistance has been provided. |
Reset MFA configuration | Clear the user’s MFA setup to allow re-enrollment with a new authentication method. |
Add a policy | Directly add an access policy to the selected user. |
User actions can be triggered from the corresponding context menus available in:
the Users pages of the Environment section
the Connected users page of the Activity section
the User dashboard
When users have trouble authenticating with MFA, they can submit a help request (if the feature is enabled). These requests appear in a dedicated MFA Help Requests page of the Activity section.
The following actions are available:
Disable MFA temporarily | Allow the user to connect without MFA for a limited time, typically for troubleshooting or exceptional access. A temporary access policy will be created. |
|---|---|
Reset MFA configuration | Clear the user’s MFA setup to allow re-enrollment with a new authentication method. |
Resolve MFA help request | Mark an MFA help request as resolved after alternative assistance has been provided. |
Warning
Before performing any action, administrators must verify the identity of the requester to prevent impersonation attempts.
UserLock automatically logs any server settings changes for auditing and compliance.
Update server settings | Change operational or security parameters. |
|---|---|
Update server version | Upgrade the UserLock server to the latest release. |
UserLock automatically logs all access policy configuration changes for auditing and compliance.
Create | Define a new access policy to control logon rules. |
|---|---|
Update | Modify an existing access policy. |
Delete | Remove an obsolete access policy. |
Disable MFA temporarily | Turn off MFA for a user during troubleshooting or exceptional access needs. |
Block / unblock users | Prevent or restore a user’s ability to log in. |
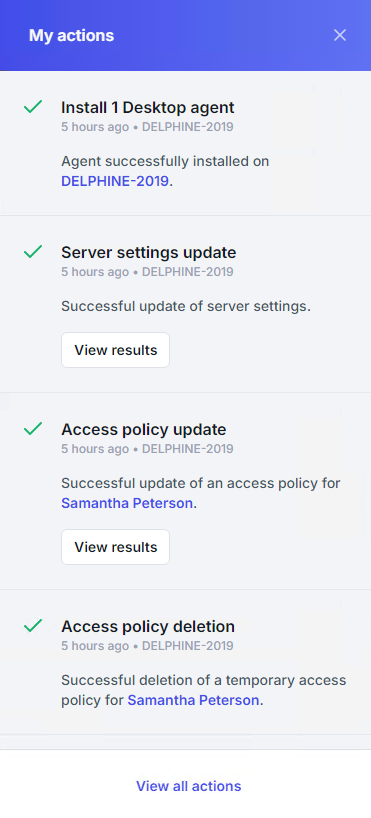
The history panel displays the last 50 actions performed by the logged-in administrator within the past 30 days.
It can be opened by clicking the lightning icon in the top-right corner of the console.
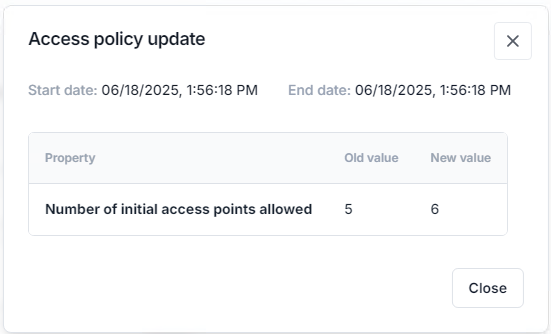
Each entry shows status, title, timestamp, target, result summary, and (if applicable) a View results button that opens a dialog with detailed results.
All actions and configurations are logged in the UserLock database for auditing and tracking purposes.
Two reports are available in the Reporting section:
Actions: records administrator operations on sessions, machines, and users.
Configurations: records administrator changes to server settings and access policies.
Why this matters
Reviewing administrator actions and configuration changes is essential for:
Security: detecting unauthorized or risky administrative behavior.
Compliance: maintaining evidence of changes for audits and regulatory requirements.
Accountability: ensuring visibility into who performed which action, when, and on which resource.
Troubleshooting: investigating failed or unexpected administrative operations.