Apply MFA for RemoteApp
Enable and configure Multi-Factor Authentication (MFA) for RemoteApp (and optionally RD Web) using UserLock.
RemoteApp allows users to run remote applications from an RDS server as if they were installed locally.
To secure these sessions, UserLock can enforce MFA when users launch or reconnect to RemoteApps.
Different scenarios may apply depending on your RemoteApp deployment, whether or not RD Web is included.
This guide explains how to configure MFA for RemoteApp with UserLock, including prerequisites, setup steps, and known limitations.
✅️ UserLock Desktop Agent installed on all RDS session hosts.
✅️ Windows services and network protocols prerequisites are met.
✅️ If your server is Windows Server 2025:
The OS build number must be 10.0.26100.4946 or higher.
The credential provider technology is used, so verify interoperability with other providers that may be installed.
✅️ On Windows Server 2022 or earlier, to protect RemoteApps requesting privilege elevation, create the registry value below:
Path
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\ISDecisions\UserLockName
UACinRemoteAppType
DWORD (32-bit)Value
1On Windows Server 2025, RemoteApps requesting privilege elevation are supported by default.
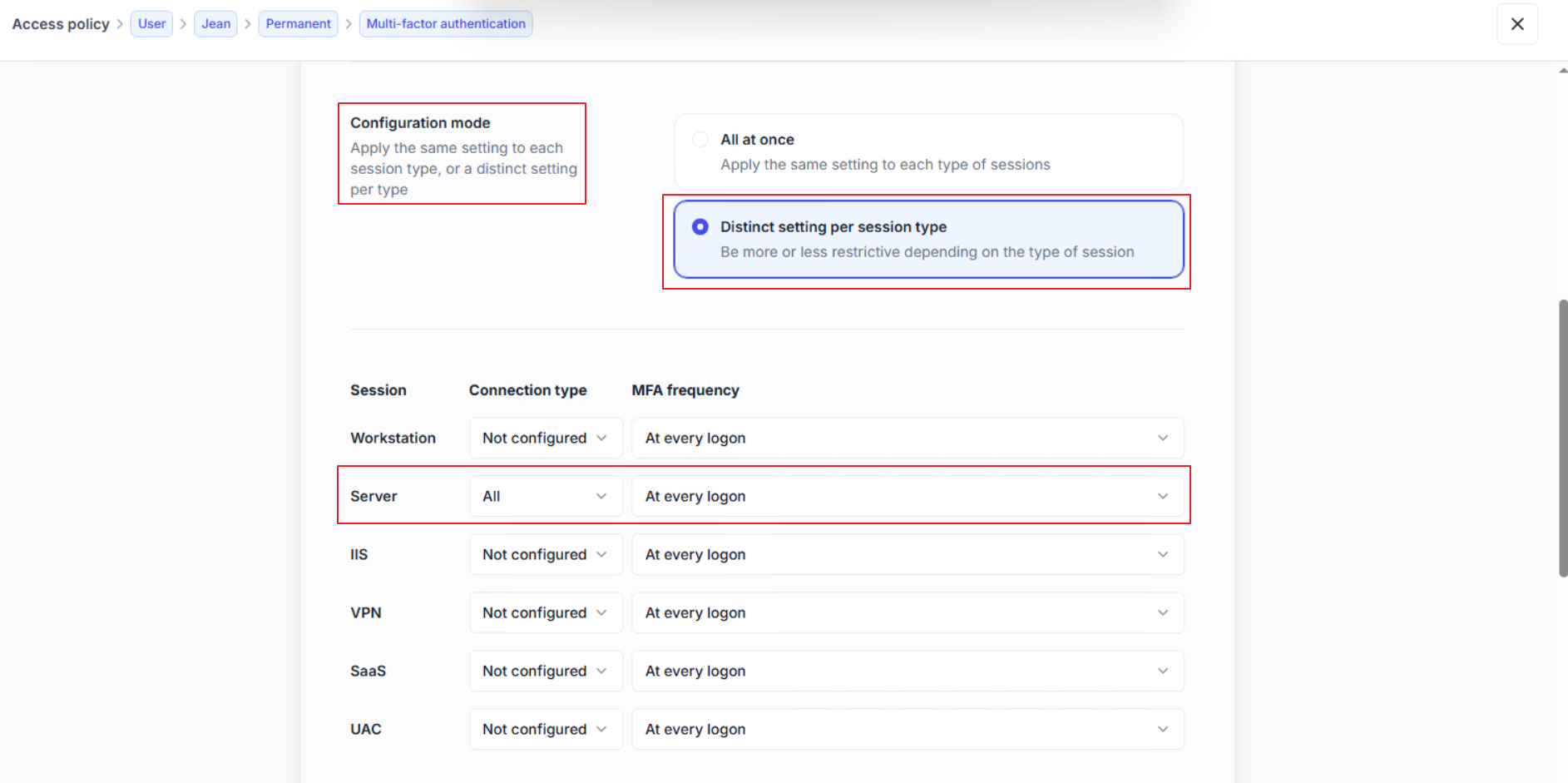
Follow the steps in Configure an access policy to create an access policy targeting the relevant users, groups, or organizational units (OUs).
Choose the Multi-factor authentication policy.
Enable the MFA.
Select the Configuration mode as Distinct setting per session type to configure the Server sessions (RemoteApps are considered server sessions).
Adjust the Connection type and MFA frequency according to your security requirements.
Test by launching a RemoteApp and confirming that the MFA challenge appears.
Verify in the UserLock Console > Activity that the session appears.
A second RemoteApp launched within the same session should not trigger MFA again.
If a RemoteApp requires privilege elevation, verify that it functions correctly.
If your RemoteApp deployment publishes session-based desktops, the enrollment will be handled by the desktop agents installed on the RD Session Host.
If your RemoteApp deployment publishes session-based applications, enrollment cannot be performed directly within those sessions. However, it can be managed through an RD Web installation, as explained in the next scenarios.
Optionally, if you want to protect access to your RD Web console and manage MFA enrollment through it, you can use UserLock IIS MFA. Refer to the How to apply MFA for IIS Apps guide for detailed instructions if needed.
To allow the enrollment of the MFA directly from a RemoteApp session, regardless of whether you are publishing programs or remote desktops, the following requirement is needed:
✅️ The registry value:
Path |
|
|---|---|
Name |
|
Type |
|
Value |
|
Note
⚠️ All MFA enrollment methods are supported except HOTP.
Optionally, if you want to protect access to your RD Web HTML5, you need to enable Windows Authentication following Microsoft’s official instructions.
Once this is done, you will be able to protect access using UserLock IIS MFA.
Refer to the How to Apply MFA for IIS Apps guide for detailed steps if needed.
Note
⚠️ The only drawback is that if users access RD Web from a machine outside the domain (or if the URL is not in the Intranet zone), they will be prompted twice for their username and password.
MFA (and other UserLock access policies) is enforced when the RDS session is established, not for each individual application.
If a RemoteApp is reconnected within 30 seconds of disconnecting, the MFA challenge is not triggered.
Support for RemoteApps requesting privilege elevation depends on the Windows Server version (see the related section).
Symptom | Probable Cause | Action |
|---|---|---|
No MFA Prompt | Policy not applied | Check target and session type settings. |
No Prompt (WS2025) | Missing or conflicting credential provider | Check credential provider installation and conflicts with other providers. |
RemoteApp with UAC blocked (pre-2025) | Missing registry value or outdated agent | Check the "UACinRemoteApp" value and agent version. |
Unable to enroll in MFA via RemoteApp | Missing value or misconfigured HTML5 portal | Check the HTML5 portal value and configuration. |
Only one session listed | Normal behavior | No action required. |