User status
User statuses classify accounts from safe to critical based on activity. Here you adjust the thresholds and conditions for each status and decide who gets notified when changes happen.
Note
To access this page, go to Server settings ▸ User status.
You need at least read permission on Server settings to view this page.
Each user is automatically assigned a status depending on their behavior on the network. Suspicious or unusual events immediately raise the user’s risk level, visible in the Users view and in the dedicated report.
Statuses are recalculated every minute. When the triggering condition is no longer valid and the user reconnects, the account returns to its normal Protected/Unprotected state.
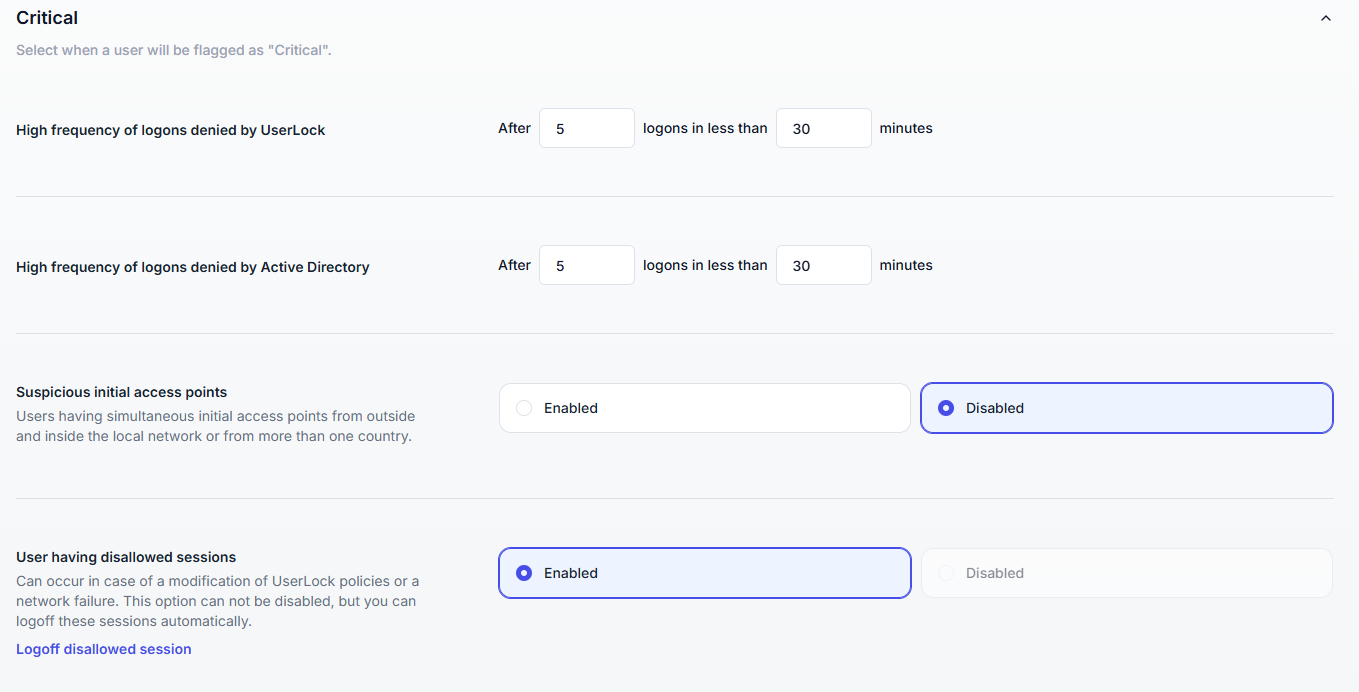
A user is flagged Critical when one of the following conditions occurs:
Triggered when UserLock or Active Directory denies more logons than allowed within the configured timeframe.
Useful to detect brute-force or password spraying attempts. By adjusting the thresholds, you can balance between catching attacks early and avoiding false positives.
Default: 5 denied logons in 30 minutes.
Triggered when simultaneous initial logons occur from both inside and outside the local network, or from more than one country.
Detects impossible travel or simultaneous connections from different networks/countries. Activating this option helps spot account compromise but may require fine-tuning in organizations with frequent remote access.
Disabled by default.
Outside IP ranges are any addresses not in:
10.0.0.0 – 10.255.255.255
172.16.0.0 – 172.31.255.255
192.168.0.0 – 192.168.255.255
fc00::/7, fe80::/10
Triggered after policy changes or network failures.
Ensures that sessions invalidated by policy changes or network failures don’t remain active. Automatic logoff reduces the risk of stale sessions being exploited.
Option cannot be disabled, but disallowed sessions can be logged off automatically.
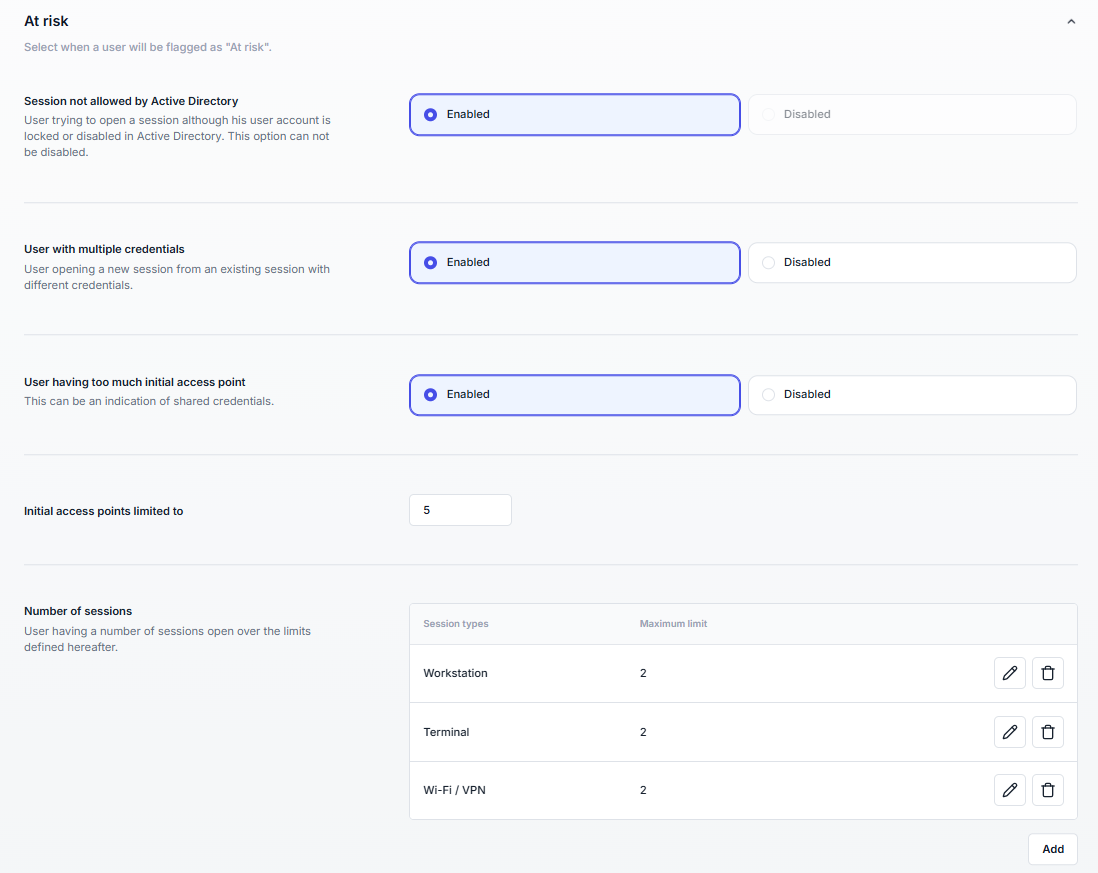
A user is flagged At risk when one of the following conditions occurs:
Detects attempts to use disabled or locked accounts. This often signals compromised credentials.
Cannot be disabled.
A new session is opened from an existing one using different credentials.
Helps uncover cases where a user switches identities mid-session, which may indicate shared credentials or privilege escalation attempts.
Disabled by default.
Number of simultaneous initial logons exceeds the configured threshold.
Useful to flag accounts that appear simultaneously on many devices or networks — a common symptom of credential sharing.
Default limit: 5 initial access points.
Number of open sessions exceeds the configured per-session-type limit.
Exceeding session limits may indicate misuse or account sharing. This feature can also be used as a “soft” control, to observe behavior before enforcing strict access policies.
Default: 2 per type (Workstation, Terminal, VPN/Wi-Fi).
These statuses are automatic and cannot be customized:
Protected: user belongs to at least one access policy.
Unprotected: user does not belong to any policy (or is a local workstation/server account). Highlights accounts outside the scope of UserLock policies (including local machine accounts). Monitoring these helps avoid blind spots in security.
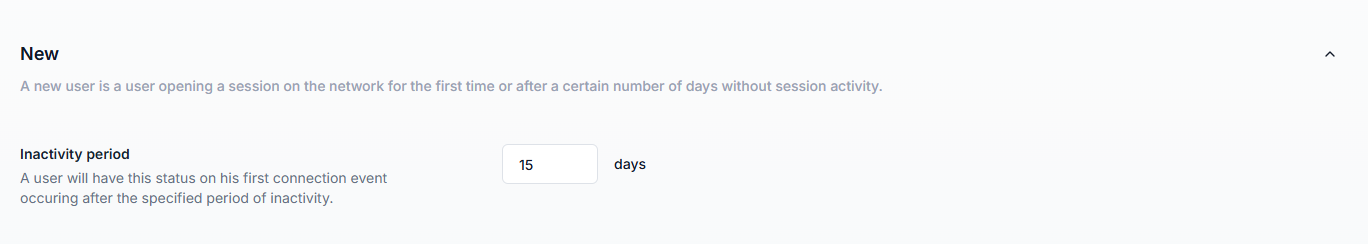
The New status identifies first-time or long-inactive accounts.
Useful to monitor onboarding of new employees or contractors.
Helps spot dormant accounts suddenly reactivated, which may be a red flag for misuse or reactivation of old credentials.
Default inactivity period: 15 days.
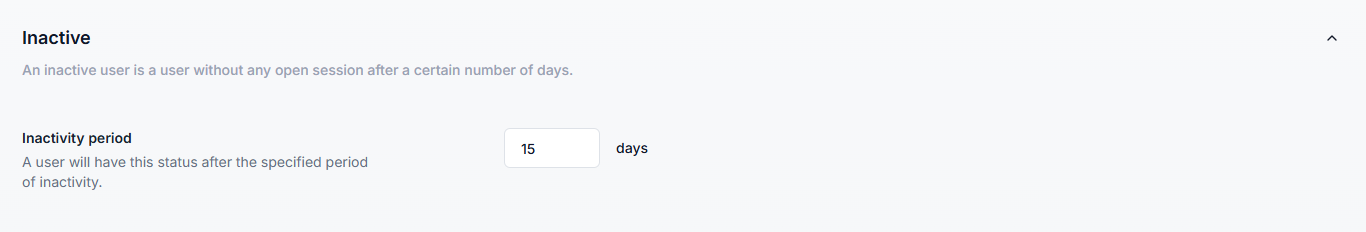
Flags accounts with no activity over a defined period.
Useful for detecting stale accounts that can be disabled or removed, reducing the attack surface.
Can support compliance by ensuring unused accounts are tracked and eventually deprovisioned.
Default: 15 days.
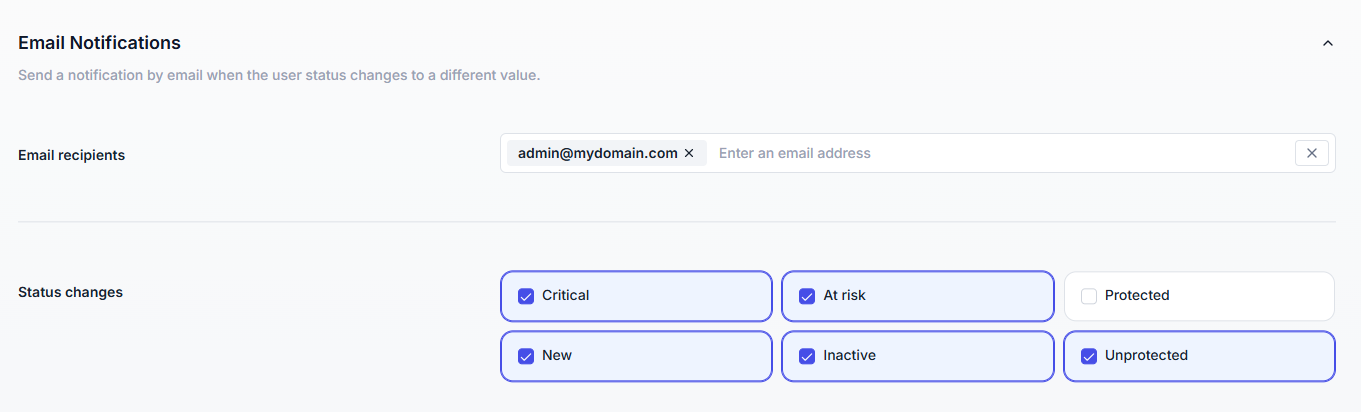
Email alerts ensure that administrators are immediately informed when a user’s status changes, even if they’re not logged into the console. This is particularly useful for Critical or At Risk events, where a quick reaction can prevent security incidents or stop ongoing attacks.
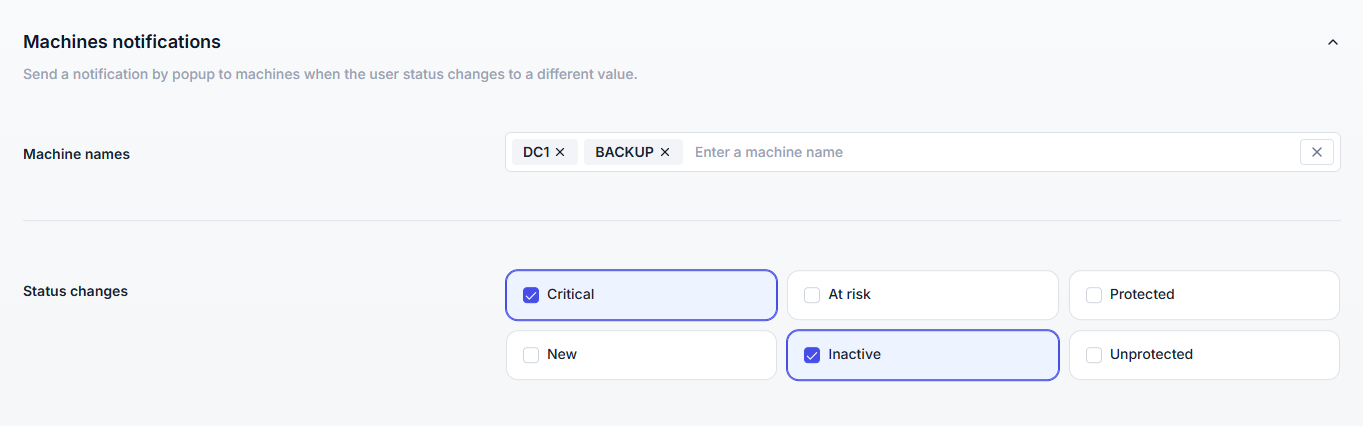
Machine popups provide instant, on-screen alerts to administrators connected to key servers or workstations. This allows rapid detection of suspicious activity without relying on email delivery or monitoring a console.