Configure Slack for UserLock Single Sign-On (SSO)
Enable Slack Single Sign-On (SSO) with UserLock to centralize authentication, enforce corporate access policies, and simplify user access to the Slack workspace.
This guide explains how to integrate Slack with UserLock Single Sign-On (SSO) using the SAML 2.0 protocol.
Once configured, Slack logins are authenticated by UserLock against Active Directory, allowing administrators to enforce UserLock access policies (MFA, time, machine, or location restrictions) on SSO sessions.
🚩️ Before starting:
You need a Slack Plus plan — SSO via SAML is not available on the Free or Pro plans.
UserLock SSO must already be installed and configured.
In the UserLock console, go to ⚙️ Server settings ▸ Single Sign-On.
In the list of applications, select Slack.
Fill in the fields with the following values:
Settings
Values
Application Domain
https://<yourWorkspace>.slack.com
(your Slack workspace domain)Email domain
Domain used by users to authenticate (e.g. contoso.com)
Save the profile.
Log in to your Slack workspace with an administrator or workspace owner account.
Go to Administration ▸ Settings and Permissions.
In the Authentication section, click Configure next to SAML authentication.
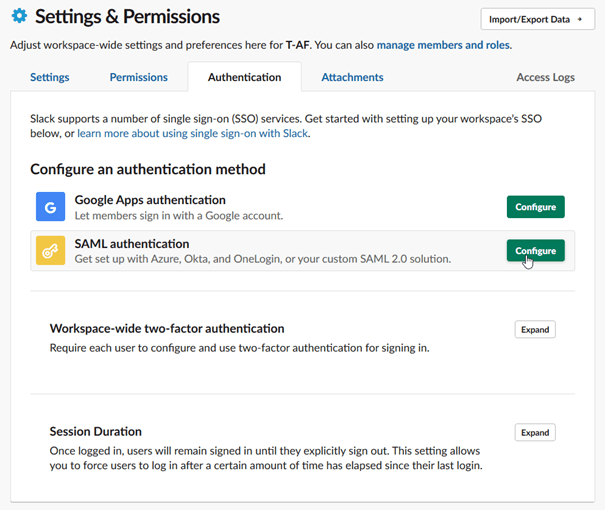
Complete the SAML configuration form using the following values:
Field
Value
SAML 2.0 Endpoint (HTTP)
https://<SSO_address>/saml/ssoIdentity Provider Issuer
https://<SSO_address>Public Certificate
Go to UserLock console▸ ⚙ Server Settings▸ Single Sign-On
Click on Download ▸ SAML certificate.
Open it in a text editor, and paste the contents here (including
-----BEGIN CERTIFICATE-----/-----END CERTIFICATE-----).
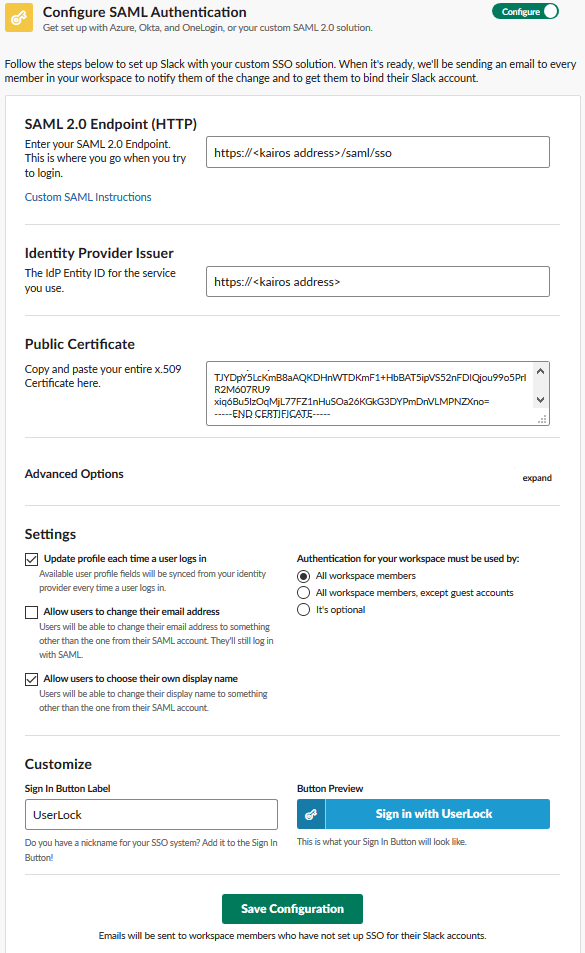
In the Configure SAML Authentication section, switch from Configure to Test mode.

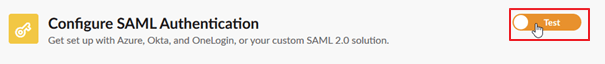
Scroll to the Test and Save section and click Test Configuration.
When the test is successful, Slack displays a confirmation message similar to: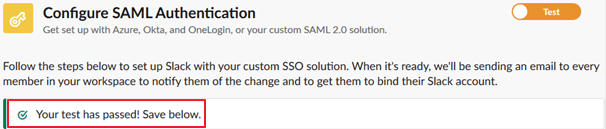
Click Save Configuration to apply the SSO setup.
For common issues, see Troubleshooting SSO.
If the problem persists, please contact IS Decisions Support.
If SSO authentication fails or becomes unavailable, only the workspace owner can disable SSO temporarily.
Ask your workspace owner to deactivate SSO from Settings and Permissions ▸ Authentication ▸ SAML Authentication while troubleshooting the issue.
You can extend the security of SSO sessions by applying UserLock access policies in addition to authentication.
Apply MFA on SaaS connections to require stronger authentication.
Hour restrictions: define when users are allowed to connect.
Geolocation rules: enforce access policies based on user location.
Session limits: allow or deny SaaS logins entirely for specific users.