Alerts & notifications
Alerts & notifications policies define how users and administrators are informed of important events. Notifications can be delivered to end users, by email, or via popup messages.
Useful resources
Display a welcome message at logon showing recent activity for the user’s credentials.
Alert users in real time if their credentials are used elsewhere on the network.
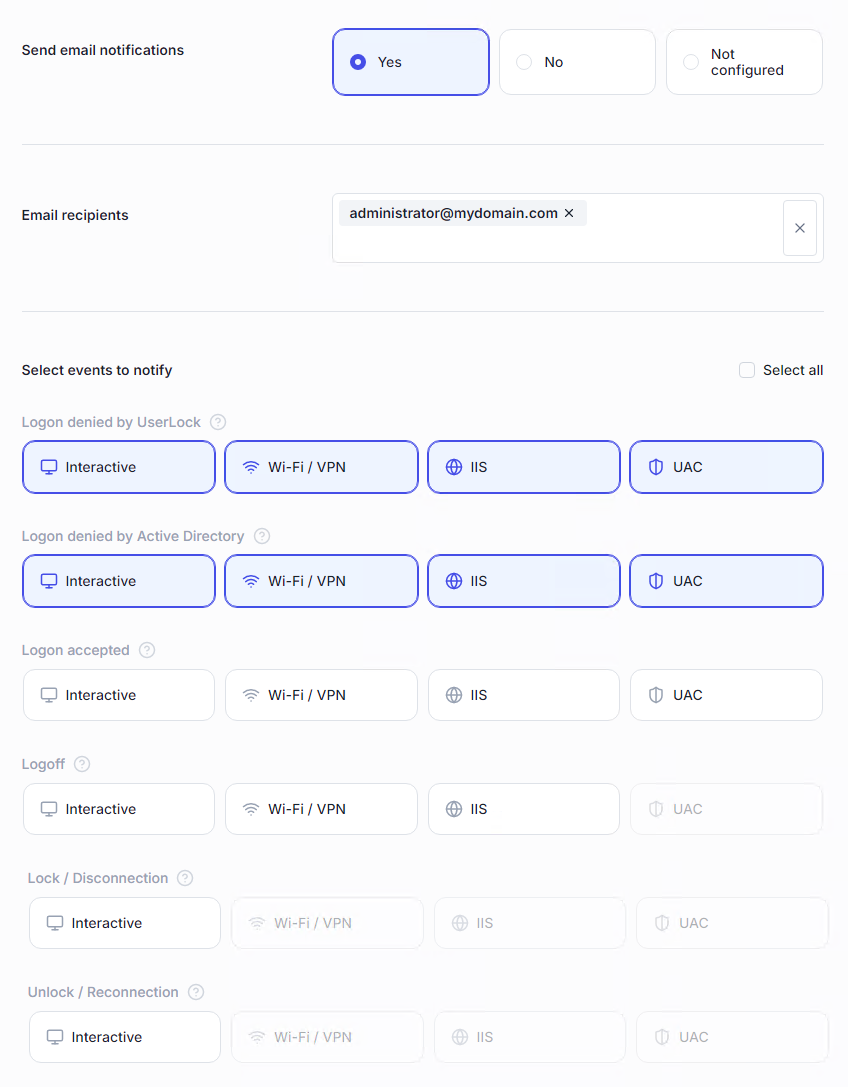
Send administrators email alerts when sensitive events occur (e.g., denied logons, suspicious activity).
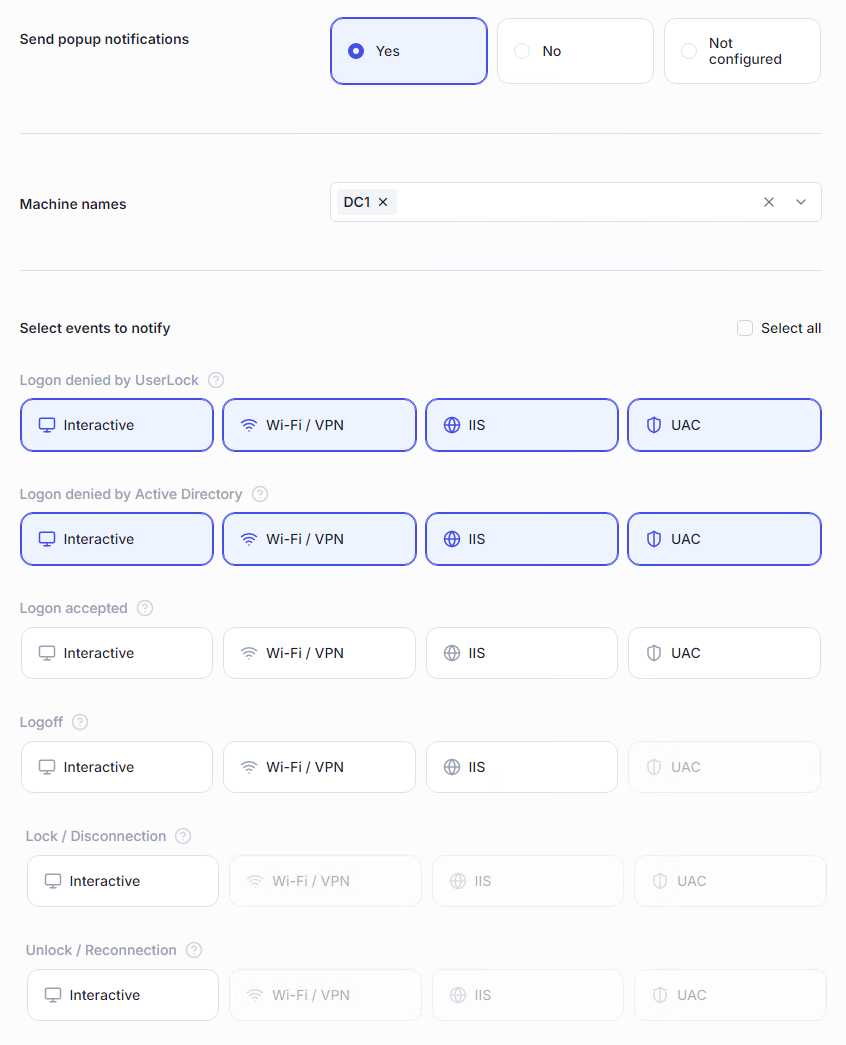
Show popup notifications on specific machines for monitoring or helpdesk purposes.
Best practice
Use a combination of end-user and administrator notifications. End users are informed about their own activity, while administrators are alerted about critical events across the network.
Welcome message: displayed at logon, useful to show time quota usage or recent connections. Content is customizable in Server settings → Messages → Welcome message.
Warn in real time: users see a popup whenever their credentials are used. Triggers can be selected per session type. Content is customizable in Server settings → Messages → Notifications for operators.
Define one or more recipient email addresses.
Choose which events will trigger an email (denied logon, accepted logon, logoff, lock, etc.).
Subject and content are customizable in Server settings → Messages → Notifications for operators.
Email server settings must be correctly configured on the UserLock server.
Display alerts on designated machines when selected events occur.
Useful for real-time monitoring (e.g., helpdesk team sees failed logons on their screen).
Subject and content customizable in Server settings → Messages → Notifications for operators.
A list of all alerts & notifications policies is available in the Access Policies section, under the Alerts & Notifications page.

If you want to react quickly to unauthorized access attempts, set up an Alerts & Notifications policy that sends an email or popup notification for Logons denied by UserLock, applied either to specific targets or to the Everyone group for centralized monitoring.
This approach helps you detect suspicious activity or configuration issues while keeping control over the alert volume