Apply MFA for VPN
Secure VPN access with Multi-Factor Authentication (MFA). Connections can be protected for VPN servers compatible with RADIUS Challenge, or for VPN servers like Microsoft’s Routing and Remote Access Service (RRAS) with several configuration options.
UserLock enforces MFA on VPN connections through its integration with the Microsoft Network Policy Server (NPS).
Two main configurations are possible, depending on your VPN environment:
VPNs supporting RADIUS Challenge:
MFA is applied directly through a standard RADIUS flow.VPNs supporting RADIUS authentication and accounting:
Solutions like Microsoft’s Routing and Remote Access Service (RRAS) can use several methods to handle MFA, depending on your configuration and user experience goals. The most seamless approach is to use UserLock VPN Connect, a dedicated client that automatically manages MFA prompts for VPN connections.
The table below summarizes the available methods and their relative ease of use:
VPN environment | MFA method | User experience |
|---|---|---|
VPN supporting RADIUS Challenge | MFA prompt appears after user credentials | ✅ Simple setup and clear MFA prompt |
Microsoft RRAS with UserLock VPN Connect | Dedicated UserLock VPN client handles MFA automatically | ✅ Seamless experience |
Microsoft RRAS with MS-CHAPv2 authentication | MFA code entered in the | ⚠️ Manual entry, risk of user error |
Microsoft RRAS with PAP authentication | MFA code entered in the | ⚠️ Manual entry, risk of user error |
Note
L2TP, SSTP, and PPTP are VPN types supported by Microsoft RRAS.
When using PAP authentication, make sure the VPN tunnel is encrypted (e.g., with L2TP/IPSec or SSTP).
Avoid PPTP, which does not provide sufficient security.
In the UserLock console, go to Environment ▸ Machines.
Locate your NPS server, then click Install in the NPS agent column.
If the "Routing and Remote Access" role or the "Remote Desktop Gateway" role is installed on the NPS server, restart the server. Otherwise, simply restart the Network Policy Server (IAS) service.
Connect once to the VPN and confirm that the user’s VPN session appears in the Activity page in the UserLock console.
This confirms that the NPS agent is correctly installed and communicating with the UserLock service.
For more information, see the guide to install the NPS agent.
Open the UserLock Console and go to Access Policies ▸ Add Policy.
Follow the general steps described in Configure an access policy until you reach the Policy type selection.
Choose Multi-factor authentication to open the MFA policy form.
)
Set MFA application to Enabled.
Choose configuration mode:
All at once (same settings for all session types)
Distinct setting per session type (recommended, so you can configure MFA separately for VPN connections).
Configure VPN session rules
For Connection type, choose whether MFA applies to all VPN logons, only remote ones, or only from outside IPs.
For MFA frequency, select how often MFA is required (at every logon, at first logon of the day, when connecting from a new IP, etc.).
Save the rules
The policy is now active and will enforce MFA on VPN connections.
Note
For the detailed meaning of the Connection type and MFA frequency options, see the MFA policies reference.
VPNs supporting RADIUS Challenge show a second MFA prompt after credentials.
Both RADIUS authentication and accounting must use the NPS server, with PAP authentication enabled.
Note
Supported VPNs include OpenVPN, Palo Alto, Fortinet, and Pulse Secure.
⚠️ For Push MFA, UserLock waits up to 5 minutes for validation. If no response, a challenge prompt appears for the user to enter an OTP code manually.
In the UserLock console ▸ Server settings ▸ Advanced ▸ Multi-Factor Authentication, set:
MFA VPN Challenge = TrueEnsure your VPN server uses PAP as the authentication protocol.
The user connects to the VPN and enters credentials.
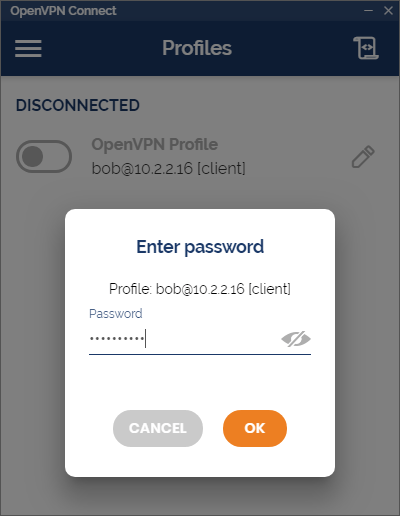
The VPN prompts for an OTP or Push confirmation.
)
Access is granted once MFA is successfully validated.
For Microsoft RRAS servers or VPN servers compatible with the Microsoft VPN client, you can use the UserLock VPN Connect app which provides a seamless MFA workflow and enrollment.
Deploy the VPN Connect app on client computers.
Install the UserLock MFA IIS module to allow remote enrollment.
Configure the RRAS server to use RADIUS authentication with your NPS server.
On the first VPN connection, the app detects missing enrollment and opens the UserLock MFA registration page (via UserLock MFA IIS module).
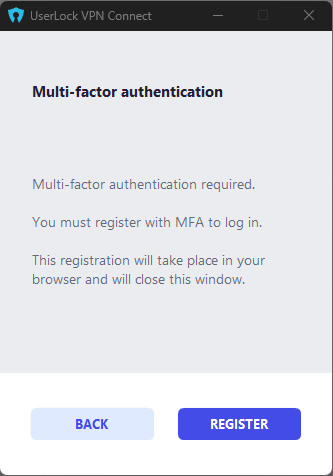
Users register and select their preferred authentication method (Push or OTP).
On subsequent logons, MFA is requested automatically, either via Push approval or OTP entry.

When using MS-CHAPv2, users can append their MFA code directly to the username during authentication.
Ensure a valid policy grants VPN access to the appropriate users.
)
Add the corresponding Active Directory group under Conditions.
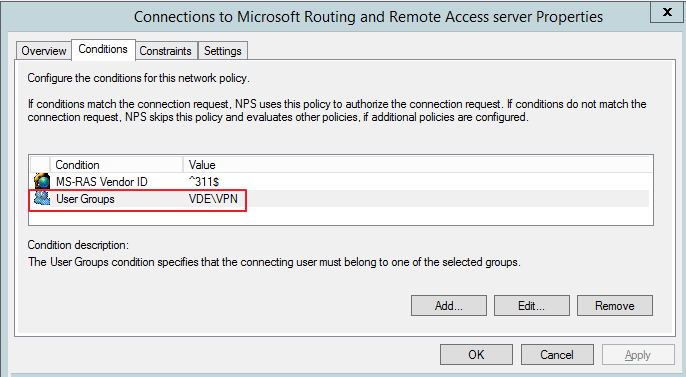
VPN type: Automatic
Authentication: MS-CHAPv2
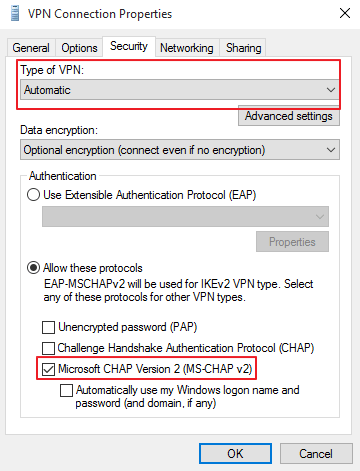
At login, users must enter:
Username:
DOMAIN\user,123456Password:
password
Note
✅ Separate the username and MFA code with a comma.
💡 Enter the MFA code last, as it changes periodically.
🔑 For TOTP/HOTP tokens, type the comma, then press the key to input the OTP.
If the VPN uses PAP, the MFA code must be added to the password field.
Note
⚠️ Use this method only when encryption is already applied (for example, L2TP/IPSec or SSTP).
❌ Do not use PAP with PPTP.
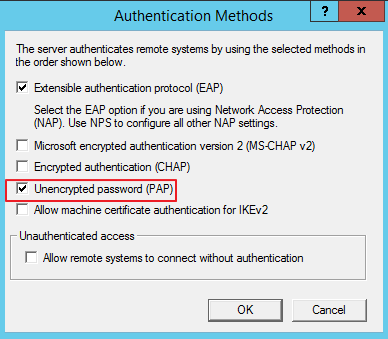
On the NPS server, select only Unencrypted authentication (PAP, SPAP).
)
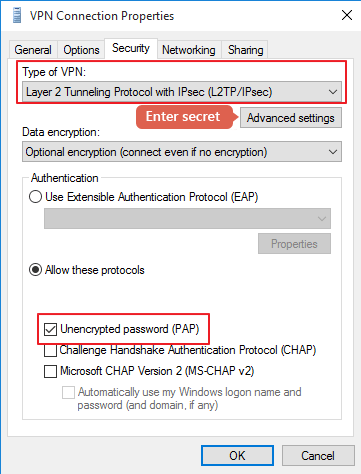
In RRAS:
Configure a pre-shared key for L2TP.
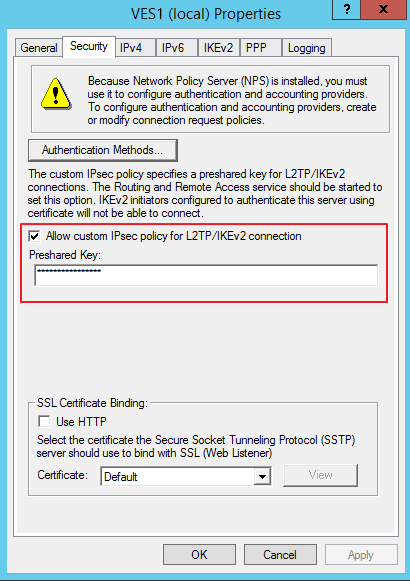
Select PAP as the authentication method.
Connection type: L2TP with IPSec
Enter the pre-shared key.
Authentication: PAP
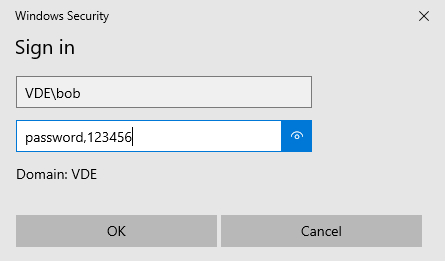
At login, users must enter:
Username:
<Domain>\<username>Password:
<password>,<MFA code>
Note
✅ Separate the password and MFA code with a comma.
💡 Enter the MFA code last, as it changes periodically.
🔑 For TOTP/HOTP tokens, type the comma, then press the key to input the OTP.
When using MFA Push with VPN RRAS, both the VPN client timeout and the RADIUS server timeout must be longer than the MFA push timeout defined in UserLock.
This ensures the VPN connection remains active while the user validates the push notification.
VPN client timeout (Microsoft VPN)
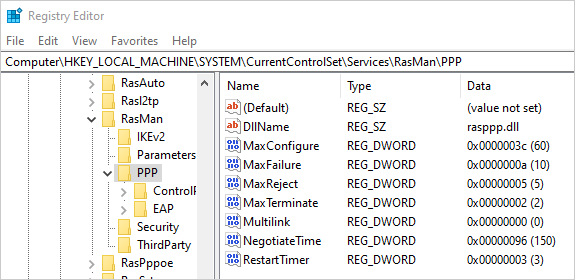
On the client computer, adjust the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\PPP\MaxConfigureType: REG_DWORD
Value: Timeout in seconds (default:
10)
RADIUS server timeout (RRAS)
On the RRAS server, the RADIUS timeout can be configured in the RADIUS server settings.
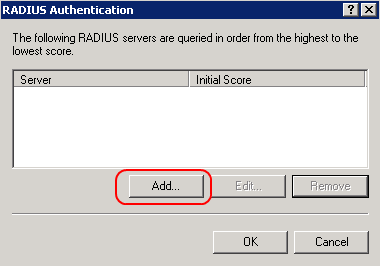
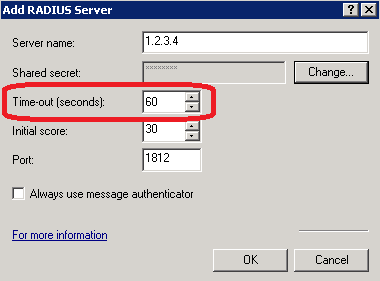
Note
If the NPS server is installed locally it cannot be changed in the RRAS administration console.
After enabling MFA for VPN sessions, users may be prompted again for credentials when accessing shared folders over VPN.
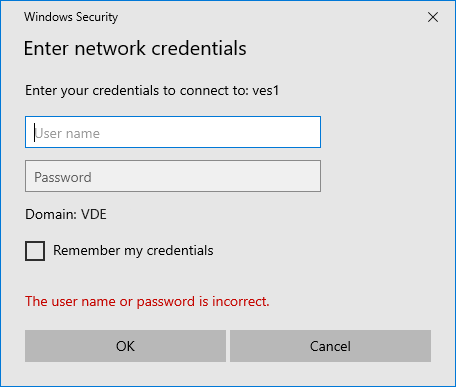
To avoid this, if the client machine is member of the Active Directory :
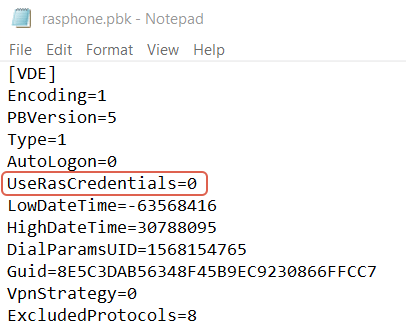
On the client machine, open:
%USERPROFILE%\AppData\Roaming\Microsoft\Network\Connections\PbkEdit rasphone.pbk file.
Set this value in the section related to the VPN connection:
UseRasCredentials=0
)
)
)
)
)
)
)
)
)
)