Configure Google Workspace for UserLock SSO
Secure Google Workspace logins with UserLock Single Sign-On (SSO) to enforce corporate authentication policies while simplifying access for users.
This guide explains how to integrate Google Workspace with UserLock Single Sign-On (SSO) using the SAML 2.0 protocol.
Once configured, Google Workspace logins are authenticated by UserLock against Active Directory. This provides a seamless sign-in experience and allows administrators to enforce UserLock access policies (MFA, time, machine, or location restrictions) to SSO sessions.
🚩️ Before starting:
You need a Google Workspace account with super-administrator rights.
UserLock SSO must already be installed and configured.
Log into the Google Admin console at https://admin.google.com.
Go to Security ▸ Authentication ▸ SSO with third party IdP.
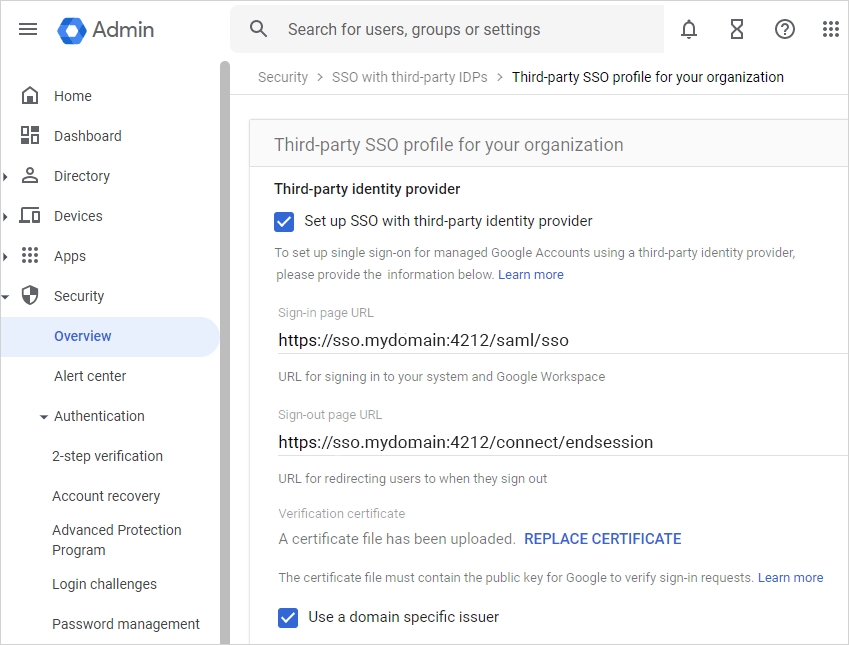
In Third-party SSO for your organization, check Set up SSO with third-party identity provider.
Fill the fields with your UserLock SSO values:
Settings
Values
Sign-in page URL
https://sso.<yourdomain>.com/saml/ssoSign-out page URL
https://sso.<yourdomain>.com/connect/endsessionVerification certificate
Go to UserLock console▸undefined️ Server Settings▸ Single Sign-On
Click on Download ▸ SAML certificate.
Open it in a text editor, and paste the contents here

(Recommended) Enable Use a domain-specific issuer.
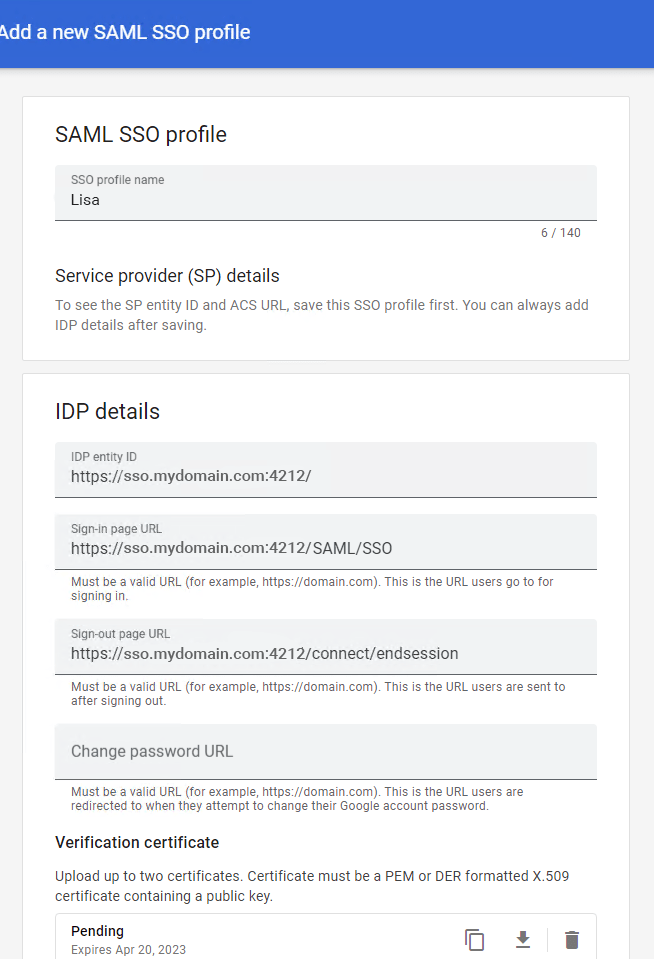
In Third-party profiles, click ADD SAML PROFILE.
Define the Entity ID, Sign-in page URL, Sign-out page URL, and upload the UserLock certificate.
Save the profile.
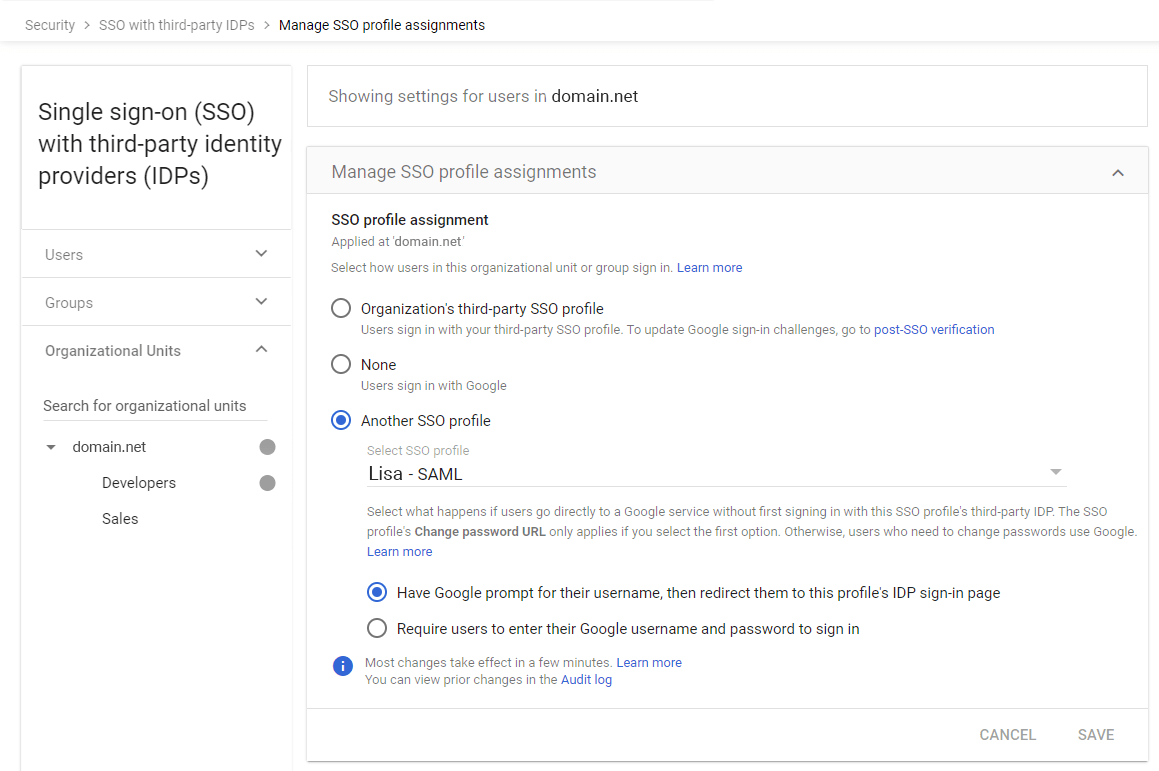
Go to Manage SSO profile assignments.
Choose the desired option:
Organization's third-party SSO profile (global application).
Another SSO profile (OU- or Group-based).
None (SSO disabled, users sign in with Google credentials).
In the UserLock console, go to ⚙️ Server settings ▸ Single Sign-On.
Click on the Google row.
Fill the fields:
Settings
Values
Email Domain
Domain used for Google Workspace logins.
Émetteur
Your Google Workspace instance domain (e.g.
google.com/a/sso.mydomain).ACS URL
e.g.
https://google.com/a/sso.mydomain/acs.
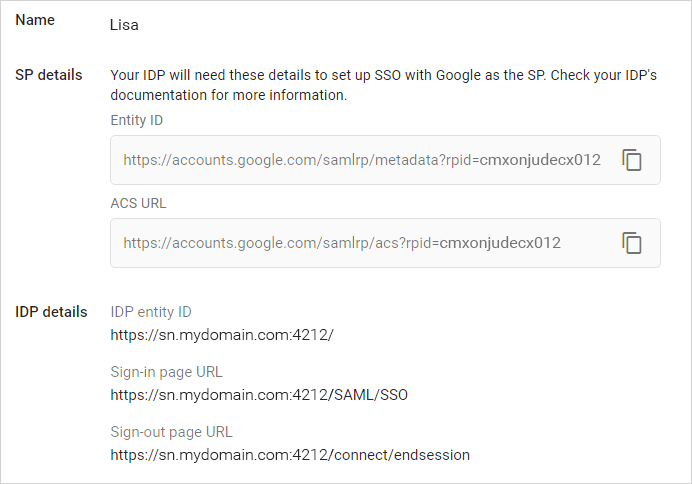
From the Google Admin console, copy the Entity ID and ACS URL from the SP details of the chosen SSO profile.
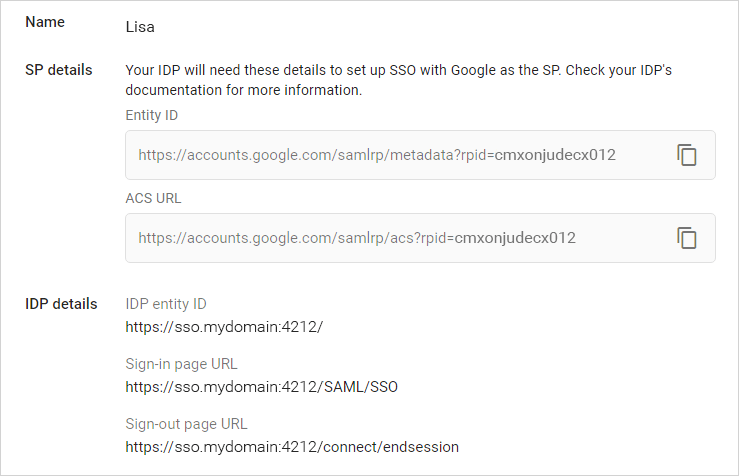
Paste them into UserLock.
For common issues, see Troubleshooting SSO.
If the problem persists, please contact IS Decisions Support.
SSO can be disabled in emergencies. Super-administrators can always log in with their full Google admin email address and password.
To disable SSO in Google Workspace:
Log into the Google Admin console at https://admin.google.com.
Go to Security ▸ Authentication ▸ SSO with third party IdP.
In Manage SSO profile assignments, select None.
Users will then sign in with their regular Google credentials.
You can extend the security of SSO sessions by applying UserLock access policies in addition to authentication.
Apply MFA on SaaS connections to require stronger authentication.
Hour restrictions: define when users are allowed to connect.
Geolocation rules: enforce access policies based on user location.
Session limits: allow or deny SaaS logins entirely for specific users.