Apply MFA to UAC prompts
Add multi-factor authentication (MFA) to Windows User Account Control (UAC) prompts to secure privilege elevation requests.
UserLock can enforce Multi-Factor Authentication (MFA) when a user attempts to perform an administrative task that triggers a Windows User Account Control (UAC) prompt.
This ensures that elevated actions are approved only after a verified second factor, preventing unauthorized privilege escalation on local or remote sessions.
Typical UAC scenarios include:
Local administrator actions such as software installation, system configuration changes, or user rights modifications.
Privileged scripts or tools that prompt for UAC elevation when executed by support teams.
By enforcing MFA on these elevation events, you ensure that only verified users can perform administrative tasks, even if administrative credentials are already known or compromised.
Before enabling this feature:
✅️ Install the Desktop agent on supported systems (Windows 10 build 1809 or later, or Windows Server 2019 and later).
✅️ The UserLock Desktop agent must be installed on the workstation or server.
✅️ In Admin Approval Mode, the UAC prompt behavior for administrators must be set to Prompt for credentials or Prompt for credentials on the secure desktop.
✅️ The UAC prompt behavior for standard users must be set to Prompt for credentials or Prompt for credentials on the secure desktop.
Note
MFA can only be enforced if the system is configured to Prompt for credentials or Prompt for credentials on the secure desktop.
See Microsoft documentation:
To enforce MFA on UAC connections, you need to create a new access policy.
Open the UserLock Console and go to Access Policies ▸ Add Policy.
Follow the general steps described in Configure an access policy until you reach the Policy type selection.
Choose Multi-factor authentication to open the MFA policy form.
Set MFA application to Enabled.
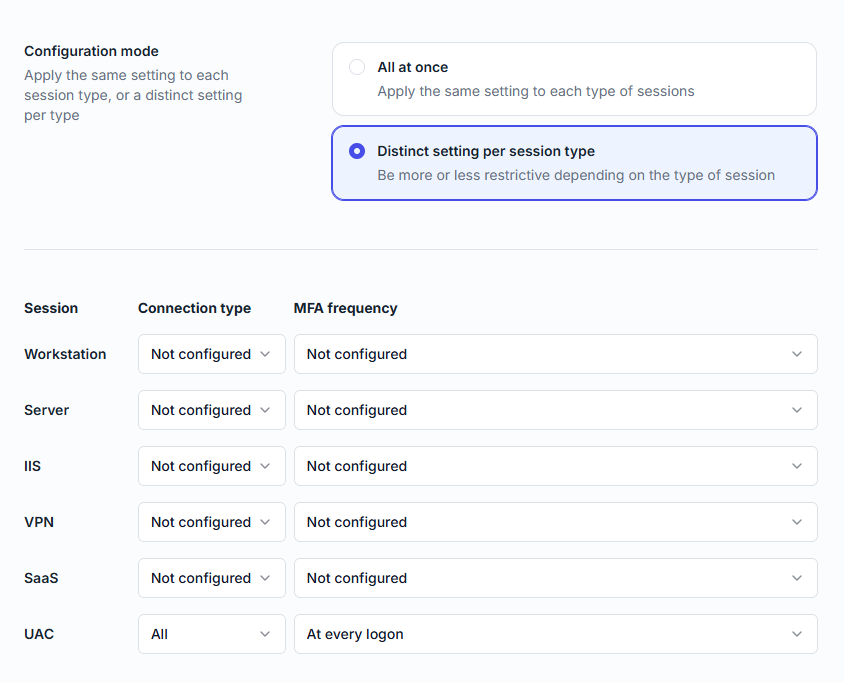
Choose configuration mode:
All at once (same settings for all session types)
Distinct setting per session type (recommended for UAC, so you can configure MFA separately for SaaS connections).
Configure UAC session rules
For Connection type, choose whether MFA applies to all UAC logons, only remote ones, or only from outside IPs.
Choose All (recommended) to apply MFA to any UAC elevation request, regardless of network location.For MFA frequency, select how often MFA is required (at every logon, at first logon of the day, when connecting from a new IP, etc.).
Choose At every logon to ensure MFA is required each time a UAC prompt appears.
Save the rules
The policy is now active and will enforce MFA on UAC prompts.
Note
For the detailed meaning of the Connection type and MFA frequency options, see the MFA policies reference.
These connections are compatible with all MFA methods: Push, TOTP code, and USB security key.
User enrollment for MFA cannot be done via UAC prompts.
Apply this feature only to accounts with administrative privileges.
Use Push or TOTP for faster MFA approval during frequent admin operations.
Test the configuration after Windows updates to confirm compatibility.
For deployment recommendations (pilot groups, communication, monitoring) and to know how users can enroll before applying MFA to UAC prompts, see the guide Apply MFA to Windows sessions.