Reporting
The Reporting pages provide detailed audit trails of all user and machine activity collected from protected machines. Reports can be viewed in real time, exported on demand, or scheduled for automated delivery.
Policies reports provide detailed logs of Multi-Factor Authentication (MFA) events and logon attempts denied by access policies. They help administrators monitor access control and identify potential security risks.
The following reports are included:
MFA events: all MFA attempts (success, failure, skipped, cancelled, help requests).
Denied logons: failed or denied logon attempts, whether blocked by Active Directory (e.g., bad password) or by UserLock access policies (e.g., unauthorized machine, hours, quota, geolocation, group limits).
Typical use cases
Identify repeated MFA failures that may indicate suspicious behavior.
Detect users skipping MFA configuration or requesting help too often.
Monitor denied logons to verify that access policies are enforced correctly.
History reports provide a detailed timeline of user activity and session events across the network.
The following reports are included:
Events timeline: all session events in chronological order.
Session history: complete log of user sessions (open, closed, incomplete).
Simultaneous sessions: domain users with overlapping sessions.
Single Sign-On events: SSO activity by user or application.
Wi-Fi / VPN sessions: network sessions by connection type (with RADIUS if configured).
IIS sessions: web application activity by pool or application name.
UAC events: granted or denied privilege escalation requests.
User status changes: transitions between statuses (e.g., risky).
Typical use cases
Trace a user’s full activity timeline to investigate incidents.
Identify users with multiple simultaneous sessions that may bypass restrictions.
Review VPN or Wi-Fi connections to ensure compliance with remote access policies.
Audit Single Sign-On events for visibility into SaaS access.
Track User Account Control (UAC) prompts for privilege escalation attempts.
Working hours reports summarize user activity over time, including daily, weekly, and monthly breakdowns. They highlight when users are active, inactive, or connected outside authorized hours.
The following reports are included:
History: daily overview of hours worked.
Statistics: average logon/logoff times, active and locked durations.
Week / Month: aggregated activity for a period, per user.
Unauthorized: activity outside authorized working hours.
Typical use cases
Verify compliance with authorized working hours policies.
Detect abnormal overtime or suspicious night/weekend activity.
Provide HR or compliance teams with activity statistics.
Note
Locked session times are counted between first logon and last logoff of the day.
IIS sessions are excluded from these reports.
Administration reports provide audit logs of administrator actions and configuration changes.
They ensure accountability and support compliance requirements.
The following reports are included:
Actions: log of administrator operations such as agent installations, machine reboots, user MFA resets, or session terminations.
Configurations: changes to access policies, MFA settings, user blocks/unblocks, or server settings/updates.
Typical use cases
Track changes to access policies or server settings.
Monitor administrator actions on sessions, users, or machines.
Provide audit evidence for compliance reviews.
Every report in UserLock supports flexible customization to fit your monitoring needs:
Views | Each report provides predefined views for common scenarios. You can save your own report views with tailored filters and settings. |
|---|---|
Columns | Any report column can be shown or hidden, depending on your needs. |
Filters | All reports can be filtered on available columns (e.g., by user, machine, domain, event type, country, organizational unit). |
Grouping | Results can be grouped by attributes such as user, machine, date, or session type, helping to summarize large datasets. |
All reports can be exported in PDF, Excel (XLSX), or CSV formats.
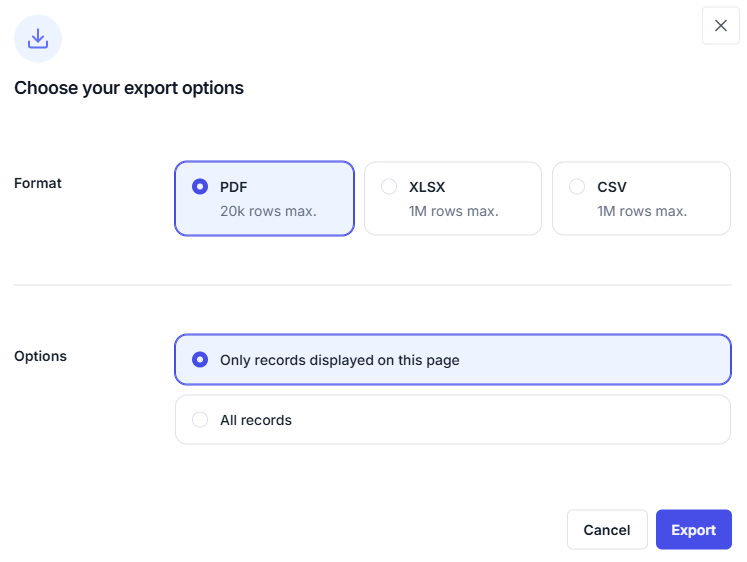
Typical use cases
Share audit evidence with compliance teams.
Provide managers with scheduled weekly activity summaries.
Export raw data to Excel or CSV for further analysis.
Note
Exported file is saved to the server’s Export folder, the exports behave differently depending on the console:
Windows Console: le dossier contenant le fichier exporté est ouvert.
Web Console: PDFs open in a new tab, Excel and CSV files are downloaded by the browser and the file is automatically deleted from the server directory.
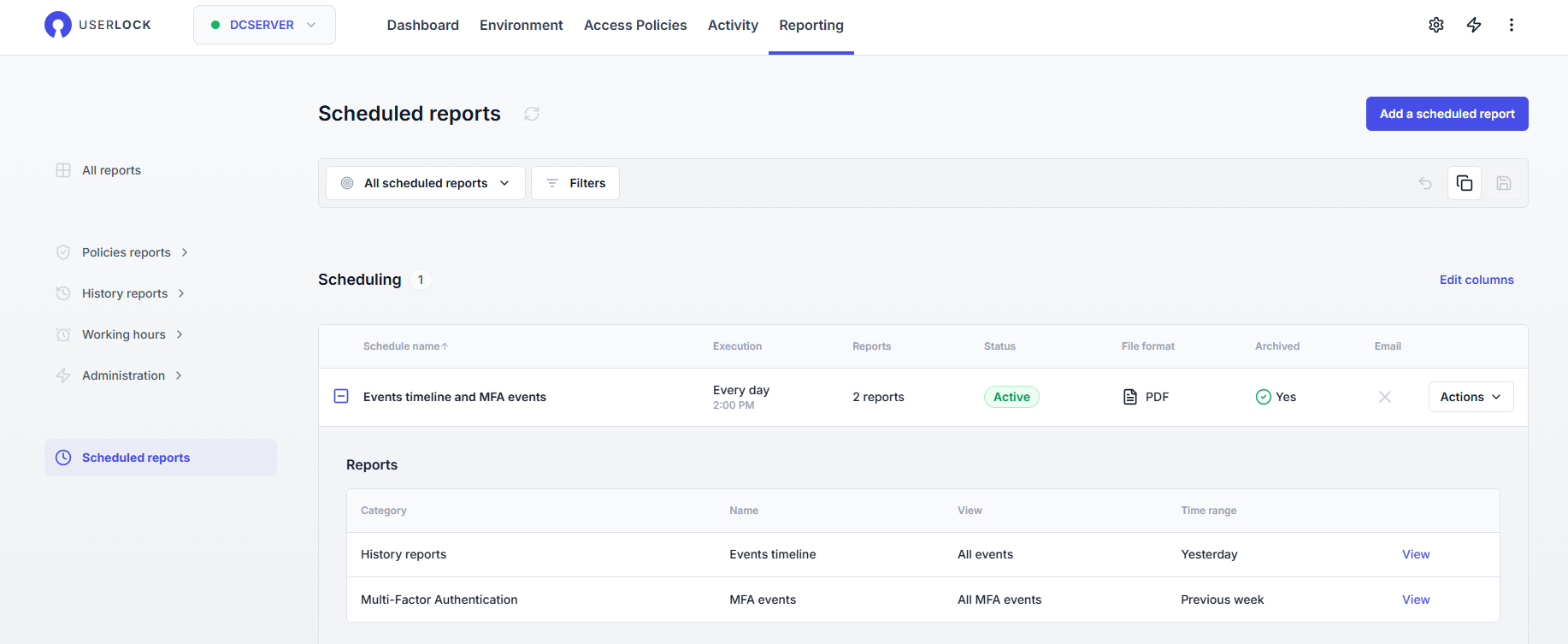
Reports can be scheduled for automatic delivery or archival.
Schedules are based on saved report views, and define:
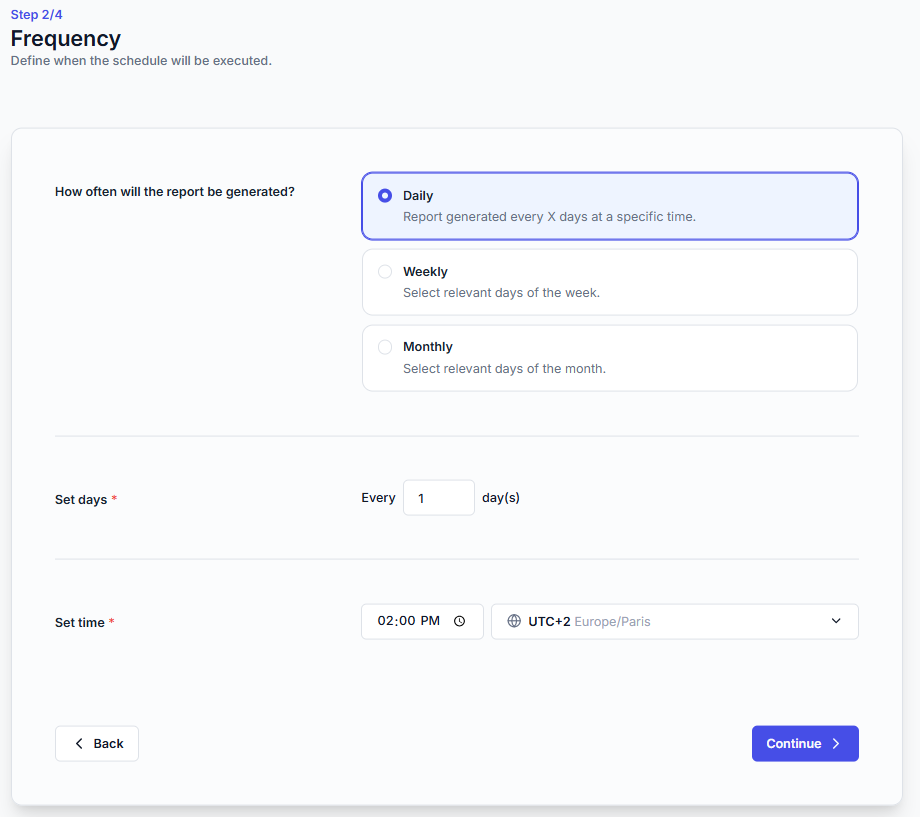
Frequency: daily, weekly, or monthly, with time and time zone settings
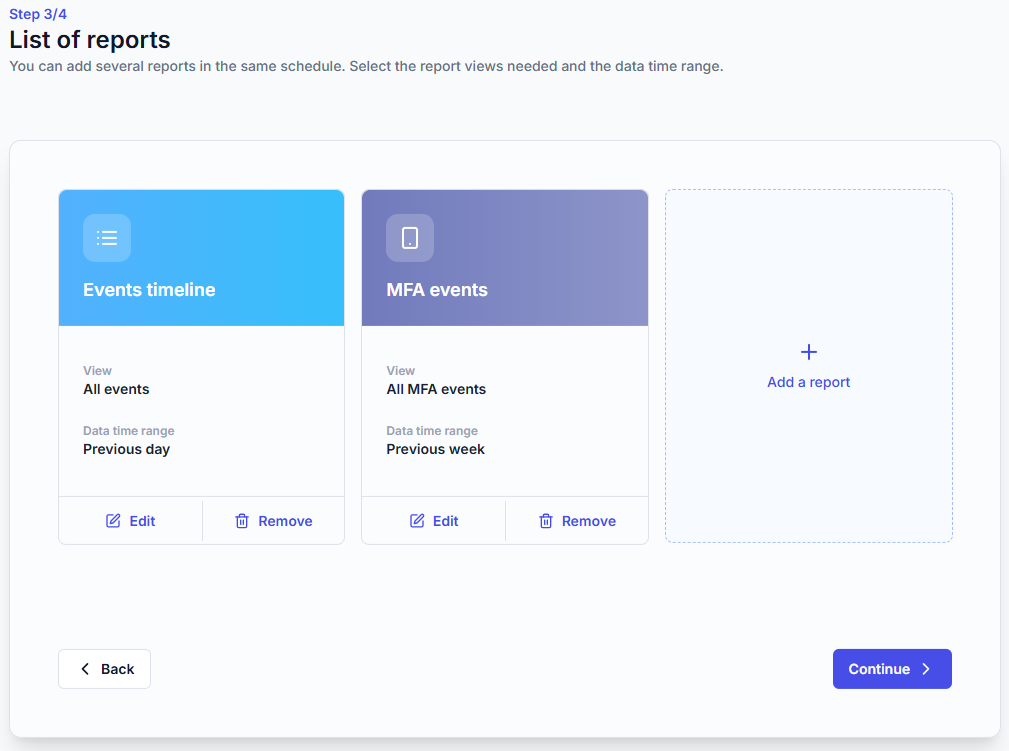
Reports included: one or more reports, each with a time range and selected view.
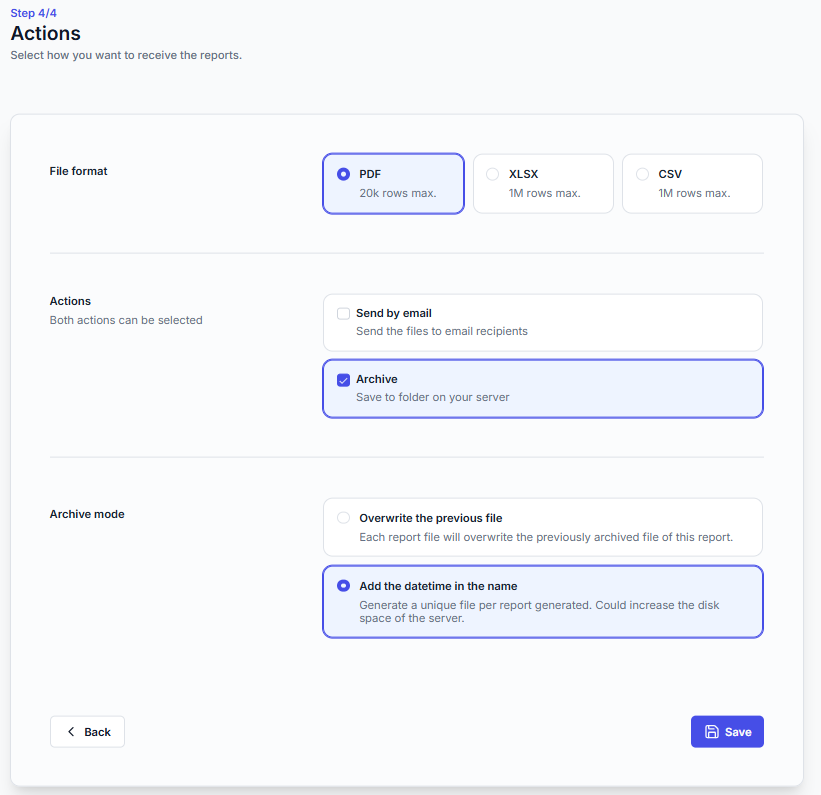
Actions:
Send by email: define recipients, subject, and body options. Ensure your email settings are correctly configured.
Archive on server: save files in a chosen folder, with overwrite option
Formats: PDF, Excel (XLSX), or CSV
All schedules are listed in the Reporting section, where they can be edited, deactivated, or deleted. From the list, a View link opens the exact report with its filters and settings.
Typical use cases
Automate compliance reporting by sending weekly denied logons to auditors.
Provide managers with monthly working hours reports by email.
Archive all administrator actions daily to maintain an audit trail.