Geolocation restrictions
Geolocation restrictions control remote logons based on the user’s country.
Useful resources
Block logons from countries where the organization has no presence.
Allow access only from the company’s home country.
Detect and deny suspicious connections originating from unexpected regions.
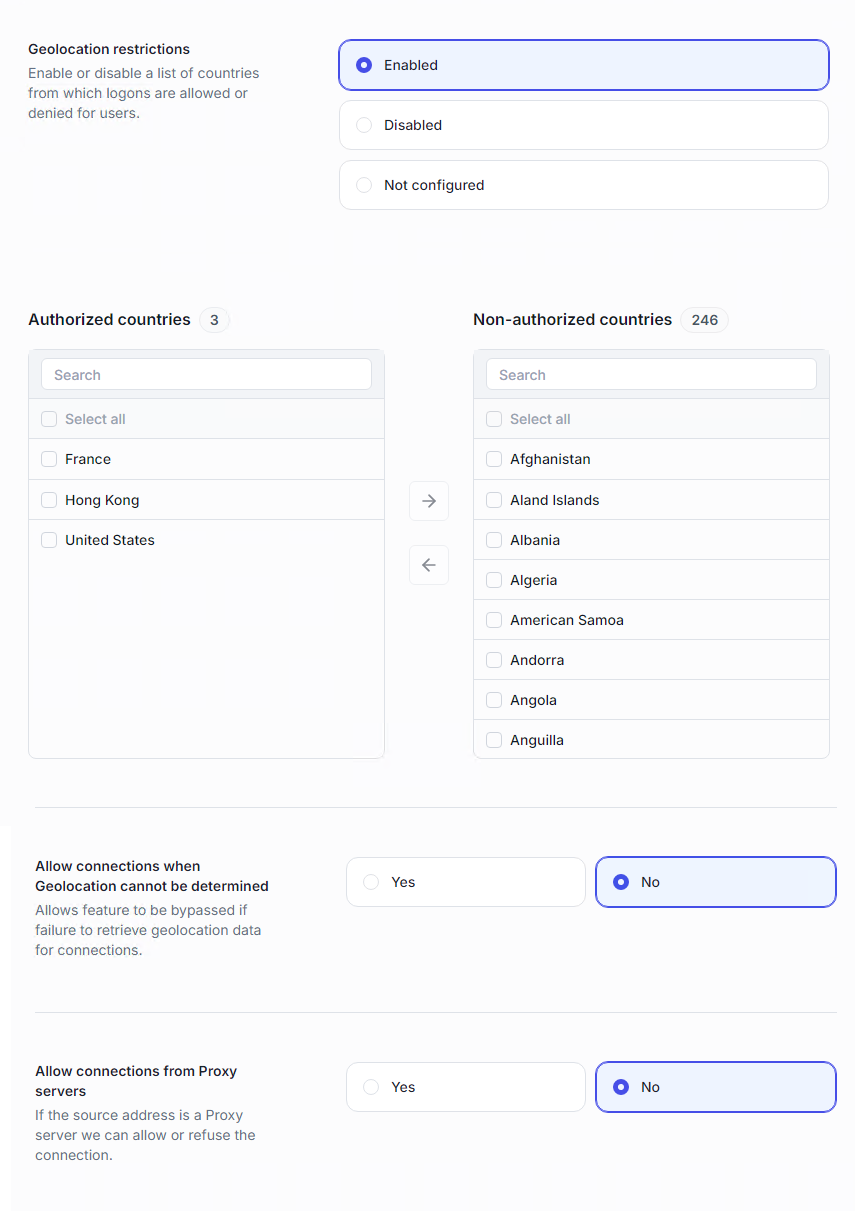
You can maintain a list of authorized and denied countries. Users outside authorized countries are blocked.
When geolocation cannot be determined (for example, if the IP is missing from the database), you can choose to allow or deny the connection. Allowing avoids accidental lockouts, but may lower security.
Proxy servers can hide the real origin of a connection. You can explicitly choose whether to allow or block logons coming through known proxies. Best practice: deny proxies unless business requirements justify them.
Geolocation is determined from the public IP address using an internal database. If the address is in a private range (10.x, 172.16–31.x, 192.168.x), it cannot be geolocated.
For users connecting through RD Gateway, install the NPS Agent on the NPS server handling RD Gateway authentication, so UserLock can retrieve the real client IP.
A list of all geolocation policies is available in the Access Policies section, under the Geolocation page.
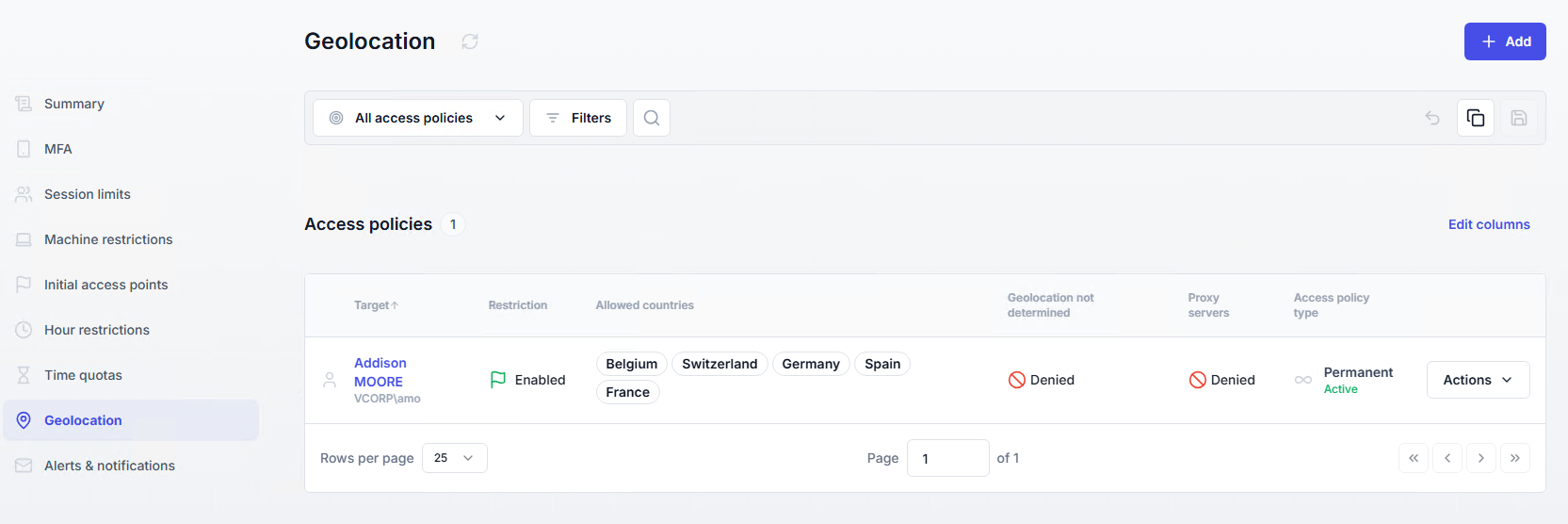
If your organization operates from a limited set of countries, use geolocation restrictions to block access from anywhere else.
This greatly reduces your exposure to unauthorized remote logons.
For example, you can allow access only from your company’s home country and block connections from all others.
To strengthen protection, you can also:
Block logons through proxy servers, which often hide the true origin of a connection.
Deny connections when geolocation cannot be determined, to avoid potential bypass attempts.
This setup ensures that only legitimate users, from expected locations, can access your network resources.