Restrict Active Directory user logon hours & force logoff on a Windows server domain
Enforce logon hour restrictions, maximum session length and time quotas for all Active Directory users. Go beyond native controls and set by group, on different session types and force logoff when outside of authorized timeframes.
Logon time restrictions far beyond native Windows controls
Manage the hours and days that any user, or group of users, can log on to a Windows Server domain. Implement effective login controls that improve network security, without slowing down productivity.
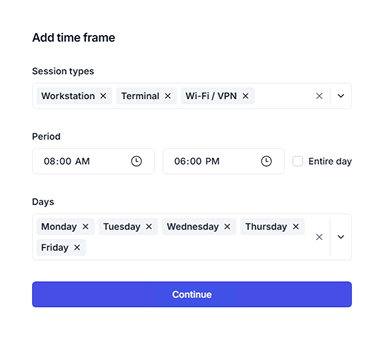
Logon hour restrictions
For a defined time period, set logon hours as either authorized or denied for different session types.
Use case example 1
For a group of users deny any interactive logon outside business hours
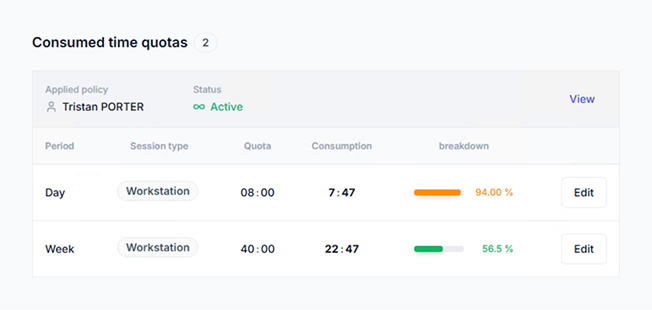
Session time quotas
Authorize a maximum period of time (hours and minutes) a user or user group can stay connected, per day, week or month, for different session types.
Use case example 2
For a group of users, enforce working hours per week by workstation session usage.
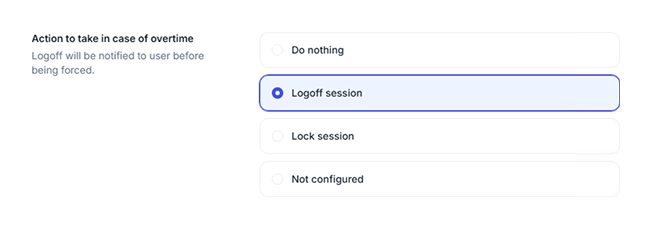
Force logoff when logon hours expire
Using native controls, there is no way to force a user to log off an interactive logon session when their time quota expires.
But with UserLock, an administrator can automatically logoff users outside of authorized timeframes, or when a time quota is up.
Display a custom warning notification to users before UserLock initiates the session logoff.
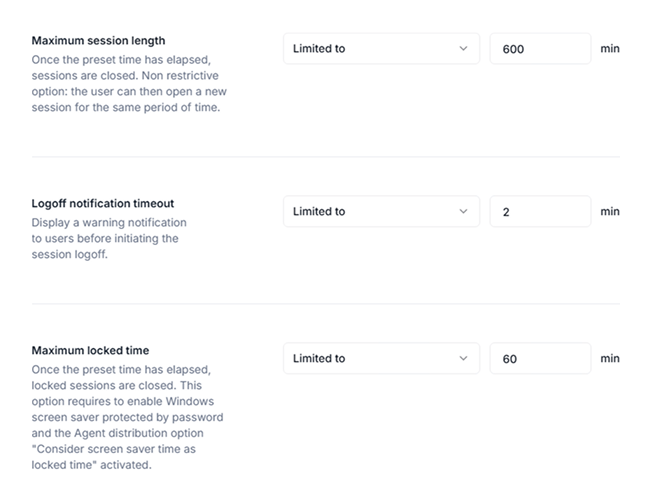
Force logoff & idle session time limit
Automatically logoff sessions after a specific idle time. This forced logoff helps protect shared workstations that are left open and increase security and compliance risks.
Use case example 3
Logoff every open session by any member of a group after an idle period of 20 minutes.
Flexible policy options
Set by group
Unlike native Windows, UserLock allows logon time restrictions to be set for any user, group of users or Organization Unit.
Set by session type
Configure the time frames for different types of session (workstation, terminal, Wi-Fi & VPN and/or IIS).
Set maximum session length
When the time expires, the session will automatically logoff the user after showing a warning.
Set according to machine’s local time zone
Apply time restrictions according to each client machine’s time instead of the UserLock server time.
Track and report on logon activity
Get live and historic data on logon hours for all users on your network. UserLock records every connection event, across all session types, to give you a reliable view of when users are working.
With searchable, filterable reports, instantly see how many users are connected and for how long. Easily manage flexible schedules and remote work without adding to IT’s workload.
More context aware restrictions
Restrictions by time constraints work alongside the other UserLock contextual access restrictions (session type, number of simultaneous connections and origin) to best protect and secure Active Directory user access.
Session type
Control workstation, terminal, Wi-Fi, VPN and IIS sessions to protect both interactive sessions and network access for remote and mobile users.
Simultaneous connections
Limit the number of unique entry points and concurrent sessions to prevent simultaneous logins from a single identity.
Origin
Limit access by location with controls at workstation, device, IP range, organizational unit (OU), department and country.
Force remote logoff after idle time
Watch how IT administrators can set an automatic forced logoff, on all locked or open machines, after a certain idle time with UserLock. This includes remote desktop sessions opened by the domain user.
ReadLogin logout time tracking for employees
Learn how UserLock makes it easy to manage and react to employees’ attendance, overtime thresholds, productivity and suspicious login logout times.
ReadRemotely manage, respond and logoff Windows Session Events
UserLock allows administrators to easily track, manage and respond to Windows sessions remotely. Real time visibility and reaction to user activities, helps both optimize PC resources and save time.
Read)
)
)
)
)
)
)
)