Multi-factor authentication (MFA) methods
Keep multi-factor authentication (MFA) simple and low-friction. With UserLock, enable up to two secure MFA methods for users.

Choose the right MFA method for Active Directory
For IT teams managing access to on-premises or hybrid Active Directory (AD), MFA is crucial. Active Directory MFA must be low friction, flexible, and secure.
With UserLock, enable multi-factor authentication methods that fit your users, systems, and compliance needs. All without moving identity to the cloud or slowing down end users.
Here, we’ll walk through the secure MFA methods you can enable with UserLock, their benefits, and how they fit real-world access scenarios.
What are secure MFA methods?
MFA adds layers of security beyond the AD username and password. Different types of multi-factor authentication methods can verify an AD user's identity before they gain access.
All MFA methods fit under three types of MFA factors:
Something you know
a password or PINSomething you have
a smartphone or hardware keySomething you are
a fingerprint or facial scan
Not all forms of authentication are equally secure.
Common methods, such as SMS (text message) and email authentication (email address), are particularly vulnerable to compromise.
UserLock focuses on “something you have”
UserLock focuses on factors that are practical, secure, and easy to deploy across AD environments.
Which MFA methods does UserLock support?
With UserLock, enable up to two secure MFA methods per user, adapting to different user needs and login scenarios.
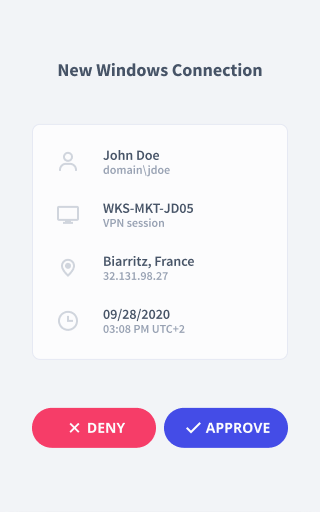
Push notifications (via UserLock Push)
Approve login attempts with a tap
When users login, they receive a push notification on their smartphone through the UserLock Push app.
With one tap, they can approve or deny access to complete MFA.
Scales easily across any number of users
Minimizes push fatigue and accidental approvals
Works offline with fallback TOTP codes
Common use cases:
General workforce, remote access, easy user adoption

Hardware security keys
Plug in or tap to authenticate
Give users a highly secure method for strong authentication with physical security keys like YubiKey or Token2.
The user must physically have the key, making it difficult for threat actors to bypass this type of MFA.
Phishing-resistant MFA
Ideal for privileged access
Supports strict regulatory compliance
Common use cases:
High-risk roles, IT administrators, privileged access,
compliance requirements

Authenticator apps (TOTP)
Enter time-based one-time passwords (TOTP)
Support TOTP authentication with popular authenticator apps such as Microsoft Authenticator or Google Authenticator.
These apps generate a 6-digit code (the TOTP) every 30 seconds.
Once users install the authenticator app on their mobile device, they can enter this code to complete UserLock MFA.
Quick setup and enrollment
Works offline
Protects from human error
Common use cases:
BYOD environments, flexible deployment needs, remote users

Windows Hello for Business
Implement passwordless MFA
Replace the traditional password with WHfB’s fingerprint scan or facial recognition. Combine WHfB with UserLock to enable any form of MFA above as an additional authentication factor.