The importance of implementing multi-factor authentication (MFA) for remote employees
Secure machine, network, and cloud access with multi-factor authentication (MFA) for remote employees.
Updated June 4, 2024)
It's been four years now since the pandemic disrupted traditional perimeter-based network security. Now, organizations are stabilizing their security protocols for hybrid and remote teams, which includes implementing MFA for remote employees.
With UserLock, you can enable effective MFA for remote work, even when the employee doesn't connect to the domain via VPN, or even to the internet.
When the four office walls defined your security perimeter, your physical office space and managed corporate network defined the work environment. Under the old "castle and moat" security model, occasional remote access via VPN was mandatory.
Now that remote work has exploded the perimeter security model, organizations have run en masse to adopt zero trust security principles. Zero trust focuses security on access, with the mantra to "trust nothing, verify everything." It sounds simple, but implementing a zero trust framework is often from from it.
And when remote employee laptops are not secured properly, they can provide entry points for malicious threats, which then leads to access to your organization's IT resources, such as files and folders.
Your remote employees' Windows logon also serves as an initial access point to your Active Directory, a key resource that's a common target for cyber attacks.
Setting up two-factor authentication (2FA), also called MFA, adds an extra layer of security when your remote user logs into your system. The challenges that face IT teams when implementing MFA are amplified for remote work. Here are a few of the most common.
Remote employees need to access a wide array of internal resources remotely to do their job. This ranges from multiple environments, applications, which might be in the cloud (SaaS) or on-premise, to Windows file servers. This often leads to password fatigue, and adding a second factor only makes it worse. Ironically, MFA fatigue can actually counter the extra security you're trying to put in place. Not only do you need MFA that authenticates your remote employees at a single key point of access, but you need MFA that you can apply granularly so it doesn't get in the way of employees doing their job.
Not all MFA is designed to deploy remotely. Often, once admins set up MFA, users have to either set up MFA at the very first logon, or they can skip (sometimes indefinitely) and avoid onboarding altogether.
This can also be an issue for employees who will be authenticating with a hardware authentication device, like an MFA token or key. Giving your employees some flexibility around MFA enrollment is key to a smooth rollout — and it gives your IT help desk time to field requests without the overwhelm.
Since remote connections are vulnerable, it's common for IT to require MFA on all remote connections, all the time. That can be extremely frustrating for remote employees, who can face MFA challenges several times a day. For example, if the MFA policy requires a new login when a session times out, they may have to go through MFA each time they step away to grab a coffee.
UserLock addresses the common challenges for a remote MFA deployment above, since admins can choose how and when to require MFA.
There are two edit modes available for modifying the MFA settings. Make sure to read the documentation for the use case for each type of session to ensure users will receive an MFA prompt.
All session types at once: By selecting this option, you can apply the same policy for all session types that are protected by UserLock.
By session type: Select this option to apply different MFA policies for each session type.
)
)
)
)
)
)
)
Admins can also apply MFA by connection type.
)
)
)
)
)
)
)
For each session type, admins can also choose how often to prompt their users (including remote users) with MFA.
)
)
)
)
)
)
)
Since UserLock MFA secures Windows logins on remote machines, you can ensure you're applying MFA across all conditions, even when there is no secure VPN connection to the corporate network — and even when the user doesn't have an internet connection.
Here are a few common remote work scenarios that UserLock allows you to secure with MFA.
UserLock allows for several possible ways to enroll MFA on users who are working remotely outside of the corporate network.
Thanks to the UserLock agent, you automatically benefit from offline MFA. So you can ensure your MFA policies are being applied, even when remote employees don't have an internet connection.
By default, all of UserLock's MFA and access controls work without internet. Since most MFA solutions rely on an internet connection to synchronize with the identity provider (IdP), UserLock's offline capabilities set the solution apart for organizations looking to close security gaps as well as meet strict compliance requirements.
With remote working, users do not always connect to a VPN. But it's still important to secure those logons. That's why we created a web app, UserLock Anywhere for UserLock subscribers to apply MFA on VPN-less, off-domain Windows logons.
UserLock Anywhere allows the UserLock agent installed on a machine to stay in contact with the UserLock service through the internet. So, you can rest easy knowing your MFA and access management policies continue to be enforced on login for any user, regardless of what (managed) machine the user is remotely working on.
Even if UserLock Anywhere isn't enabled, the UserLock agent can still manage an off-domain access attempt on a machine where it's installed.
Administrators can configure UserLock to always allow, always deny, or request MFA for all offline, or off-domain connections. An option to "Force MFA" will deny access for users who are not yet enrolled in MFA.
)
)
)
)
)
)
)
A VPN works by establishing encrypted connections between devices that remain private even if they stretch across public internet infrastructure.
UserLock’s MFA for VPN sessions supports the Remote Authentication Dial-In User Service (RADIUS) Challenge. The RADIUS Challenge can prompt for the one time password in a separate second step, after the user has successfully entered their login credentials.
VPN solutions that support “RADIUS Challenge” include Open VPN, Palo Alto, Fortinet, Pulse Secure Connect SSL...
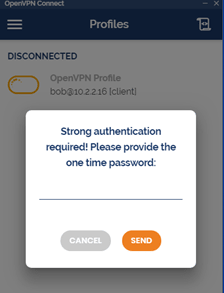
The Microsoft Remote Desktop Protocol (also known as RDP) is used to allow remote desktop to a computer. Remote Desktop Gateway (RDG or RD Gateway) is a Windows server role that enhances control by providing a secure encrypted connection to the server via RDP.
With UserLock MFA for RDP, administrators can define under what circumstances MFA is asked for these different RDP connections.
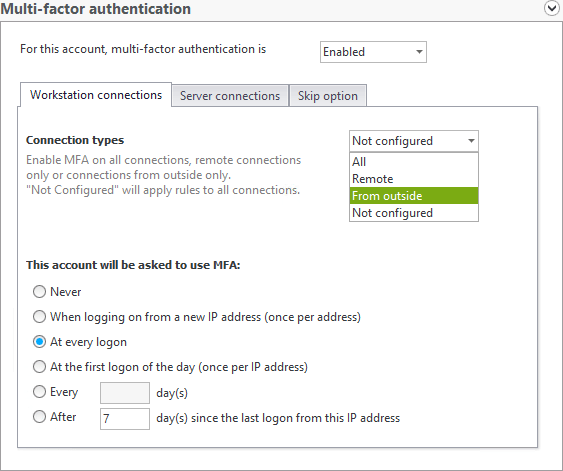
Administrators can first customize MFA on RDP logins based on whether an end-user is connecting to another machine from inside the network or from logons that originate from outside the corporate network.
Administrators can then choose to consider RDG connections as coming from inside or outside the network and define the circumstances for MFA.
RD Web Access is a way to connect to a remote desktop server — and access Remote Desktop Services — over the Internet without a VPN connection.
The RD Web connection component installs the necessary web pages and scripts to the Internet Information Services (IIS) server directory, giving users the Web page interface for their remote desktop. Users need just their AD credentials, a URL and a supported web browser to access desktops and applications.
With UserLock MFA for IIS, administrators can target any one or several web applications that need a second factor of authentication.
UserLock detects the servers where IIS is installed and can automatically deploy the UserLock IIS agent. The UserLock MFA feature must then be installed on the IIS Server and the UserLock MFA application added.
The website settings are then configured to redirect the user to enroll for MFA if not already done, and challenge for MFA before access to the IIS application is granted.
Outlook Web Access (OWA) allows users to access their own corporate mailbox over the internet- from outside the corporate domain — without having to log into a VPN.
With UserLock MFA for IIS, a second factor of authentication can be added to OWA connections as Exchange applications are supported by an IIS server.
UserLock detects the servers where IIS is installed and can automatically deploy the UserLock IIS agent. The UserLock MFA feature must then be installed on the IIS Server and the UserLock MFA application added.
The website settings are then configured to redirect the user to enroll for MFA if not already done, and challenge for MFA on all access to users email.
Note: UserLock can also protect Exchange Online (available as a standalone service or part of Office365) with MFA. See cloud-based resources.
DirectAccess allows connectivity for remote users to organization network resources without the need for VPN connections. With DirectAccess connections, remote client computers are always connected to your organization — there is no need for remote users to start and stop connections, as is required with VPN connections.
AlwaysOn VPN — the replacement for DirectAccess — automatically establishes a VPN connection any time an authorized client has an active Internet connection.
Both of these methods help secure the machine’s remote connection. Unlike a traditional VPN there is no prompt for user credentials.
Therefore with UserLock, MFA can continue to be prompted when the remote user is asked to identify themselves.
Organizations want remote users to have stronger security on their direct connectivity to cloud resources. Direct access can reduce the load on the network and improve user experience, but often at the expense of security.
Rather than backhauling these applications through the core network UserLock enables MFA combined with single sign-on (SSO) for secure and direct connectivity to cloud based applications.
By retaining Active Directory (AD) as the Identity Provider, UserLock SSO allows each user to log in only once - with their existing AD credentials. Combined with granular MFA, this ensures a second factor of authentication can be added to verify the identity of users, before they access the cloud.
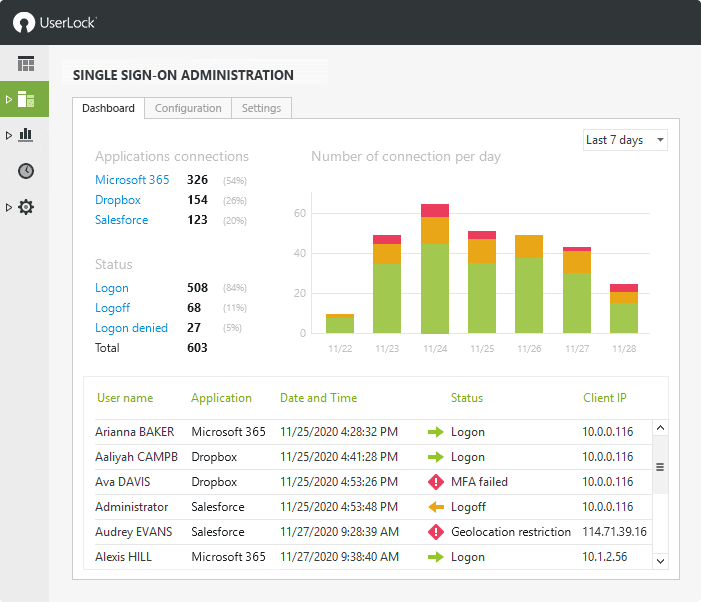
Access is immediately granted. UserLock SSO asserts the user’s identity to the cloud application and is authenticated without the user having to log in to the application. There is no difference whether inside the corporate network or working remotely.
(MFA can be requested again if required in the admin settings).
The user enters their corporate email address in the cloud application to login. UserLock SSO will then prompt the user for Windows domain login credentials (and a second authentication factor if enabled). The user is logged in successfully and redirected back to the application. There is no difference between a smartphone browser, a computer browser or a mobile app.
(MFA can be requested again if required in the admin settings).
Access is immediately granted. Multi-factor authentication can however be requested at each logon if required in the administrative settings.
Both before and after authentication, UserLock's contextual login restrictions and remote session management help further secure AD identity and secure remote access to all resources.
UserLock can restrict VPN access to just authorized company machines. Any other access attempt from any other machine is then denied.
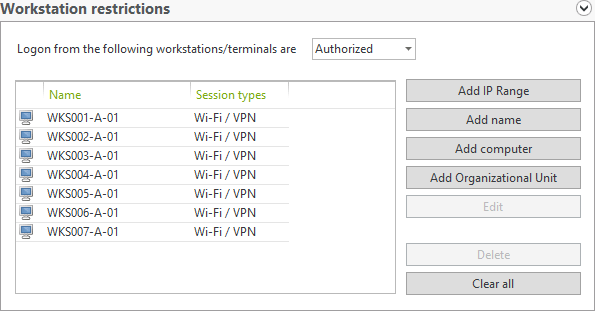
The geolocation restriction allows an administrator to restrict remote logons based on country (geolocation). The restriction will disallow/allow logons from a list of selectable countries.
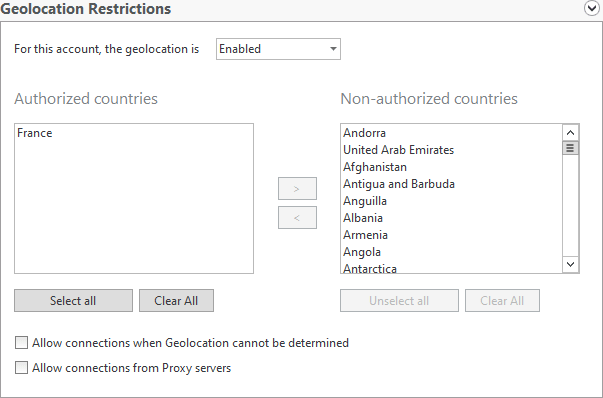
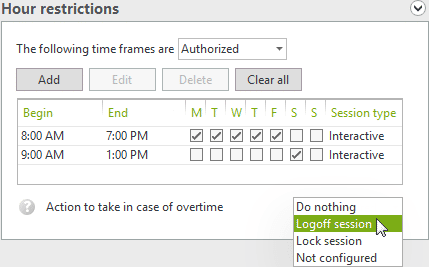
The rapid adoption of home working has meant many organizations can no longer apply time policies for network logons to reduce security risks or reduce unauthorized overtime.
UserLock Anywhere can continue to apply these restrictions even if the machine is outside the corporate network. The UserLock agent remains in contact with the service and can force the user to logoff if they have exceeded the working hours allowed.
"With remote access quickly becoming the rule rather than the exception, UserLock helps administrators alleviate the increased risk to security by protecting against inappropriate or suspicious access."
Remote work is here to stay. As IT adjusts to securing this new normal, the security solutions that win will help rein in your expanded attack surface.
The problem is, most MFA solutions are designed to help you check a compliance box. For example, most MFA solutions don't offer offline MFA by default. And if they do offer it, the offline mode has to be enabled (often by the user), and may only work for a few hours or days.
That's because most MFA solutions put identity authentication in the cloud. The trouble with that is, your attack surface increases exponentially as soon as you use a cloud-based identity provider (IdP). That's just how the security game works.
And when implementing MFA for remote employees, those vulnerabilities get put on loud speaker. UserLock is one of the only solutions on the market that offers effective MFA security on all conditions, which is critical for remote work. Far from just a solution to check an MFA box, UserLock offers meticulous, effective access security.
)
)
)