Active Directory MFA
Secure on-premises Active Directory (AD) identities with simple, secure Active Directory multi factor authentication (MFA). Make sure only the right user accounts gain access to network and cloud resources.
Take a tour of UserLock MFA

How does UserLock's multi factor authentication for Active Directory work?
With UserLock MFA, prevent unauthorized access, stop privilege escalation, and meet strict compliance requirements. No added complexity, no need to rewire identity infrastructure.
Apply UserLock MFA comprehensively across Windows logins, Remote Desktop, VPN, IIS, Microsoft 365 and SaaS, and UAC prompts.
Scale UserLock easily across large and small user bases thanks to granular session-based controls. You decide where the balance between security and productivity sits for your team.
Match MFA methods to user risk levels. UserLock supports push notifications, third-party authenticator apps such as Google Authenticator or Microsoft Authenticator, and hardware tokens such as YubiKey and Token2.
Work smarter with a straightforward MFA solution that IT and end users are happy to use.
How to apply Active Directory multi-factor authentication in any context
MFA for offline scenarios
With on-prem hosting, UserLock MFA enforces MFA policies, even when users logon from a device that isn’t connected to the internet.
MFA for off-LAN, off-domain connections
UserLock prompts remote employees for MFA even when devices are off the corporate network, ensuring secure off-domain access. Install the UserLock Anywhere web application for off-LAN MFA.
MFA for air-gapped networks
Enable secure Active Directory two factor authentication and access controls on air-gapped networks without outer internet connectivity.
Extend Active Directory MFA across all access points
MFA for Windows servers and AD domains
Apply MFA to all Active Directory devices and standalone terminal servers for secure access.
MFA for Microsoft Remote Desktop Gateway (RD Gateway) and RDP
Enable MFA on all Remote Desktop Services connections, including RDP logins and RD Gateway connections.
MFA for RemoteApp
Protect connections to RemoteApp sessions with MFA.
MFA for Virtual Private Network (VPN)
Secure VPN connections with MFA through RADIUS Challenge or Microsoft RRAS.
MFA for IIS (OWA, RDWeb, SharePoint)
Apply MFA on Microsoft IIS sessions to secure AD user access to Outlook on the Web (OWA), RDWeb, SharePoint, Microsoft Dynamics CRM, and other IIS apps.
MFA for SaaS apps
Combine MFA and Single Sign-On (SSO) to secure access to Microsoft 365, Exchange Online, AWS, Google Workspace, and other SaaS apps with SAML-2 authentication protocols.
MFA for Virtual Desktops
Add MFA on AD user access to virtual desktop infrastructure (VDI) using Windows OS, including Microsoft, Citrix, VMWare and more.
MFA for UAC prompts
Enforce MFA on Windows UAC (user account control) credential prompts displayed when launching administrative tasks.
Using Active Directory login MFA
When users enter an on-premises Active Directory username and password, these are validated with the Windows Domain controller or cached credentials on their device.
After the Active Directory credentials are verified, UserLock intervenes at the AD authentication layer to enforce MFA policies. Since UserLock integrates seamlessly with on-premises Active Directory, MFA is low maintenance: simple to set up and easy to manage.
Quick configuration
Set MFA policies by user, group, or organizational unit (OU), making setup fast and scalable — even across a large user base.
Seamless adoption
Control how and when end-users enroll in MFA, allowing them to skip enrollment for a set time to ensure a smooth rollout.
Effective application
Apply MFA policies in real-time, securing all connections — no matter where users connect from — thanks to UserLock's ability to detect new endpoints instantly.
Keep end users productive with easy MFA enrollment
Once the administrator enables MFA, end users can easily self-enroll thanks to UserLock’s simple self-enrollment process. Admins can also allow users to skip MFA enrollment until a specific date to allow for flexible onboarding.
How to self-enroll with the UserLock Push app
Install the UserLock Push app on a smartphone.
Scan the QR code.
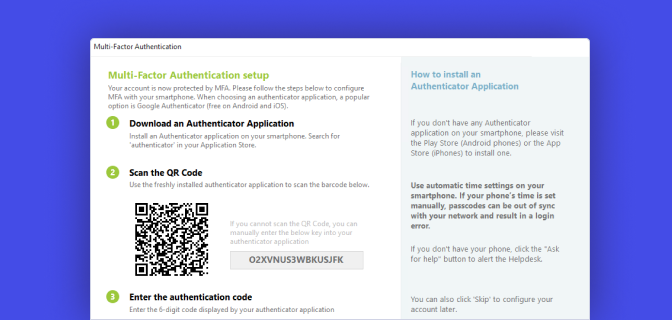
How to self-enroll with an authenticator application
Install an authenticator app on a smartphone.
Scan the QR code.
Enter a code to confirm activation.
How to self-enroll with hardware security keys (YubiKey, Token2)
Insert the key into the computer’s USB port.
Login to computer, confirm they want to use YubiKey (for example), and select the available YubiKey slot.
Click “Link YubiKey” to confirm configuration and press the YubiKey button. This automatically enters the code to confirm activation.
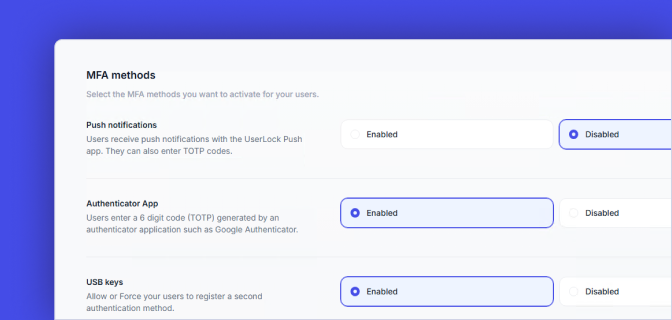
Multiple MFA methods
Choose to enable up to two MFA methods. All methods rely on secure cryptographic algorithms for Time-based (TOTP) and HMAC-based (HOTP) one-time passwords.
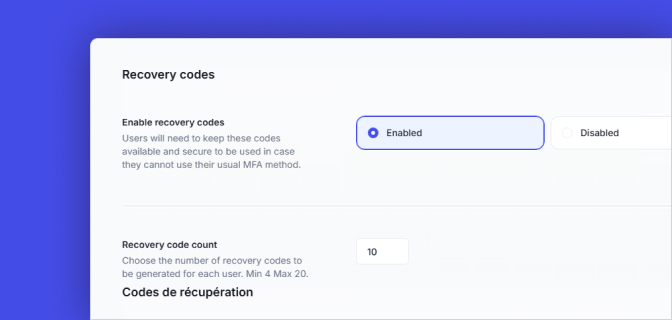
MFA recovery codes
After enrollment, admins can allow users to access a chosen number of MFA recovery codes. These serve as one-time passwords to validate MFA and regain access.
Remote MFA enrollment
Users can enroll for MFA even when working remotely, outside of the corporate network.
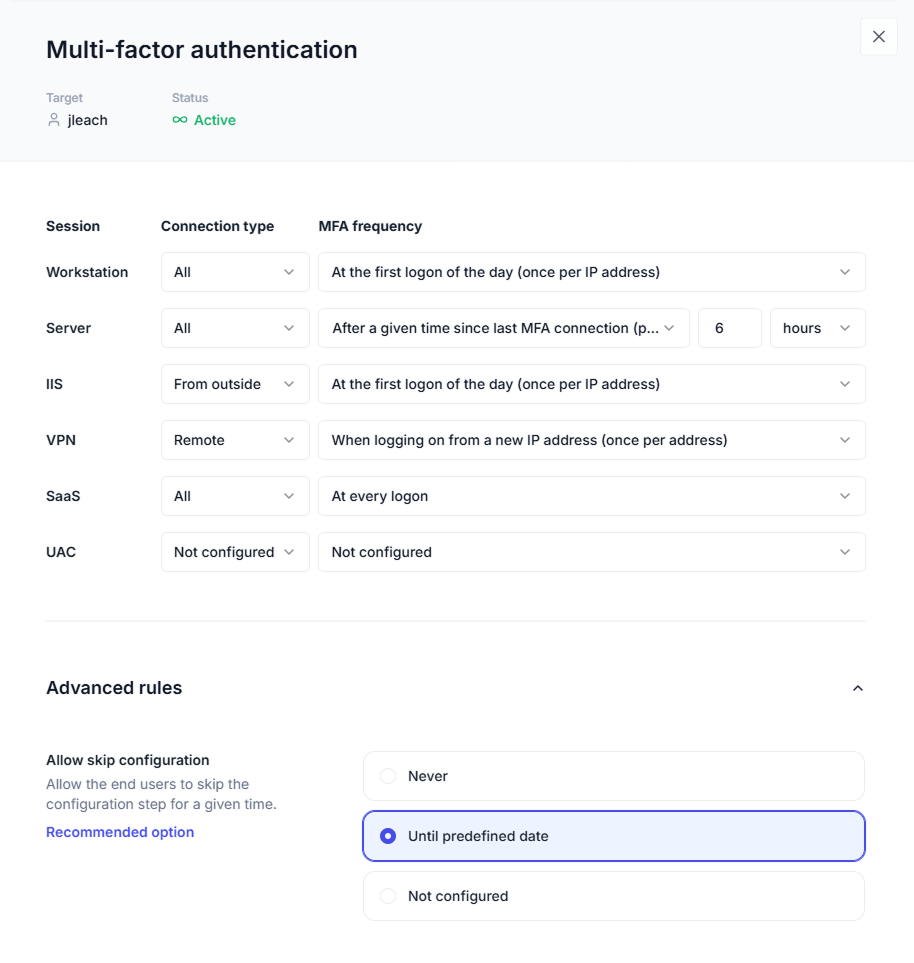
Keep MFA lightweight with custom MFA policies
Give IT full control over when and how to require MFA.
This flexible approach safeguards resources, supports compliance, and keeps business moving forward.
Configure MFA policies based on:
User role: Enable MFA according to AD user, group, or organizational unit (OU).
Session type: Adjust MFA policy according to session type, including privilege elevation requests on UAC (user account control) prompts on administrative tasks and run as administrator requests.
Connection type: Set different MFA policies for local sessions and sessions connecting from outside the network.
Fine-tune MFA application according to:
Frequency: Choose when to prompt for MFA for each session and connection type, with the ability to specify every n minutes/hours/days.
Circumstances: Set custom rules for when to prompt MFA, including on the RDP or RD Web connection, or on logins on devices that aren’t connected to the LAN.
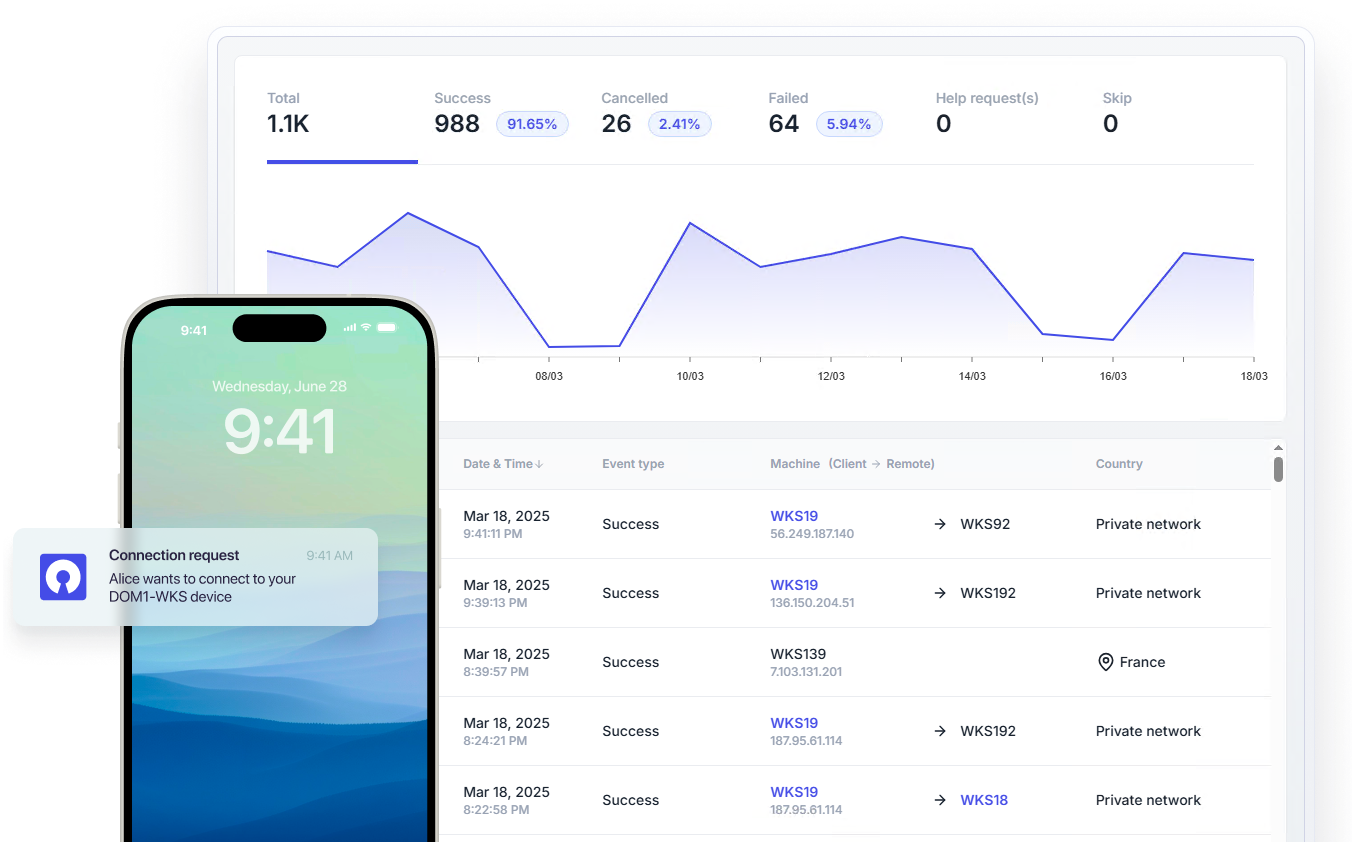
Detect threats and get compliant with MFA event tracking
Easily monitor and manage Active Directory MFA that scales seamlessly across all users.
Complete visibility
See all MFA events, successful and unsuccessful, per user, and generate MFA reports to support cyber insurance and compliance requirements.
Real-time alerts
Get instant notifications for end user MFA help requests.
One-click actions
Reset MFA keys or temporarily disable MFA for a user when needed.
Reduce the risk of MFA fatigue with contextual access controls
UserLock’s contextual restrictions provide an extra layer of security by verifying each access attempt against set policies.
Control access by machine, device, location, time, session type, initial access point, and the number of active sessions.
Example use case
Enforce the use of corporate machines for remote working.
Read the case studyAffordable, easy to use with Active Directory
UserLock allows us to have a single 2FA solution for all of our users. It integrates easily with Active Directory and is simple to install and maintain. It's an IT manager's dream. ”
Bill Hopkins
IT Director | City of Keizer, Oregon
Reviewed on


Stolen user credentials were at the root of some of the biggest hacks in the last few years.
UserLock is a powerful product that focuses on preventing the internal and external threats related to compromised credentials, by providing the administrators with detailed options for restricting and monitoring access to their Windows-based networks. ”
HelpNet Security

UserLock MFA for RDP significantly enhances security, especially today with a boom in remote working.
IT connect

UserLock makes implementing multi-factor authentication (MFA) extremely easy.
4 sysops