How to improve Windows file share auditing
Windows file share auditing helps organizations secure their sensitive files and folders. Here's how to get started with file share auditing and best practices to follow.
Updated December 31, 2024)
Windows file share auditing helps organizations secure their most sensitive files, folders, and file shares and prove compliance. Having file auditing is in place can help IT security teams to quickly identify a data breach and respond in time to stop the breach. Here's how to ensure your file share auditing is set up for maximum security.
Across almost all industries, file servers remain the primary asset of choice for attacks. On Windows-based networks, protected data is most likely hosted on server-based file systems, making these servers an attractive target for attackers.
IT security teams want to keep these files secure, only allowing access to those who need it. To both put this in place for security and prove you're doing it for compliance, IT needs visibility into who has access, who is using access, and what users with access are doing with the files.
These 10 best practices for Windows file share auditing highlight how Windows system administrators can do this best with FileAudit.
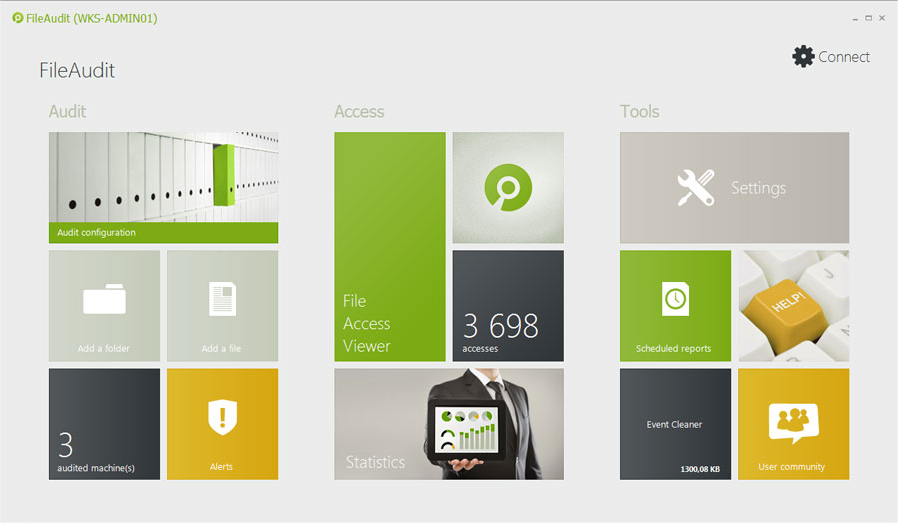
Native Windows tools have gaps in functionality, performance, and detail. They contain mountains of data, which is great in theory but makes file auditing a headache. Plus, it takes time to dig into the data and connect the dots to pull together actionable intelligence.
Remember, Microsoft didn’t design Event Viewer to be an auditing solution. Actually, Microsoft designed it to provide IT teams with a centralized application in which to view event data. So, in a scenario where IT needs to audit any given file server, there are a few shortcomings.
For one, it's complicated to figure out something as simple as “Who accessed your protected files today and what did they do?”
Answering that question takes more work than just skimming through the event log data. IT has to do meticulous research into specific field values within multiple log entries, all to “puzzle piece” their way to a potential answer. It’s time-consuming and overwhelming.
File auditing should be more than just about information gathering. Look for tools that pull together data in a way that gives you actionable insights.
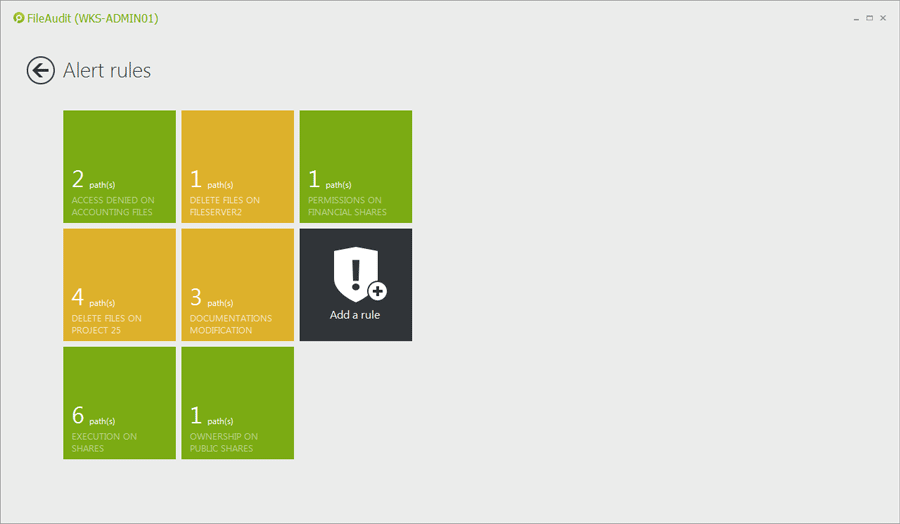
When protected data resides on a file server, there will be obvious leading indicators of a breach. By tracking file access and usage of protected data on file servers, it’s possible to detect a data breach based on unusual activity. Here are a few of the most common indicators of a breach that IT will want to monitor regularly:
Frequency: Normal user access can likely revolve around an average daily use. The presence of a mass copying or bulk deletion or movement of data is worth looking into.
Amount: Are files being accessed multiple times more than is normal? An unsure insider having second thoughts about stealing data may make several access attempts before finally taking data.
Day/Time: A user accessing data at 10 p.m. on Friday night who normally only accesses files Monday – Friday during business hours seems suspect.
Endpoint/IP Address: Access from a machine outside the company network, or one that doesn’t normally access a given set of files can be a clear sign of improper use.
Processes: Attackers may use their own tools to exfiltrate data, so seeing processes other than Explorer, Word, etc. accessing files can indicate a problem.
A third-party file auditing solution such as FileAudit allows you to easily track potential data breach indicators and allows you to take action immediately to stop threats.
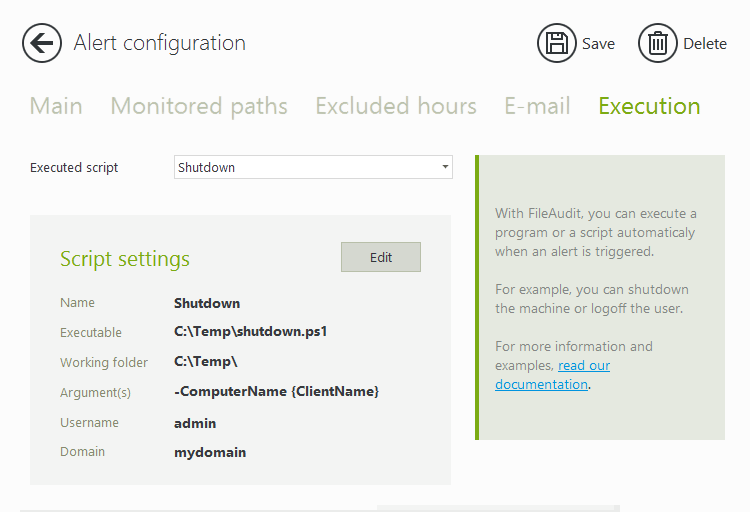
With FileAudit, you can set up alerts for unusual activity. Then, you can create and run a script (for example to shut down a machine or logoff a user), whenever a specific alert is triggered.
For more about identifying unusual file activity and stopping data breaches read how file auditing helps spot and stop a data breach.
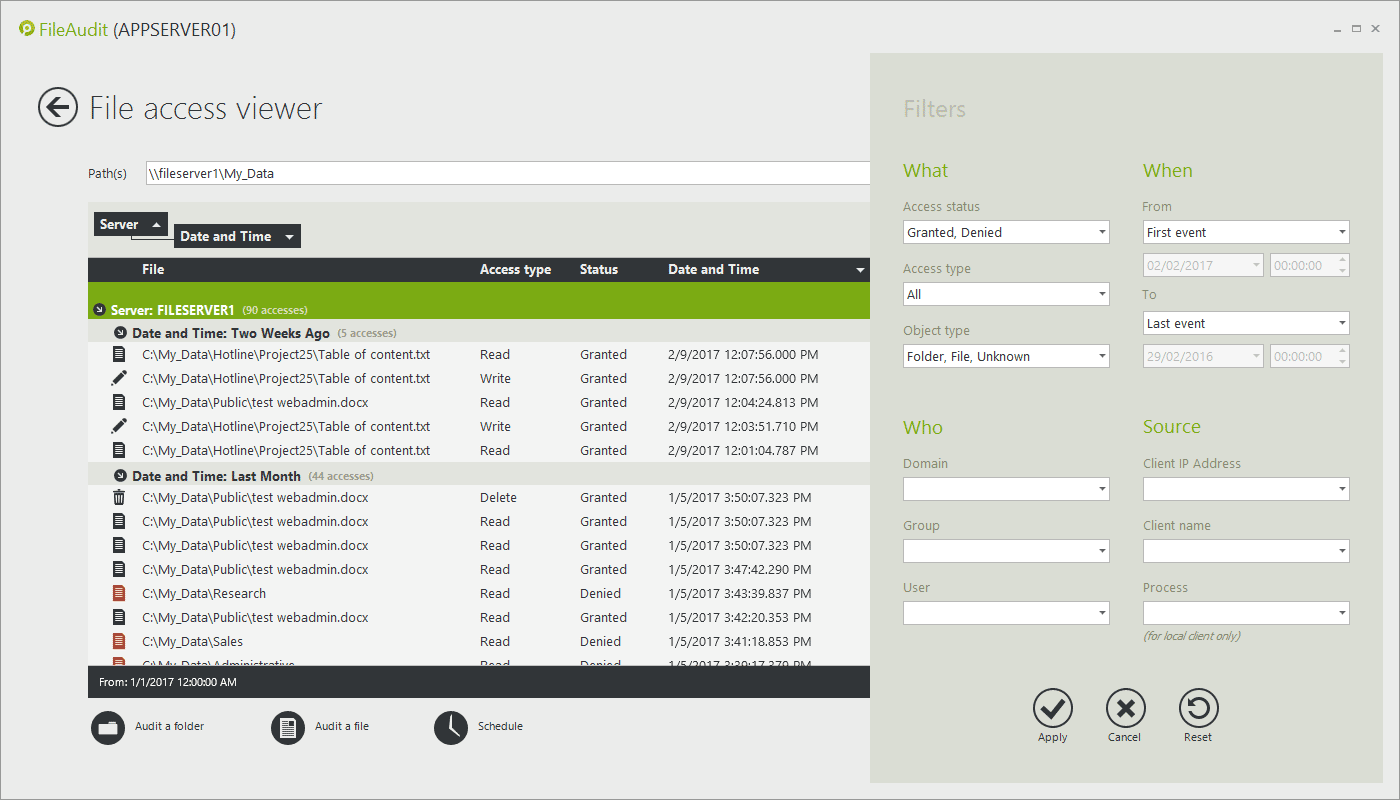
Finding answers about file access activity can be time consuming and challenging. Exclude irrelevant data and focus only on insightful and actionable information.
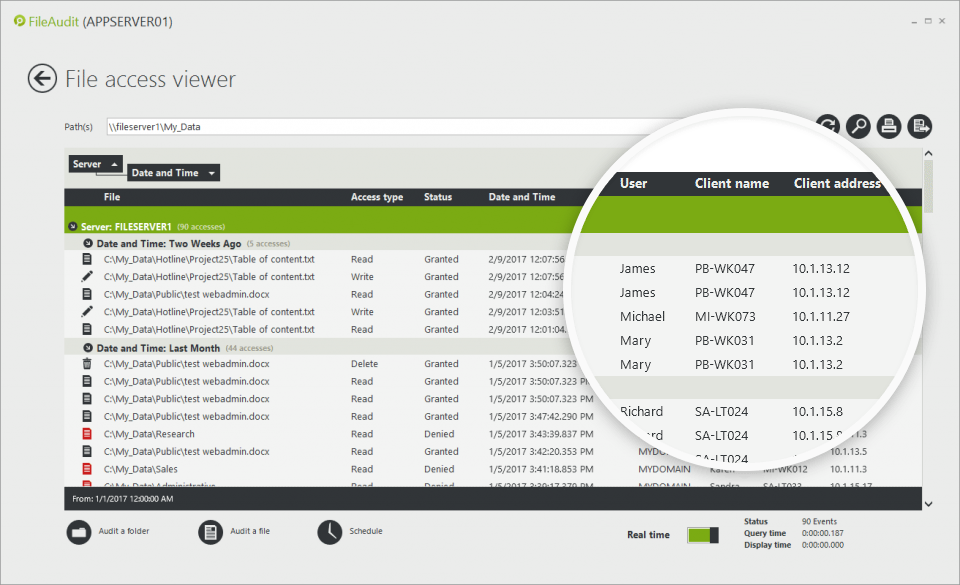
Only by identifying the name and IP address of the machine from which the file/folder access has been performed can you indicate exactly where the user has accessed the file from. This puts a spotlight on potentially suspicious access, such as a user accessing a sensitive file from a different workstation than normal.
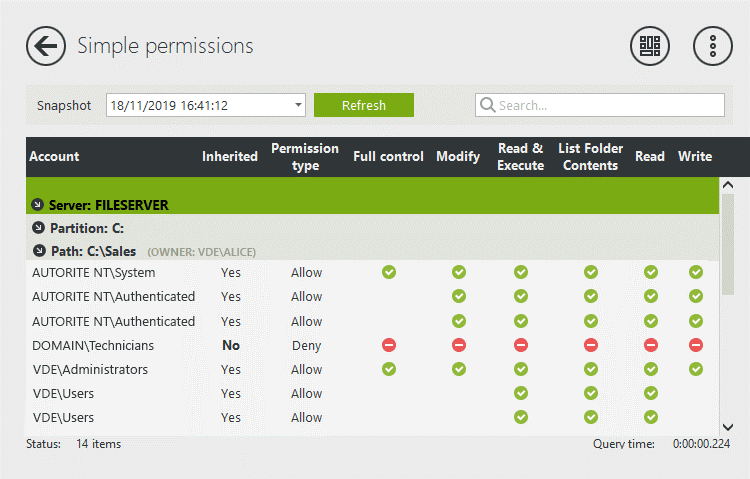
FileAudit allows you to have a centralized view of the NTFS permissions (simple and advanced) of your files and folders. To do so, it scans all the audited paths you have defined and saves the information in a snapshot.
You can set up alerts on permission changes. The alert gives you the name of the user and the name of the file/folder affected by the change. By scheduling regular snapshots, you can then compare two snapshots (one before the alert and one after) to see what changes have been made.
)
)
)
)
)
)
)
FileAudit provides the centralized monitoring and analysis of file activity data necessary to quickly and intelligently identify and report on potential breach activity. The ability to monitor activity across the whole organization (not just a single server) means quick and accurate answers can be given to who did what, when and from where.
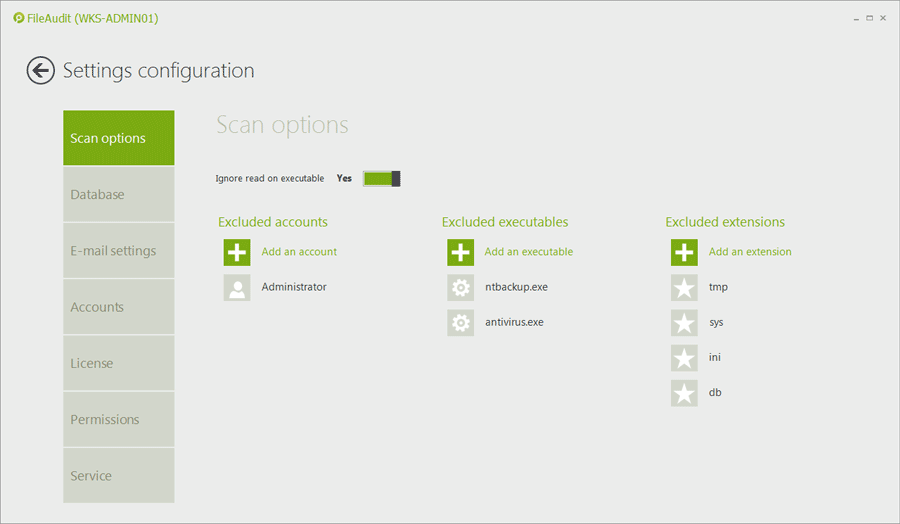
Filter out program access events (such as backup tool, anti-virus or search engine) or files with specific extensions (e.g. temporary files with .tmp extension). This keeps your data from becoming polluted.
An audit tool that discards meaningless events and keeps only the relevant access events for monitoring will improve your Windows file share auditing performance and scalability.
Unlike native Windows tools, which simply consolidate and present event data, FileAudit is purpose-built to improve the audit experience. With FileAudit, you can focus on the specific needs of compliance audits and get the details you need to prove your organization is compliant.
Make file auditing faster, smarter and more efficient.
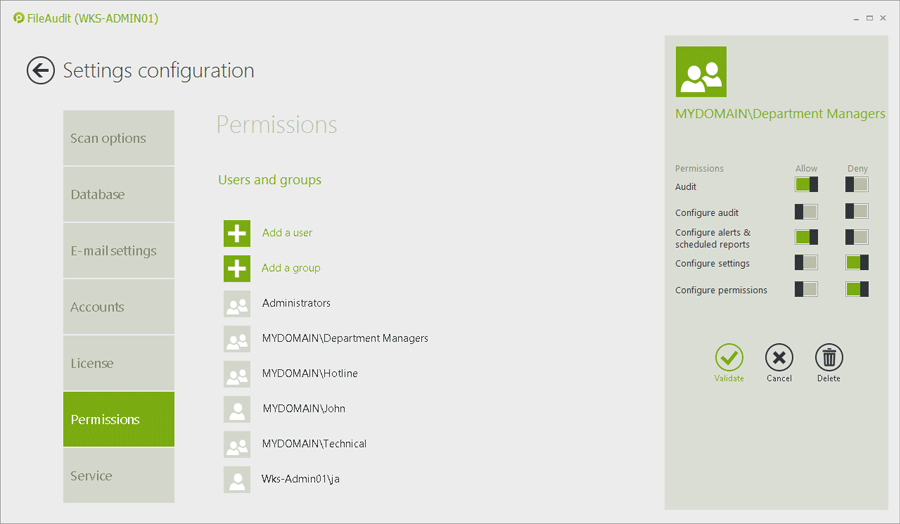
The reality is, those closest to the files have a much better sense of whether someone’s access — or use of permissions — is proper. The IT team will inevitably be somewhat out of touch with which users need what access, whether use of files is appropriate — and how all that changes over time.
For a Windows System domain, executives outside of IT or external auditors can take advantage of FileAudit features and ease-of-use to perform audits and controls autonomously without breaching security protocols.
Read more about security through user delegation with FileAudit.
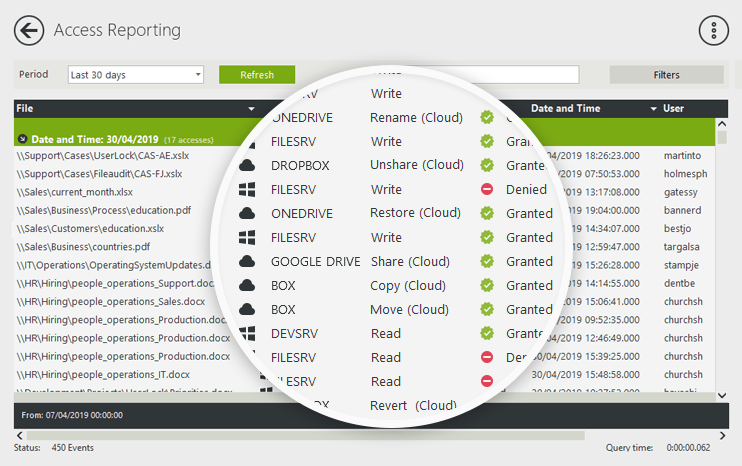
If your files aren’t already in the cloud, they will be soon. Of course, IT needs the same levels of visibility and control over access to and usage of file data in the cloud.
FileAudit gives you a single consolidated view of all file activity — both in the cloud and on-premise. This reduces the risks associated with allowing users anytime, anywhere, any device access to cloud-based file data.
More on how FileAudit can extend file auditing with cloud-based services.
File auditing doesn't need to be as time-consuming or overwhelming as it often is when you're using Windows Event Viewer.
A third-party tool designed for Windows file share auditing can do the heavy lifting for you, helping your team turn what's usually a headache into a boost for security and easy win for compliance.
)
)
)