Meet Essential Eight compliance
UserLock and FileAudit support key Essential Eight controls across all maturity levels.
Australia's Essential Eight Maturity Model (E8MM) establishes a baseline of mitigation strategies to help organizations protect themselves from common cyber threats. The Australian Signals Directorate (ASD) distilled the eight essential mitigation strategies from the Strategies to Mitigate Cyber Security Incidents published by the Australian Cyber Security Centre (ACSC).
First published in June 2017, the Essential Eight defines four maturity levels (0-3) to protect organizations’ internet-connected information technology networks. All Australian government agencies and departments subject to the PGPA Act must comply with Essential Eight maturity level 2. While non-governmental organizations aren’t required to prove compliance, the ACSC recommends all Australian organizations implement the Essential Eight mitigation strategies.
IS Decisions’ solutions, UserLock and FileAudit help organizations implement key controls required for the following Essential Eight pillars across all four maturity levels:
Multi-factor authentication (MFA)
Restrict administrative privileges
MFA implementation is a key component of the Essential Eight baseline security controls. UserLock MFA helps you meet major Essential Eight MFA requirements across all maturity levels.
Here, we've outlined the Essential Eight MFA requirements that UserLock can help with. Essentially, the only MFA controls UserLock does not support are those that concern customer authentication.
Maturity Level One | Maturity Level Two | Maturity Level Three |
|---|---|---|
Multi-factor authentication is used to authenticate users to their organisation’s online services that process, store or communicate their organisation’s sensitive data. | ||
Multi-factor authentication is used to authenticate users to third-party online services that process, store or communicate their organisation’s sensitive data. | ||
Multi-factor authentication (where available) is used to authenticate users to third-party online services that process, store or communicate their organisation’s non-sensitive data. | ||
– | Multi-factor authentication is used to authenticate privileged users of systems. | |
– | Multi-factor authentication is used to authenticate unprivileged users of systems. | |
– | – | Multi-factor authentication is used to authenticate users of data repositories. |
Multi-factor authentication uses either: something users have and something users know, or something users have that is unlocked by something users know or are. | ||
– | Multi-factor authentication used for authenticating users of online services is phishing-resistant. | |
– | Multi-factor authentication used for authenticating users of systems is phishing-resistant. | |
– | – | Multi-factor authentication used for authenticating users of data repositories is phishing-resistant. |
– | Successful and unsuccessful multi-factor authentication events are centrally logged. | |
– | Event logs are protected from unauthorised modification and deletion. | |
– | Event logs from internet-facing servers are analysed in a timely manner to detect cyber security events. | |
– | – | Event logs from non-internet-facing servers are analysed in a timely manner to detect cyber security events. |
– | – | Event logs from workstations are analysed in a timely manner to detect cyber security events. |
– | Cyber security events are analysed in a timely manner to identify cyber security incidents. | |
– | Cyber security incidents are reported to the Chief Information Security Officer, or one of their delegates, as soon as possible after they occur or are discovered. | |
– | Cyber security incidents are reported to ASD as soon as possible after they occur or are discovered. | |
With UserLock, you can add strong authentication and access controls to Active Directory user account access to network and SaaS resources.
Since you can combine UserLock MFA with single sign-on (SSO)., you can securely implement SSO with on-prem authentication for Active Directory identity access to web services and applications such as Microsoft 365, Google Workspace, Salesforce, Dropbox, and other SAML-based SaaS resouces.
What sets UserLock apart is the ability to apply MFA granularly. This way, IT stays in control of how much security is enough for your team.
With UserLock, you can set different MFA policies on existing AD users, groups, and organizational units (OUs).
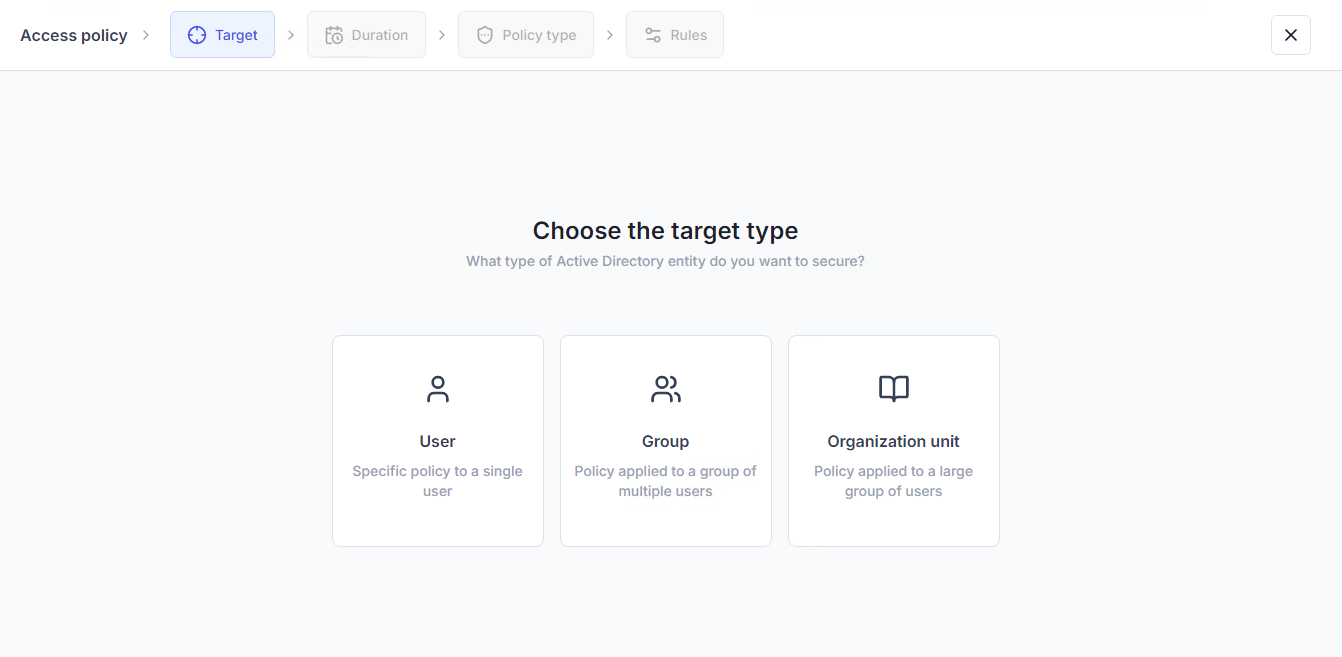
Then, you can choose whether to apply the same MFA setting across all session types, or to apply different settings depending on the type of session. For more info, read the documentation for implementing MFA.
)
)
)
)
)
)
)
For each session type, you can choose how often to prompt your users with MFA.
)
)
)
)
)
)
)
Maturity levels two and three require MFA across both unprivileged and privileged users of systems, such as your Active Directory.
UserLock provides straightforward, effective MFA to verify identity across all Active Directory accounts, whether privileged or non-privileged. This allows your organization to properly apply the principle of least privilege, which is key to lowering security risk as well as a cornerstone of zero trust architecture.
At Essential Eight maturity level two, MFA must be enforced on user access to data repositories.
UserLock makes it possible to implement MFA on AD user access to data repositories. UserLock is compatible with data repositories that integrate with Microsoft Entra, as well as data repositories on SAML-based apps such as AWS thanks to UserLock's single sign-on (SSO).
At Essential Eight maturity level three, authentication to data repositories must be phishing-resistant.
To ensure that MFA is resistant to phishing, UserLock supports MFA using hardware tokens or keys such as YubiKey and Token2.
UserLock satisfies this requirement with secure MFA methods, and offers the flexibility to choose between two of the following MFA methods:
Push notifications with the UserLock Push app
Authenticator applications such as Microsoft Authenticator or Google Authenticator
From Essential Eight’s maturity level two, the scheme requires MFA on access to systems such as AD and online services to be phishing resistant. As mentioned above, UserLock allows phishing-resistant MFA via secure keys and tokens from YubiKey and Token2. UserLock’s Push app also uses secure push notifications designed to minimize the risk of accidental approval.
To meet level two requirements, Essential Eight requires organizations to prove they log MFA events.
UserLock’s MFA event reports provide a complete log of all events related to which users are prompted for MFA upon logon, including details on whether or not MFA was completed successfully or not.
)
)
)
)
)
)
)
UserLock’s event logs cannot be modified or deleted.
With UserLock, administrators get easy visibility on all multi-factor events. You can define if and when to receive alerts for certain event types, such as MFA denials or logons outside of working hours, making it easier to quickly spot potential threats.
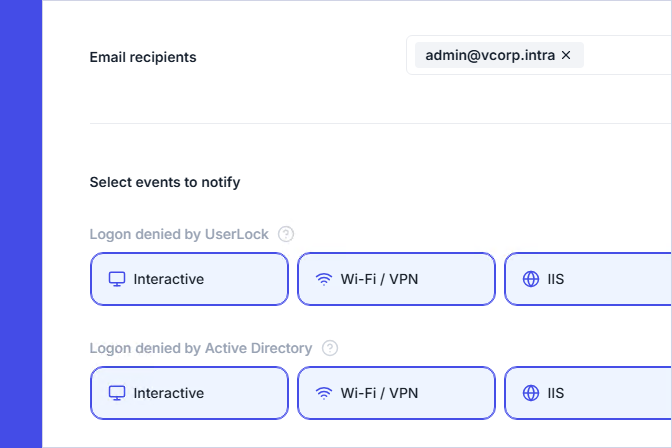
You can also define what types of activity to flag as "at risk." This helps you get an immediate alert on risky behavior and respond, without drowning in noise.
)
)
)
)
)
)
)
You can also schedule any UserLock report (custom or pre-programmed) to send automatically from the UserLock dashboard to specified recipients.
)
)
)
)
)
)
)
UserLock also helps you put in place the necessary controls to support Essential Eight requirements on restricting administrative privileges, from levels one to three.
Maturity Level One | Maturity Level Two | Maturity Level Three |
|---|---|---|
– | Privileged access to systems, applications and data repositories is disabled after 12 months unless revalidated. | |
– | Privileged access to systems and applications is disabled after 45 days of inactivity. | |
– | – | Privileged access to systems, applications and data repositories is limited to only what is required for users and services to undertake their duties. |
– | – | Secure Admin Workstations are used in the performance of administrative activities. |
Unprivileged accounts cannot logon to privileged operating environments. | ||
Privileged accounts (excluding local administrator accounts) cannot logon to unprivileged operating environments. | ||
– | – | Just-in-time administration is used for administering systems and applications. |
– | Administrative activities are conducted through jump servers. | |
– | Privileged access events are centrally logged. | |
– | Privileged account and group management events are centrally logged. | |
– | Event logs are protected from unauthorised modification and deletion. | |
– | Event logs from internet-facing servers are analysed in a timely manner to detect cyber security events. | |
– | – | Event logs from non-internet-facing servers are analysed in a timely manner to detect cyber security events. |
– | – | Event logs from workstations are analysed in a timely manner to detect cyber security events. |
– | Cyber security events are analysed in a timely manner to identify cyber security incidents. | |
– | Cyber security incidents are reported to the Chief Information Security Officer, or one of their delegates, as soon as possible after they occur or are discovered. | |
– | Cyber security incidents are reported to ASD as soon as possible after they occur or are discovered. | |
With UserLock, you can set a time quota or define access only within certain times (for example, working hours) to control access to your Active Directory and SaaS resources.
With FileAudit, you can track access by AD user, group, or organizational group (OU) across Windows files, file servers, and cloud storage. These logs provide proof of which users are or are not able to access your data.
UserLock allows you to set access policies for different types of employees according to AD user, group or OU, in line with least privilege principles.
In other words, you can prove your users only have access to the information they need to do their job.
To go one step further, UserLock also allows IT administrators to set granular, contextual access restrictions based on factors like IP address, time, machine, session type, or geolocation.
)
)
)
)
)
)
)
With UserLock, these access controls also allow you to limit the number of concurrent sessions.
)
)
)
)
)
)
)
You can also limit concurrent logons by controlling the number of initial access points allowed.
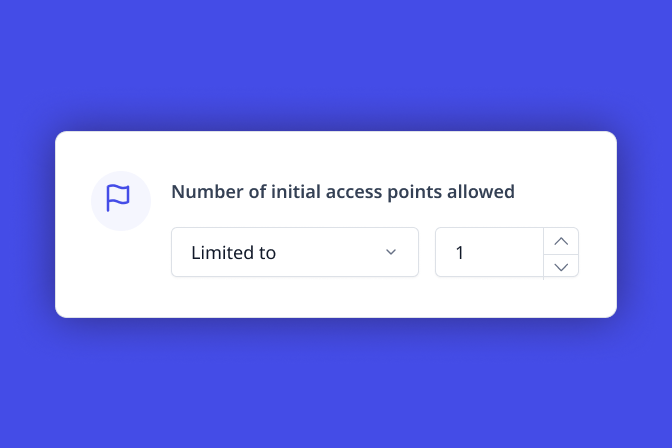
UserLock's multi-layered access security also helps secure admin workstation access. For example, with UserLock’s session-based access restrictions, you can control when and how they logon, and on what machine. With UserLock MFA, you get strong authentication on admin logons, and can track all admin access events.
UserLock allows administrators to set access policies for different types of employees, by user, group or organizational group (OU) in line with least privilege principles.
You can enable UserLock MFA for jump server connections, ensuring strong authentication for access to your administrator accounts.
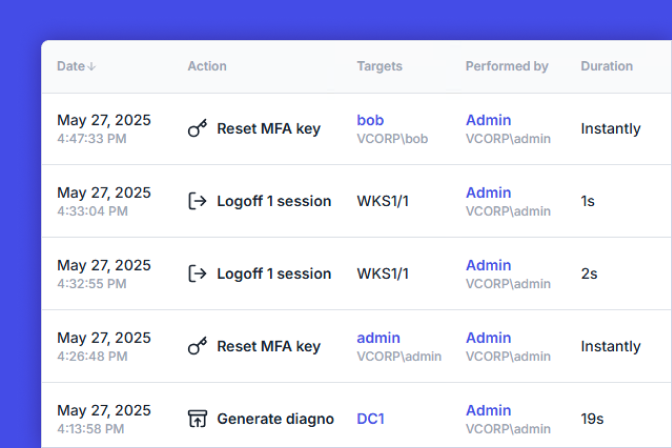
With UserLock, administrators can also record and report on all privileged access, at the user, group, or OU level, thanks to a central audit across the whole network. The administrator actions report also allows organizations to quickly see and report on all administrator account actions.
UserLock’s event logs cannot be modified or deleted.
With UserLock, administrators get easy visibility on all multi-factor events from internet or non-internet-facing servers and workstations.
Administrators can set up alerts for certain event types, such as privileged account access denials, or privileged account logon attempts outside of working hours or from an unusual location, so they can quickly detect potential threats. UserLock also allows admins to block user sessions with one click.
)
)
)
)
)
)
)
With UserLock, admins can also set up and run scripts to respond automatically to certain events, ensuring their ability to threats before any damage is done.
As mentioned above, UserLock allows you to can set up alerts on certain access event types so that you can quickly detect and respond.
Powerful filters also help you see only the information you need, speeding up IT forensics.
All UserLock reports can be pre-programmed to send automatically from the UserLock dashboard to specified recipients.