Remote work security for VPN and RDP sessions
Remote work creates big cybersecurity problems that put sensitive corporate data at risk. Learn how to secure two of the most vulnerable issues: user access via VPN and RDP sessions.
Updated June 13, 2024)
With COVID-19 (coronavirus) cases increasing by the day, organizations in affected countries around the world are asking employees to work remotely. However, offering this option without proper supervision and preparation raises security concerns. VPN and RDP are two of the most common ways remote workers connect to your sensitive Active Directory resources. Here's how to secure those connections.
First, the obvious. IT professionals understand that remote working is extremely beneficial, but they also know that remote employees create risks.
Research shows that 92% of IT professionals believe the benefits of remote work outweigh the risks.
But their approval of remote work as a whole comes with some concerns. 90% of respondents think that remote workers pose a general security risk, and 54% think they pose a higher security risk than employees on site.
Whether we’re talking about insecure networks, the risk of spying or hacking, or even exploited employees, the risks of remote working ultimately concerns how IT can securely extend access to the corporate network — and the sensitive data inside your Active Directory.
When it comes to how to secure remote access to Active Directory, VPN and RDP are common options.
A virtual private network (VPN) is like a safety net for your internet connection. It tracks everywhere you go online, and is commonly used to secure access to remote desktops.
The Microsoft Remote Desktop Protocol (also known as RDP) is used to allow remote desktop to a computer. Very easy to use and widely implemented, Remote Desktop even comes built-in to most versions of Microsoft Windows.
While RDP is a powerful and convenient business tool to facilitate remote working, it does need further securing.
One way to restrict RDP access is to ensure the Remote Desktop is used behind a secure VPN. Then, it's important to implement two-factor authentication (2FA) that is compatible with RDP and VPN to add an extra layer of security to traditional password authentication.
It's also possible to drop the VPN connection and to directly secure RDP with MFA and access controls.
There isn't a right or wrong answer here. It depends on what you're looking to do, and what your needs are. We can walk through a few scenarios to help you see when to require one of the other for your remote employees.
Non-trusted networks: If your remote employees routinely use public Wi-Fi at a cafe or at the airport, you'll want to make sure they're using a VPN with the additional security of MFA to make sure the right person is the one attempting access.
Home working: When remote employees regularly access the network from a private home network, RDP with MFA can establish a secure connection to your Active Directory resources.
Remote access to work files: If your remote employees need to access work-related documents or data within your network, you may want to ask users to connect via VPN to your corporate network, and then use RDP to access other resources within that network. Ideally, you'll want to prompt for MFA on at least one, if not both, of those two connections, depending on your security needs.
Raising employee awareness around the challenges and risks of IT security is essential. However, this is not enough. There are steps to be taken in addition to awareness.
Using a VPN opens a secure tunnel between the remote desktop and your corporate network.
For users to be able to work safely outside the office, IT administrators must be able to limit VPN access to certain authorized enterprise laptops. Any attempt to access from another machine must then be denied.
VPNs are meant to give users access to your most sensitive resources, therefore hardening them with 2FA is a crucial step toward preventing hackers from gaining access to your corporate network.
Setting up a monitoring solution for RDP connections is a great way to detect abnormal access. Real-time alerts and an automated response allow you to act before any damage is caused.
2FA helps secure user access to the Windows environment. For remote connections, the need is even more paramount. End users who connect remotely or virtually to a computer on the network should be challenged with 2FA to verify their identity.
With remote and mobile access quickly becoming the rule rather than the exception, UserLock alleviates this increased risk to enterprise security and protects against inappropriate or suspicious access.
Working alongside Active Directory, the solution helps administrators manage and secure access for all users (remote or on-premises), without disturbing employees or upsetting the IT department.
Secure VPN connections by only allowing a user access to a certain authorized device.
Monitor and react to any user session (including RDP and VPN) directly from the UserLock console.
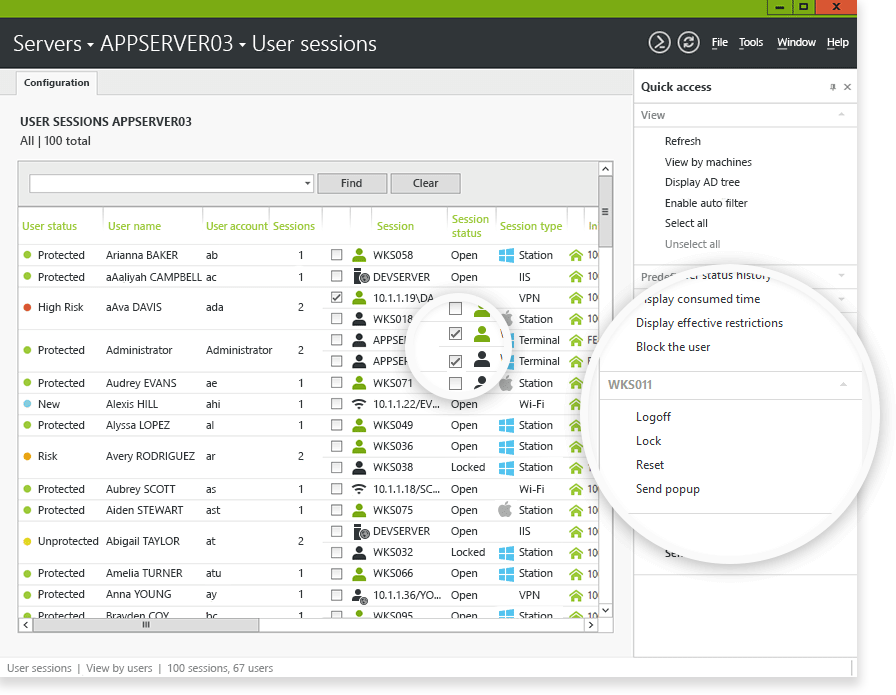
Enable two-factor authentication on all Windows logins and RDP & VPN sessions.
Choose to apply 2FA on RDP connections that originate only from outside the corporate network, or for any RDP connection inside or outside.

UserLock supports 2FA with UserLock push notifications, through authenticator applications that include Google Authenticator, Microsoft Authenticator, and LastPass Authenticator, or programmable hardware tokens and keys such as YubiKey and Token2.
)
)
)