Check users logged into Windows server, computers, and all RDP connections
With UserLock, track and control all user access to know who is logged into the Windows Server network, from which computer(s) or through an RDP, for what time, and for how long.
Published June 17, 2015)
IT Administrators often need to know who is currently logged on to any computer or connected to a server, either while at the console or through a remote desktop session.
Spend a few minutes perusing online forums and common questions include:
Who is logged into Windows Server 2012?
How can I view all active remote desktop sessions?
Which computer is a user currently logged into on my domain?
Who last logged into a specific computer?
What is the last date and time a computer logged into the domain?
Find all users logged into a remote machine.
View all users connected to a server via remote desktop (RDP)
Display all virtual desktop infrastructure (VDI) sessions
See all remote desktop connection logs
What’s more, IT administrators need to better protect all these connections. So in addition to better monitoring, an organization needs to think about how multi-factor authentication can be best deployed on all connections to prevent unauthorized access.
1. Check users logged into computers: Know who is logged on interactively at the workstation/device or is connected remotely via a remote desktop connection (RDP).
2. Check users logged into servers: Know which users are logged in locally to any server ((Windows Server 2003, 2008, 2012, 2016 etc) or are connected via RDP.
3. Check Virtual Desktop Infrastructure (VDI) sessions: VDI is a variation on the client-server computing model. It hosts a desktop operating system on a centralized server in a data center. If desktop virtualization is deployed, it’s also important to be sure to identify and monitor VDI sessions.
With UserLock, an organization can track and record all user access to know who is logged into the Windows Server network environment, from which system(s), since what time and for how long.
Here’s a quick video that will highlight how to do this:
Once UserLock is deployed, every user session on the network is monitored and audited by UserLock to provide immediate and real-time visibility on all network sessions. This includes all session types (workstation, terminal, Wi-Fi, VPN, IIS and SaaS sessions).
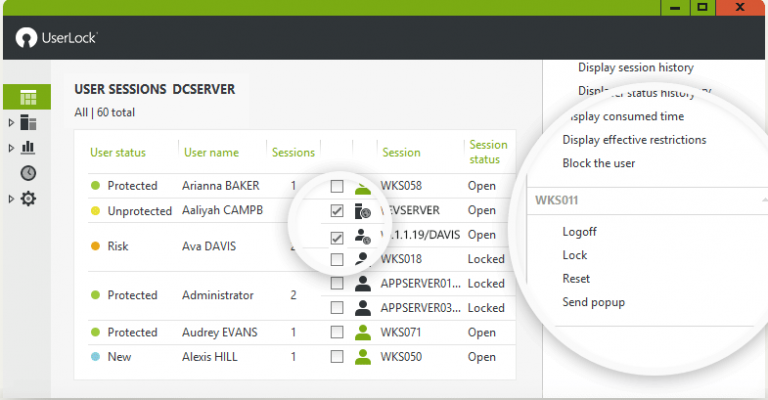
View all sessions that are active at any moment.
All session events are stored in the database for auditing and reporting.
You can view which user is connected (user name, user account, organizational unit, etc) the time and date of their logon (view all the session status opened by a user, from where he has logged on, since when, etc)
Further information about the session includes, for example, the last workstation on which the user logged off and the time of the last logoff.
You can also choose to monitor user sessions by computer. You can view all users with a session on this computer, get the computer localization (building/room of the computer etc) and view the computer name, the client IP, the organizational unit, etc.
In addition to Microsoft VDI platforms, UserLock can also be installed on other VDI platforms such as VMWare and Citrix.
Because UserLock continuously monitors all login and session events in real-time, organizations can also react to what users do through alerts. These notifications allow Active Directory administrators to instantly react and respond, directly from the UserLock console itself (E.g. remotely closing or locking user sessions or the shutdown of specific workstations).
Finally, UserLock makes it easy to also enable multi-factor authentication (MFA) on any Windows logon and RDP connection. Leveraging push notifications, authenticator applications or programmable hardware tokens to generate a time-based one-time password (TOTP), administrators can now deploy strong two-factor authentication. Multi-factor authentication is one of the most effective controls an organization can implement to prevent an unauthorized adversary from gaining access to a device or network and accessing sensitive information.
Fast to deploy, UserLock is installed in minutes on a standard Windows Server. As the video tutorial shows, a wizard walks you through the installation and takes just a few minutes. There is no requirement to use a Domain Controller Server. Any Windows Server can be the host.
See for yourself how UserLock can help your check and control all users logged into the Windows Server network.
)
)
)