How to meet HIPAA's unique user identification requirement in a Windows System
HIPAA's unique user identification requirement is a key part of the HIPAA access control requirements in the HIPAA security rule. Here's how UserLock allows you to uniquely identify users in Windows systems.
Updated May 22, 2024)
Healthcare is one of the most information-intensive industries, and patient data is sensitive by its very nature. This makes handling any sort of protected health information (PHI) and electronic protected health information (e-PHI) complex. So, to help protect this information, U.S. medical organizations must meet HIPAA compliance (Health Insurance Portability and Accountability Act), a set of regulations enforced by the Office for Civil Rights (OCR), a department of the U.S. Department of Health and Human Services (HHS). Here, we'll look more closely at HIPAA's Unique User Identification rule.
Because patient data is so sensitive, HIPAA requires regulated healthcare organizations to operate on a need-to-know basis. Meaning, everyone in an organization can access only the minimum information necessary to perform their job function.
This is one reason why unique user identification is a core HIPAA access control requirement in HIPAA Technical Safeguards. Let's break down why.
Having a unique user ID for everyone is an essential first step to ensuring role-based access rights. Making sure everyone only has the access they need to do their job. HIPAA's precise directions are to “assign a unique name and/or number for identifying and tracking user identity.”
And of course, this means no shared credentials. HIPAA strictly says no to shared credentials to assign access rights, but it's also just a general security best practice to not share Windows credentials. But to meet HIPAA requirements, you need unique identifications to prove, for example, that a specific employee took an action.
Healthcare organizations also need a unique user identification to be able to remove employee access. For example, if you terminate an employee who used a shared single login, you need that unique identifier to prove you removed their access.
For IT team, this level of monitoring is tricky to put in place with native Windows capabilities. And the consequences (HIPAA fines and penalties), are huge. Standard Windows audit logs may show which account was used, but not the actual user. This is especially true if the accounts are shared, which we still see often in Healthcare.
There's no way in native Windows to limit a given user account from only logging on to one machine at a time. Windows Active Directory provides basic user security, checking that the credentials supplied match stored user profiles before allowing access to resources.
But how do you make sure a user really is who they say they are, and achieve compliance with HIPAA Technical Safeguards?
To establish a unique user’s identity in a Windows system, organizations must turn to a third-party access security solution, such as UserLock.
Here's how UserLock helps you meet HIPAA requirements:
Prevent or limit simultaneous logons
Limit access based on contextual factors and role-based access controls (RBAC)
Deploy multi-factor authentication (MFA) for HIPAA across all users
With UserLock, you can prevent or limit simultaneous logons (using the same ID and same password) across all session types (workstations, terminal, interactive, Internet Information Services and Wi-Fi/VPN).
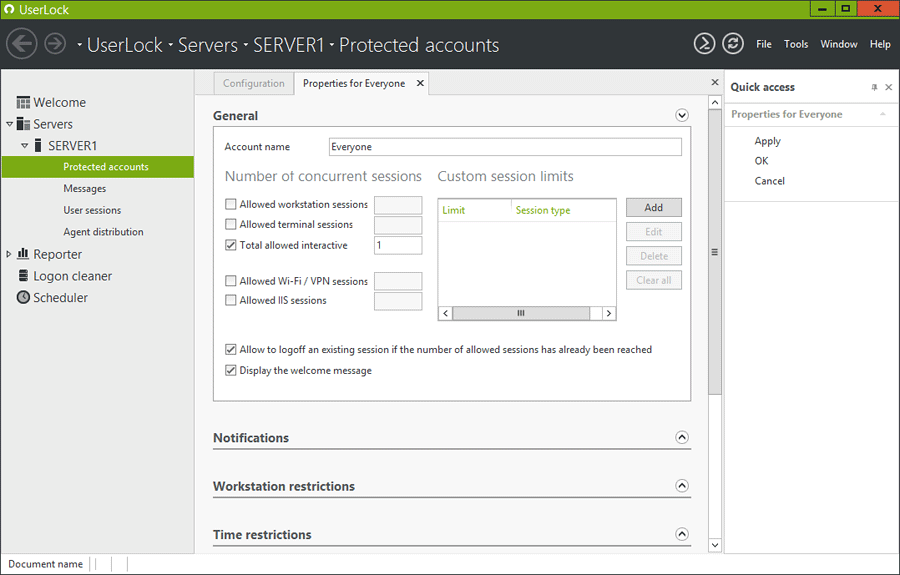
Preventing concurrent logins enforces accountability, making sure that Nurse Susan really is Nurse Susan when she goes to logon to the network. Not controlling logins creates a whole non-repudiation issue, which is why it’s vital not only for HIPAA compliance but for the security of your patient information.
HIPAA is about security — security from outsider attacks, insider mischief, and careless behavior.
As well as preventing concurrent logins via a single identity, UserLock permits, denies or limits access based on a range of contextual factors such as origin, time, and session type. For example, you can set access controls by user, group, or organizational unit (OU) to ensure role-based access control (RBAC). You can also limit access to certain workstation/locations and limit network access methods (think Wi-Fi controls).
These customized contextual access controls further help verify the identity of the user. This helps stop unauthorized access from users who have no access rights but are trying to deliberately circumvent the system to gain access.
It also ensures the right users can easily still get the necessary access to provide the best possible treatment for their patients.
While there's a separate HIPAA requirement for Person or Entity Authentication, multi-factor authentication (MFA) is an extra layer of security to prove that the person requesting access is indeed the right person.
UserLock also monitors all Active Directory sessions in real time providing a flow of information for other IT security tools and a log of access information for audit and forensics.
UserLock's wide range of access controls, session management, MFA, and reporting capabilities make it a cost-effective, straightforward solution to help meet HIPAA's unique user identification requirement, and much more.
Curious to learn more? UserLock installs in minutes on a standard Windows Server. The installation can be done on any server member of the domain. There is no requirement to use a Domain Controller server.
Once installed, UserLock must deploy a micro agent onto each workstation that are members of the selected network zone. This can be done through the UserLock console which contains an agent deployer with manual or automatic modes. UserLock reads Active Directory information but doesn’t modify anything regarding accounts nor schema.
)
)
)