File auditing for Windows file server & cloud storage
Get faster, smarter file auditing. Monitor, alert and report on file access events across Windows file servers and cloud storage
Audit file access for Windows file servers and cloud storage
Native Windows file auditing in Windows Event Viewer is a real pain. It takes way too much time to get half the information you need. There had to be a faster, less frustrating way to monitor file access events.
FileAudit changes that. It’s simple, efficient, and built for clarity.
With FileAudit, you get a clear, centralized view of all file access events across multiple Windows file servers or in cloud storage — all in one searchable dashboard.
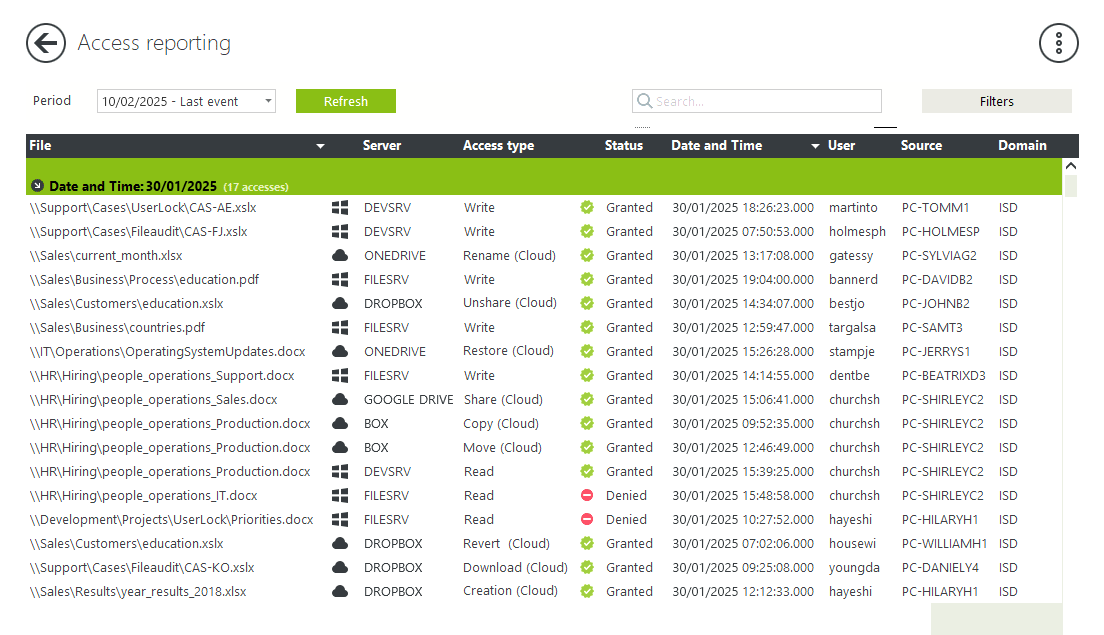
Monitor folder and file access events
Monitor file and folder access in real time across Windows file servers and in the cloud.
Find the answers you need quickly with searchable reports, and tie actions to specific users thanks to IP address tracking and machine name.

Alert and respond to file access activity
Set up file access event alerts and automated responses. Detect and respond to suspicious access events such as access denied, file deletion, and mass file access events (bulk copy, delete, or file movement).
Audit folder and file access events
Simplify folder and file access auditing with a centralized file audit trail that’s searchable, secure, and always available.
Finish IT forensics faster on file access events and file usage thanks to searchable Windows file audit logs, and identify which user did what.
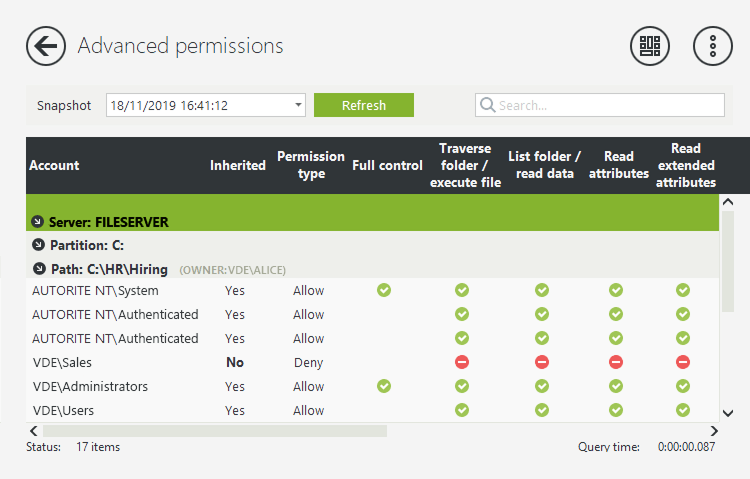
Track and report on NTFS permissions
Report on and track NTFS permissions, permission changes, and file and folder properties. See basic and advanced NTFS file and folder permissions, with properties such as size, creation date, and last modified date in one drill-down report.

Monitor cloud storage
Extend file access auditing to data stored in the cloud. FileAudit delivers cloud storage monitoring for files in OneDrive, SharePoint Online, Google Drive, Dropbox, Box, and more.
See all file and folder access events in a single dashboard, across both Windows file servers and cloud storage. With clear visibility, it's easier to quickly spot risks.
Prevent data breaches and get compliant
With FileAudit, see and react to user activity on your files and folders in real time. Clear visibility with an easy-to-use file access log helps protect data, detect ransomware threats early, and support compliance.
Protect data in Windows file servers and the cloud
Protect sensitive data from unauthorized access, theft, alteration, or deletion. FileAudit delivers real-time file monitoring, alerts, and automatic responses to suspicious file access events. Quickly identify who accessed (or attempted to access) data, changed file ownership, or modified permissions thanks to accurate IT forensics.
Prevent ransomware with real-time file access monitoring
Minimize ransomware risk by analyzing improper file access.
Get alerts on mass file encryption or ransomware-generated file extensions. Configure predefined scripts to automatically block or log off the user when an alert is triggered, stopping the attack instantly.
Get compliant with a centralized audit trail
Demonstrate data security compliance and avoid penalties. Granular file access management includes NTFS permissions tracking, real-time alerts and automated responses to suspicious access. A searchable file audit log shows who accessed what across Windows file servers and cloud-based file services.
Intuitive to use
FileAudit is simple to manage and cuts the workload of file monitoring and auditing with a searchable audit trail of cloud and Windows file server access events.
Quick set up
FileAudit installs in less than 3 minutes thanks to a remote, agentless deployment that scales easily across any number of users.
Easily adopted
FileAudit allows IT to delegate file monitoring to non-IT personnel so they can track files across their business line, without breaching security protocols.
Cost-effective
Building on your investment in Windows, FileAudit offers file access security across data in Windows file servers and cloud storage.
Join 1000+ organizations that rely on FileAudit
Whether you’re a small to medium-sized business (SMB) or a large enterprise, FileAudit is a proven solution trusted by the world’s most regulated and security-conscious organizations.
What clients say about FileAudit
One of the best, less intrusive File Audit programs. At a very reasonable cost.
Hanns S.
IT Director
Reviewed on

Like no other. Easy to understand and use.
We got FileAudit due to a breach of trust from a key employee. We didn't expect it to happen and when it did we were dumbfounded. This adds a layer of accountability to all staff members. ”
Kevin T.
Reviewed on

Great software!
It gives you a good in depth look at who and what is accessing files on your file servers. We use File Audit to monitor mass data removal from our file server and to run reports when files get accidentally moved or deleted. ”
Mantas K.
Reviewed on

Great choice for file auditing
Our company reviewed a number of different auditing packages and in the end, FileAudit stood out to be the best of breed for both functionality and price. It took literally only minutes to get setup and running. ”
Daniel Norris
Reviewed on







