Why file auditing matters for CMMC 2.0 compliance
Show you've done the work to track who has access to sensitive files and folders.
Published September 11, 2025)
One of the most striking evolutions in cybersecurity over the past two decades has been the growing global influence of frameworks, standards and certifications. This is especially true for sectors like defense, where compliance isn’t just helpful, it’s required.
The Cybersecurity Maturity Model Certification (CMMC), developed by the U.S. Department of Defense (DoD), is a clear example. If your organization is part of the defense industrial base (DIB), CMMC compliance is a must-have for doing business.
While frameworks provide best practices and standards define how to implement them, certifications like CMMC demand proof. You have to show, through a third-party assessment, that you’ve done the work to secure sensitive data and systems.
CMMC came from a simple but powerful insight: securing the networks and data at only the large defense contractors isn’t enough. The entire supply chain, including the global network of small suppliers supporting those big players, must meet the same cybersecurity expectations.
Certifications like CMMC level the playing field. Everyone knows what’s expected, and everyone must prove they’re meeting the standard.
Starting in 2025, any organization bidding for contracts through or connected to the U.S. DoD supply chain must comply with CMMC 2.0.
This updated version introduces three compliance levels, which align with NIST 800-53 and NIST-800-171:
Level 1 (Foundational): Basic cyber hygiene, verified through annual self-assessments
Level 2 (Advanced): Higher-level practices, with third-party assessments every three years
Level 3 (Expert): Intended for the most sensitive data, with government-led assessments
The relevant level for a supplier will depend on the depth and complexity of their involvement in the supply chain, with foundational being the most basic.
Regular assessments are required to maintain compliance, with annual self-assessments for the foundational level, and tri-annual third-party assessments for the advanced and expert levels.
CMMC 2.0 requires organizations to meet a wide range of cybersecurity requirements. However, fundamental across many of these is the ability to protect and track access to sensitive data.
Many provisions of CMMC 2.0 have an impact on file auditing. The most important of these can be reduced to a set of basic principles:
Monitor which users access files and what they do (e.g., reading, writing, modify, and deleting)
Alert admins to unusual access and ensure there is a way of blocking access if it breaches policy
Centralize logs, protect them from tampering, and track who accesses the logs themselves
Ensure there are no blind spots, such as data in cloud platforms
Make audit data as simple as possible for admins to review and act on
Retain file access logs for long enough to support investigations or audits
In short, no user should be able to access files without that being monitored and logged on a 24x7 basis.
Simply implementing file monitoring and logging is not enough on its own. The tools must also be practical to use on an everyday basis.
Native Windows tools like Windows Event Viewer require a lot of manual effort and don’t scale well across larger numbers of files.
While PowerShell scripts to monitor NTFS file permissions can compensate to some extent, this approach will still miss a lot of detail and lack centralized reporting, which is essential to CMMC 2.0.
FileAudit helps organizations meet CMMC 2.0 requirements by making it simple to monitor, log and audit files across both internal and cloud systems.
This comprehensive “do-it-all” approach makes it an ideal fit for CMMC 2.0 compliance, whether at foundational, advanced or expert levels.
FileAudit offers visibility and control around every aspect of file auditing, including the processes that have an indirect effect on these:
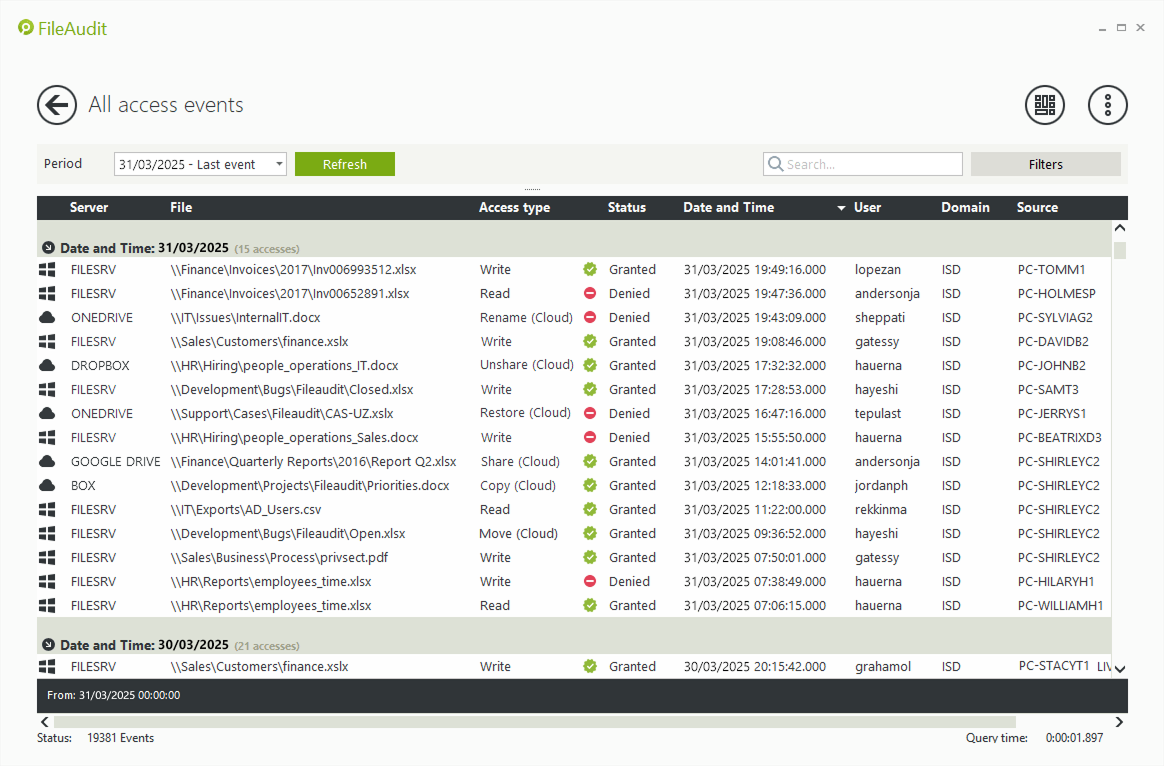
Tracks file access events like reads, writes, deletions, and copies
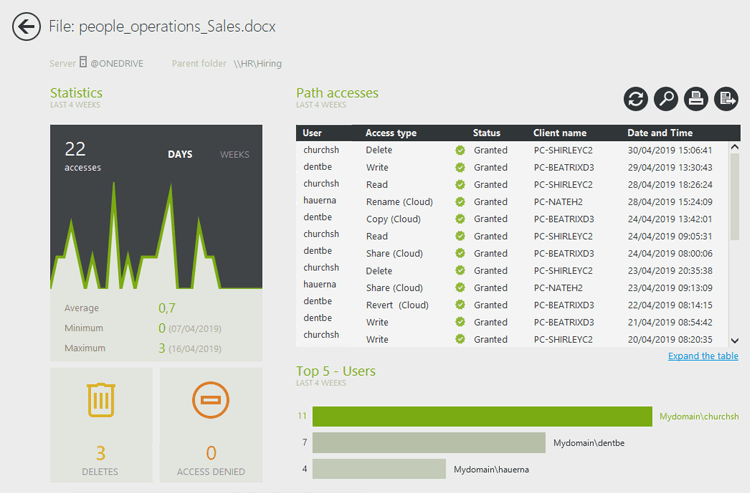
Sends instant alerts (via email or SIEM) for abnormal file access patterns, like mass deletion or off-hours activity
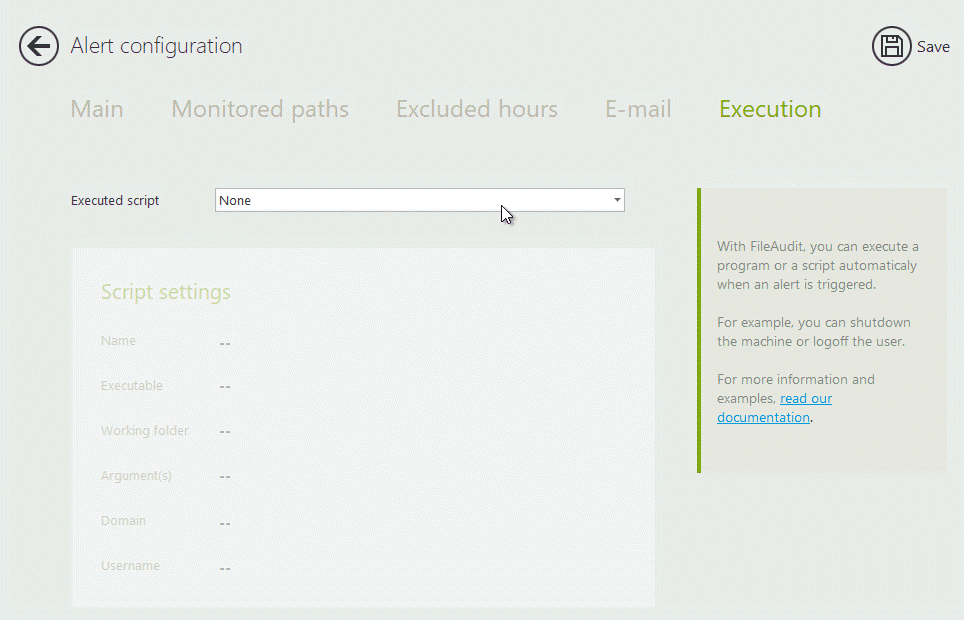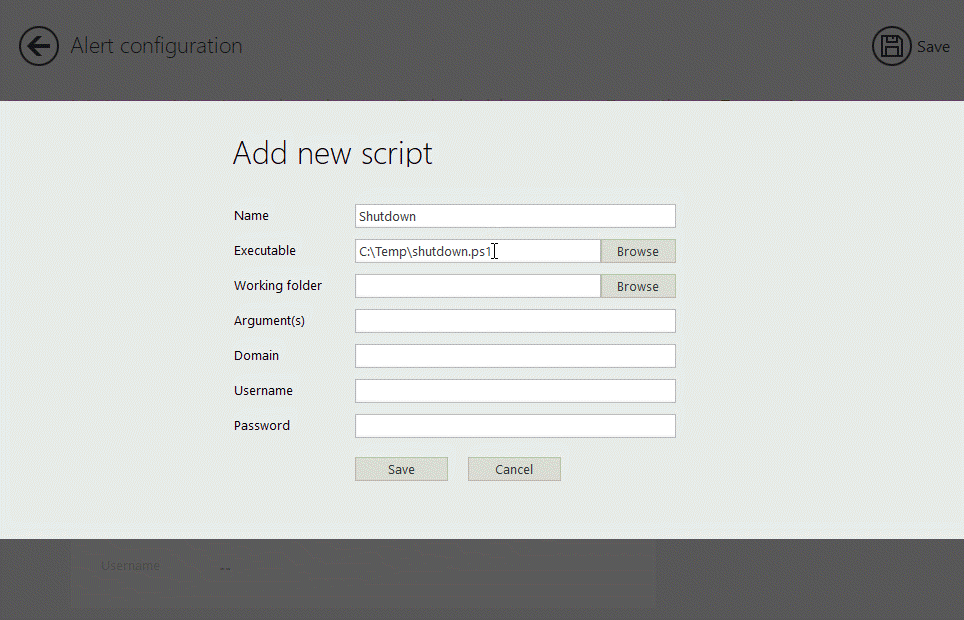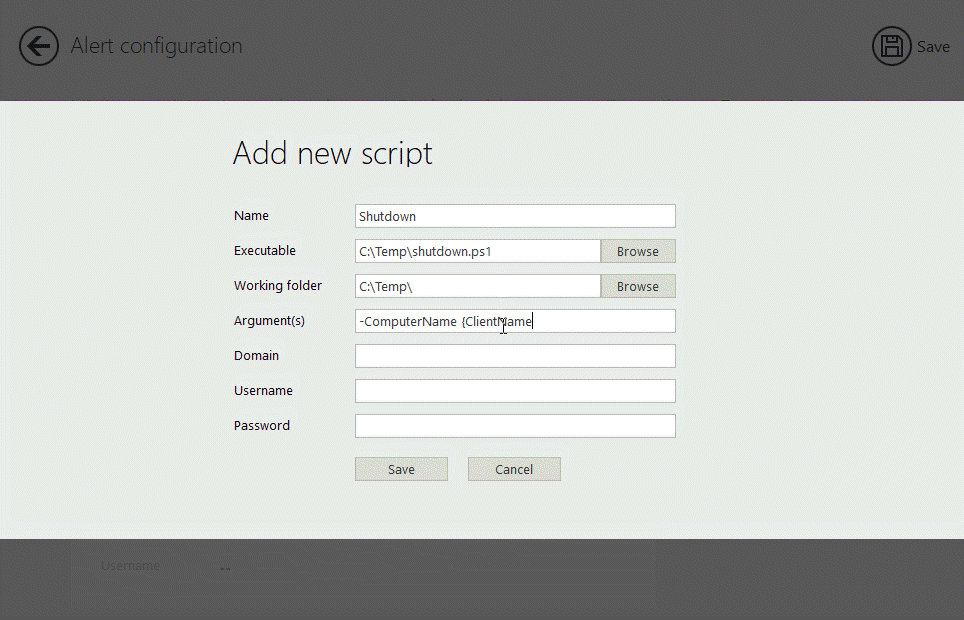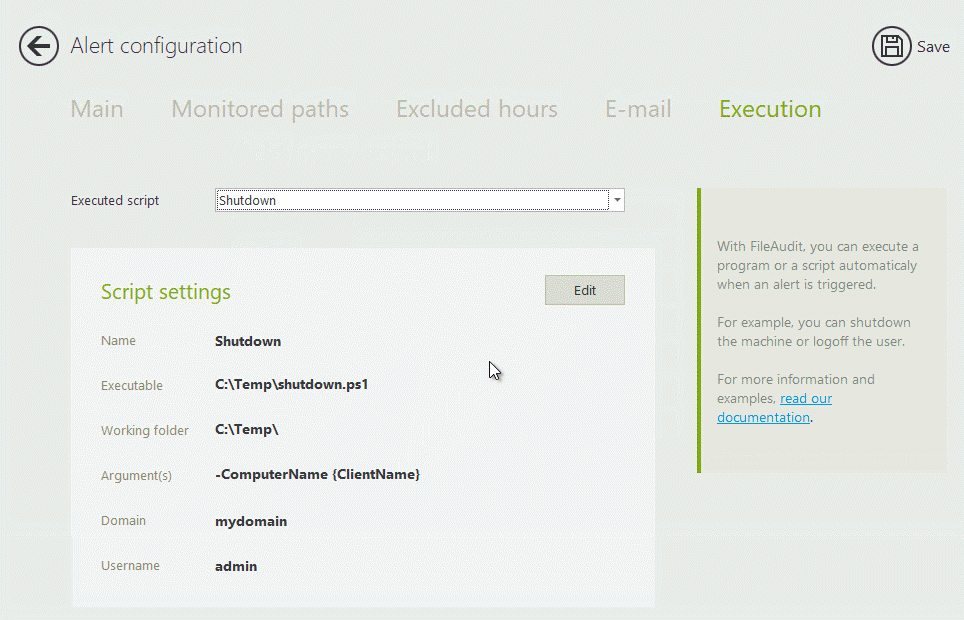
Generates audit reports that map directly to CMMC 2.0 requirements
Supports long-term log storage to comply with CMMC 2.0 data retention requirements
Audits access across platforms including OneDrive, SharePoint, Google Drive, Dropbox Business, and Box

Centralizes tamper-proof access logs, making it easy for admins study access behavior by users over time
Powerful tools are only useful if people actually use them. That’s why FileAudit’s interface is built with usability in mind, for IT admins and non-technical users alike.
FileAudit makes file the auditing and reporting functions easy to access for experts and non-IT staff alike through three simple panes:
Audit: See live and historical access to files across Windows servers/paths, cloud platforms, permissions and properties, and important access alerts.
Reports: Get insights into file/folder properties, access denied events, an overview of all access events, and a summary of current NTFS file access permissions.
Tools: Manage scheduled reports, audit databases, and system settings.
File auditing without filtering can generate a flood of data. That noise can hide real threats.
FileAudit gives administrators the precision they need to focus on what matters. You can audit:
Specific users, AD groups, IP addresses, machine name, or software executable accessing a file
Defined date/time ranges
File actions (read, write, delete, access denied)
CMMC 2.0 is a major compliance test for any organization connected to the U.S. defense supply chain. But at its core, it’s about knowing who has access to what, and proving it.
File auditing is a foundational part of that. And FileAudit makes it easier, more accurate, and far easier to scale, whether you’re just starting out with Level 1 or pursuing the more advanced tiers. Plus, you’ll gain a better understanding of how your data is being accessed over time.
With real-time monitoring, detailed reporting, and simple deployment, FileAudit helps take the complexity out of compliance.
)
)
)