How FileAudit automates response to unauthorized file access
Detecting suspicious file access is only the first step. It’s what happens next that matters.
Published September 8, 2025)
Monitoring sensitive files for unauthorized access used to be a concern limited to sectors like healthcare and financial services. That's changed with rising anxiety around ransomware and insider attacks. Today, file access event alerts and automated remediation response are a crucial early-warning system for organizations of all sizes.
However, simply detecting suspicious access in the form of alerts isn’t the same as doing something about it.
The first challenge is distinguishing genuine alerts from false positives. Because security systems, including file monitoring, can generate a lot of alert "noise," fatigue can quickly set in a way that causes security teams to miss genuine threats.
A second problem is time. Security teams must accurately respond to unauthorized file access in an era where computing power makes it possible to copy thousands of files in a few seconds. Stopping an attack means responding almost instantly, which is not always possible.
Perhaps most difficult of all, organizations must take into account the sheer number of places sensitive data can be stored, which now includes multiple cloud platforms. Monitoring this type of estate quickly becomes a major undertaking, even for well-staffed IT teams.
Automation provides one answer. Unlike humans, machines can react instantly as directed to by custom PowerShell scripts that integrate with .NET, in theory overcoming these limitations.
Unfortunately, security teams still need to work out what counts as normal and what doesn’t, at what trigger points automation should intervene, and what action should be taken. There is no single template for this; it will inevitably vary from organization to organization.
File access patterns vary. An employee might access only a few files most days, then suddenly need to access hundreds at short notice. If automation responds too aggressively, it can hurt productivity (the last thing IT wants to be responsible for).
The downside of automating file auditing response with scripts alone is that it requires skills and experience that not every admin team will have. Scripts also function like legacy code that requires regular tweaks to take account of Microsoft updates to the underlying software. In short, scripting will do the job, but it can be complex to manage in larger environments.
FileAudit removes that complexity.
It comes with built-in, predefined remediation scripts to help reduce configuration errors and speed up setup time. You can set up these custom scripts to respond to common alerts with specific actions, such as shutting down a machine or logging off a user.
For a more detailed overview, read how to set up an alert.
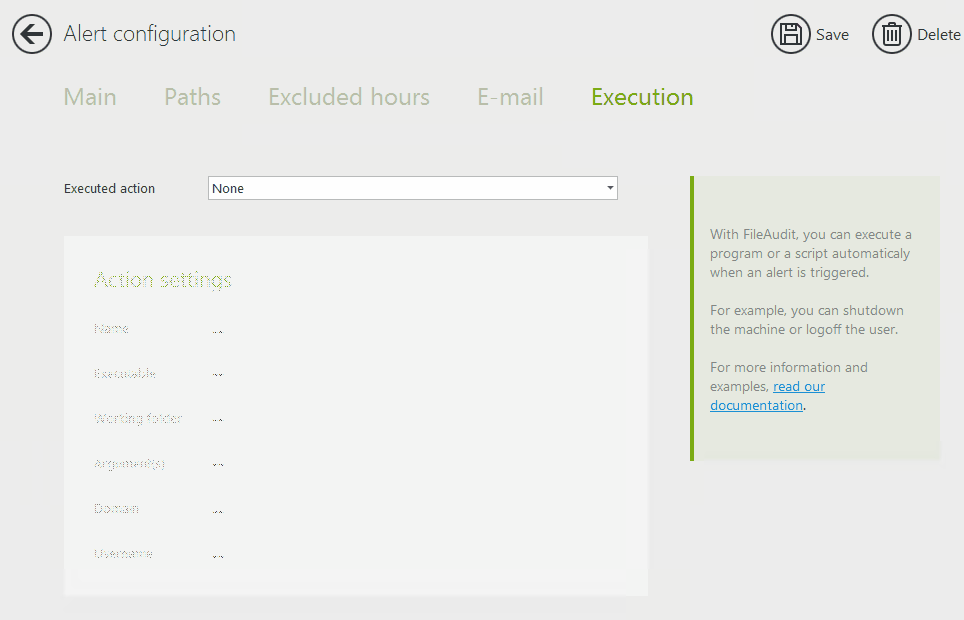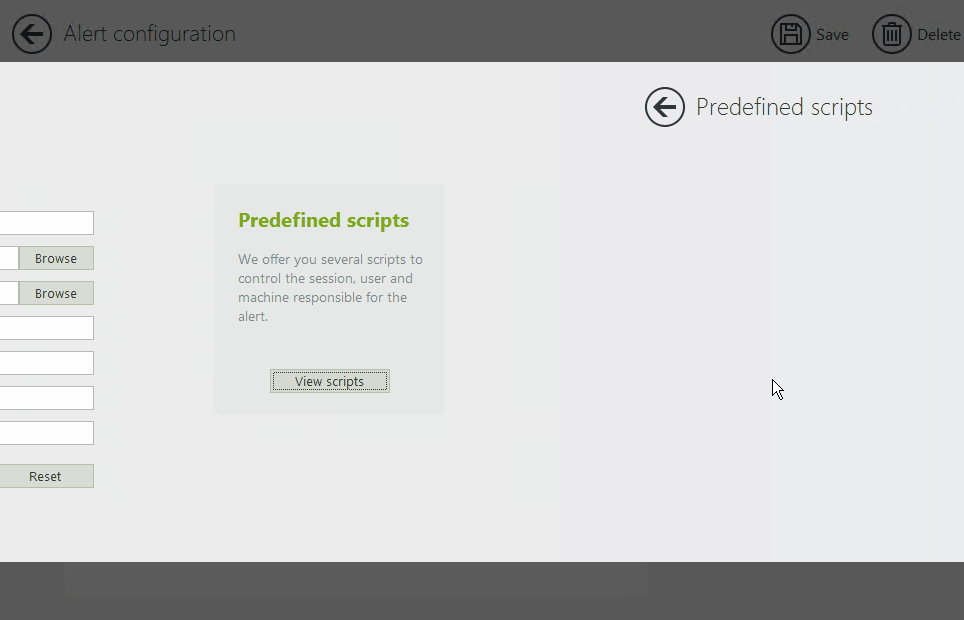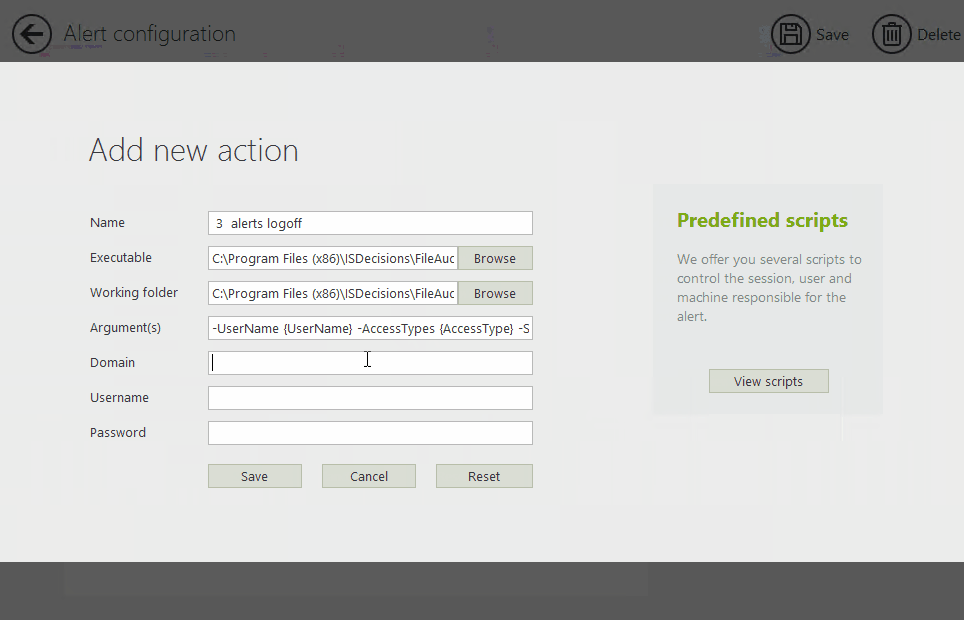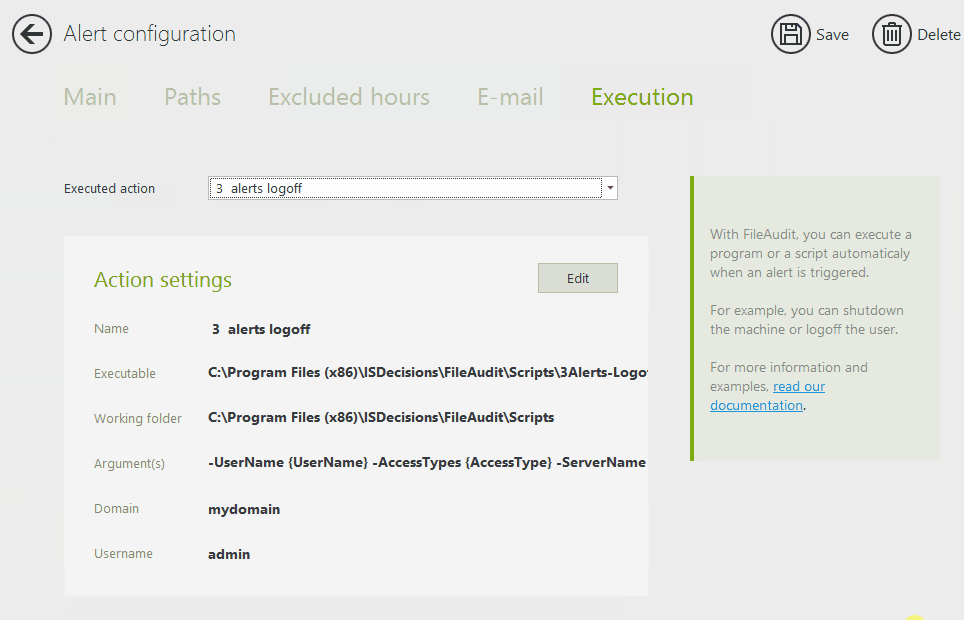
Anomalies are different in every organization. To avoid false positives, careful configuration is key.
That's why FileAudit lets you combine detailed alert criteria based on:
Single file access or mass access events
Read, write, move, and delete actions, permission changes, and more.
Access outside of specific time windows
Active Directory domain, group, or user
IP address, machine name or application
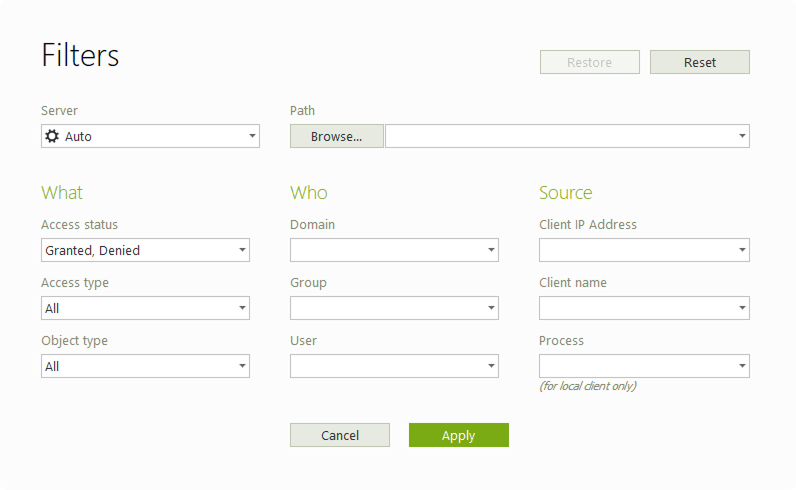
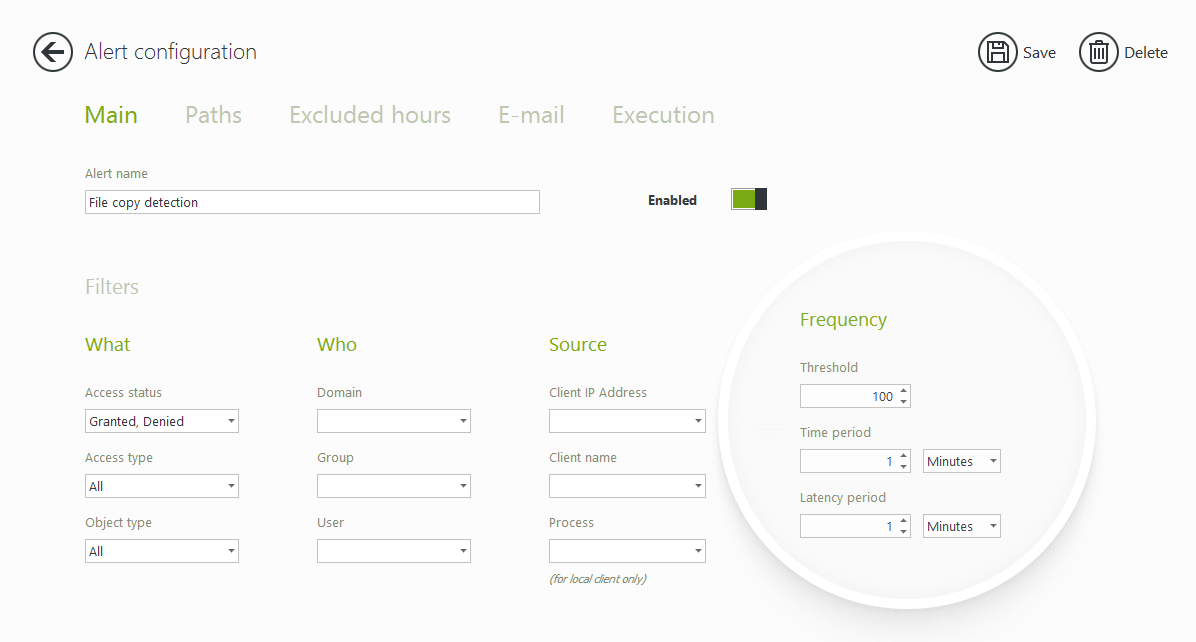
FileAudit not only monitors specific file access events but is able to gather data on the frequency of access over time. Should a user exceed a defined threshold within a set period, this will trigger an alert.
Because files aren't just on-prem anymore, FileAudit also supports cloud data monitoring across cloud platforms, such as Microsoft OneDrive for Business, Microsoft Teams, SharePoint Online, Google Drive, Dropbox Business, and Box.

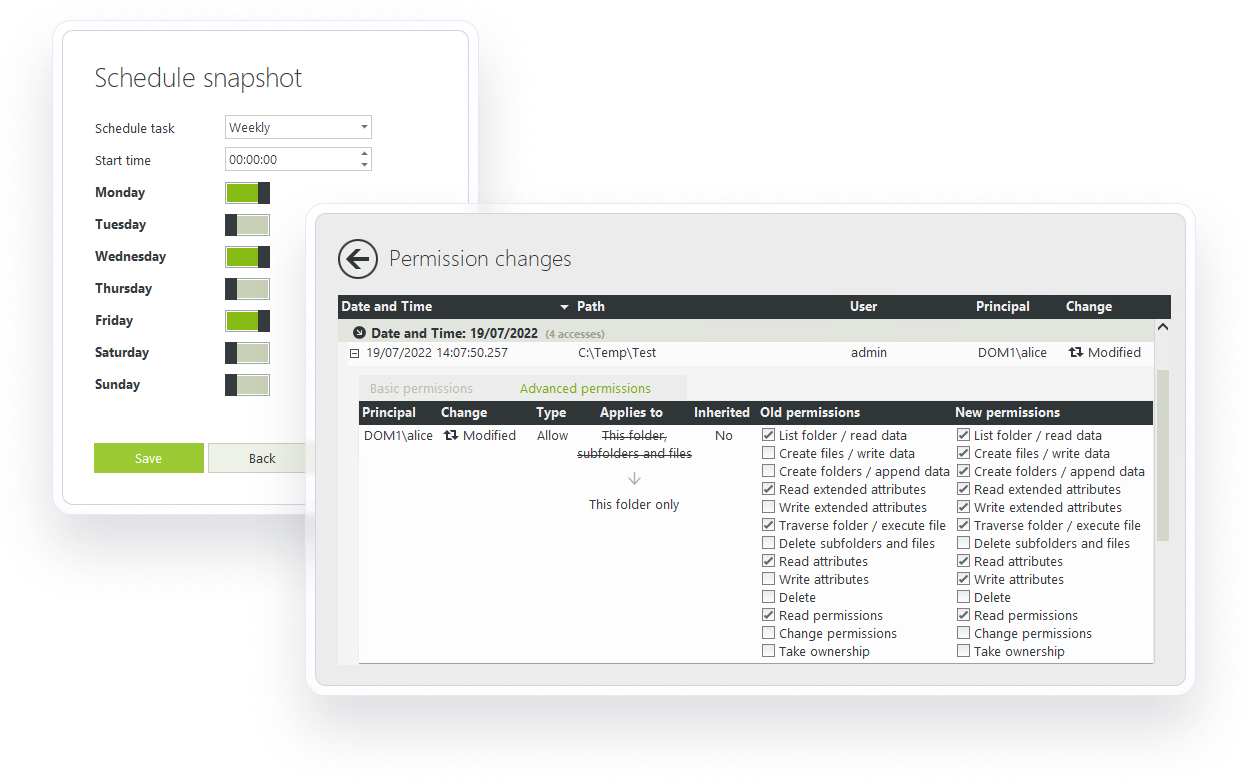
Another key capability is seeing who has access permissions, and when those permissions change. With Fileaudit, you can see who has access to what, spot permission changes, and remove outdated rights.
NTFS permissions reporting is important for staying compliant with cybersecurity regulations like HIPAA, GDPR, and PCI DSS.
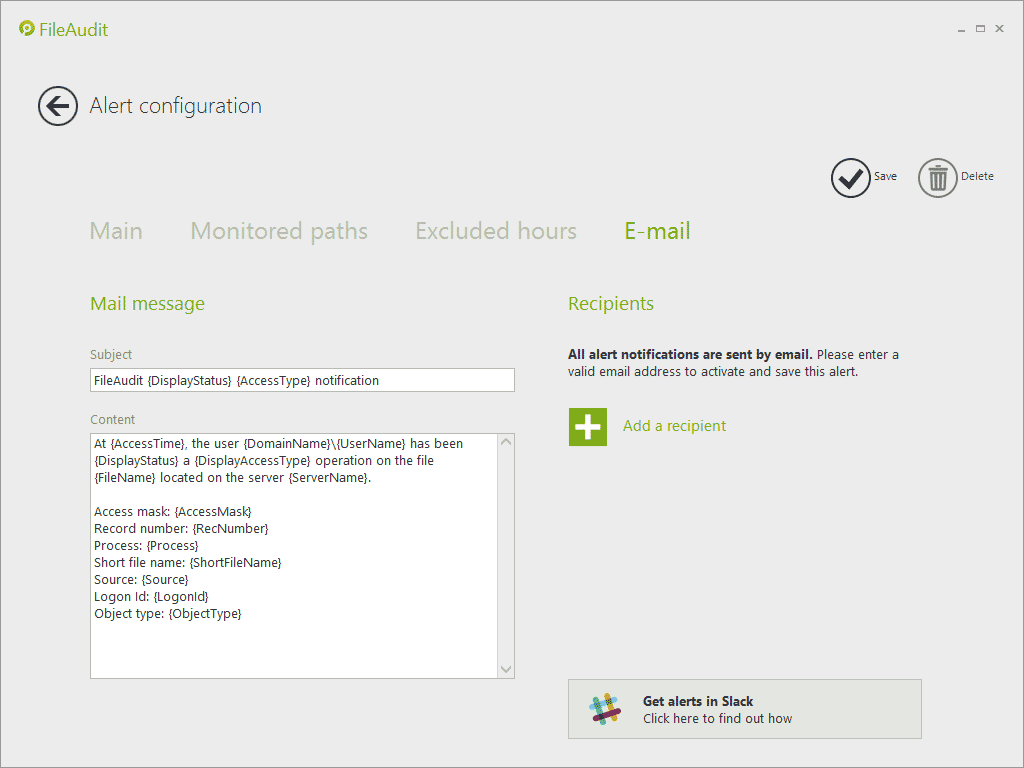
If FileAudit detects that an access threshold is reached, it will send an alert or text message to the admin detailing the event.
Then, it will apply any automated scripts you've set up to run after this alert is triggered. For example, if it detects a mass file copying or deletion, it will disable the Windows Active Directory user account.
For years, IT security has seen file auditing as a technology to help meet compliance requirements. Where threats existed, this was primarily insider abuse in specific business sectors such as finance.
Now, file auditing plays a crucial role in detecting and responding to ransomware attacks that target mass data encryption or theft. Meanwhile, legitimate account takeover phishing has driven the requirement to monitor all users at all times, not only those with privileged access.
But getting the balance right between monitoring, alerting, and automated response remains challenging. FileAudit gives security teams a clear, real-time single view of file access across your organization, so you can trigger an immediate, automated response the moment something goes wrong.
)
)
)