CMMC compliance: MFA strengthens security in the U.S. defense sector
With CMMC 2.0 requirements now rolling out across new contracts, the U.S. defense sector faces strong MFA requirements. Here's what to know about implementing MFA for CMCC compliance.
Updated December 15, 2025)
CMMC, the Cybersecurity Maturity Model Certification, is a set of standardized rules and best practices developed by the U.S. Department of Defense (DoD). CMMC 1.0 laid the foundation for defense contractors and organizations to meet specific security requirements. Now, CMMC 2.0 raises the cybersecurity bar higher with stronger access security and multi-factor authentication (MFA) implementation requirements.
Organizations are acting to ensure compliance with the CMMC 2.0 final rule, which the DoD will enforce starting November 10, 2025.
For federal IT pros, it's time to evaluate CMMC 2.0 readiness. In this article, we’ll walk you through CMMC MFA requirements and help you understand the new, broader requirements around strong authentication.
The CMMC program is designed as a comprehensive framework to enhance the cybersecurity posture of the defense industrial base (DIB).
The Department of Defense (DoD) developed this framework to safeguard sensitive data and Controlled Unclassified Information (CUI) throughout the supply chain, reducing the risk of cyber threats and ensuring the protection of national security interests.
CMMC has strong roots in NIST SP 800-171, which provides a set of security controls for safeguarding CUI in non-federal systems and organizations. Building on this foundation, the CMMC program aims to build a culture of cybersecurity resilience.
CMMC 1.0 measured cybersecurity maturity with five levels. But CMMC 2.0 compliance simplifies, trimming from five to just three distinct levels, each associated with specific requirements:
Level 1: The foundational stage, Level 1 includes 17 controls. It’s for organizations exclusively dealing with Federal Contract Information (FCI). At this level, organizations conduct self-assessments to ensure they meet the specified criteria. After the CMMC 2.0 rollout, organizations will need to conduct annual self-assessments.
Level 2: Intended for organizations that handle not only FCI but also CUI, Level 2 includes a comprehensive set of 110 practices, requiring third-party assessments to verify Level 2 certification.
Level 3: With over 110 practices, Level 3 is for organizations that handle classified or top-secret information. They must complete formal government assessments to confirm compliance with Level 3 cybersecurity measures.
Multi-factor authentication (MFA) plays a big role in CMMC 2.0 compliance, particularly to ensure secure access to sensitive and classified data.
MFA adds an extra layer of security beyond traditional username and password authentication. This requirement adds an extra security layer to verify the identity of the person trying to access privileged and non-privileged accounts.
Of course, CMMC takes seriously any unauthorized access to sensitive or classified data. Since MFA typically requires something the user knows (a password or a PIN) plus another factor (something the user has, like a push notification or a token), it reduces the risk of unauthorized access even if a password is compromised.
The CMMC Assessment Guide (Level 2) states:
“Use multifactor authentication for local and network access to privileged accounts and for network access to non-privileged accounts.”
So, as part of CMMC compliance, organizations must first identify privileged accounts. These accounts typically have elevated permissions and access to sensitive information. MFA is mandated for these accounts to provide an additional layer of security, ensuring that even if a privileged account is compromised, the attacker would still need a second authentication factor.
Additionally, the requirement to apply MFA across all users, both privileged and non-privileged, and across various session types, servers, and applications, ensures comprehensive coverage. This reduces potential security gaps and ensures that all access points to sensitive data are protected.
See how UserLock delivers CMMC MFA
See how UserLock fits your needs and explore common use cases
There are several common pitfalls that we see organizations usually face while implementing MFA for CMMC compliance. Below we discuss six of those challenges.
The first common mistake is failing to apply MFA consistently across all required access points. Some assessment objects (AOs) may require MFA for privileged local logon, while others may require it for network access. So, defense organizations must ensure that MFA is implemented wherever it’s mandated by the CMMC requirements.
The CMMC requirements apply to the entire environment, including all systems and accounts that manage access to CUI. This means that organizations need to comprehensively identify all accounts and access points that require MFA, which can be a complex task in large and diverse IT environments.
Some devices and applications may not easily support MFA. For example, certain firewall administrator consoles or legacy systems might lack built-in MFA capabilities. In such cases, organizations need to find creative solutions, such as using privileged access workstations (PAWs) or jump boxes that prompt for MFA before connecting to these administrative consoles.
Another thing we notice is that enforcing MFA consistently can still be difficult, especially in environments with a mix of legacy and modern systems. Organizations must ensure that MFA is applied uniformly across the board and that no exceptions or gaps exist.
Implementing MFA often requires the active involvement of users. Ensuring that users are aware of MFA requirements, understand how to use them, and are willing to adopt MFA practices can be a challenge. Resistance from users can hinder successful implementation.
Lastly, different assessors may interpret the CMMC requirements differently. Some may have a broader interpretation of which accounts require MFA. So, it’s important for organizations to align their MFA implementation with the most comprehensive interpretation to avoid compliance gaps.
Choosing the right MFA solution, especially in on-premise and hybrid Active Directory (AD) environments, presents unique challenges. Below we discuss three key considerations for defense organizations when selecting an MFA solution.
To bolster security, it’s necessary to prove MFA for every AD account. Embracing the least privilege approach, where users only have access to resources essential for their tasks, necessitates comprehensive MFA coverage. By adopting such an approach, defense organizations can minimize the risk of unauthorized access and data breaches.
In defense environments, demonstrating MFA across AD identity access is non-negotiable. However, this can be a challenging endeavor, particularly when managing multiple directories in a hybrid environment. Defense organizations need to seek MFA solutions that seamlessly integrate and authenticate identities across different AD directories, ensuring a unified security posture.
An effective MFA solution should provide comprehensive and detailed logging of all user activities. UserLock’s centralized audit, for example, facilitates comprehensive reporting on the login activity of AD users. This includes details such as the connected user, system source, duration of the session, and more. These logs must be readily accessible to IT administrators at defense organizations and agencies in real-time.
Managing a hybrid environment involves bridging the gap between on-premise and cloud-based applications. Defense organizations must invest in an MFA solution developed for on-premise AD that also offers the flexibility to secure access to SaaS applications such as Office 365. This approach minimizes administrative overhead while reducing the cost and time commitment of managing multiple MFA solutions.
Lastly, compliance with recognized security standards ensures that the MFA solution follows industry best practices. This adherence serves as a technical benchmark for security measures, guaranteeing that the MFA solution is designed to protect against known vulnerabilities and threats.
CMMC compliance is the essential prerequisite for securing sensitive data and government contracts, and without a robust solution, the path forward remains uncertain. UserLock is designed to fit right into your on-premises and hybrid AD environments to help simplify security management.
Plus, UserLock brings granular MFA to the forefront, verifying AD identity access across all session types.
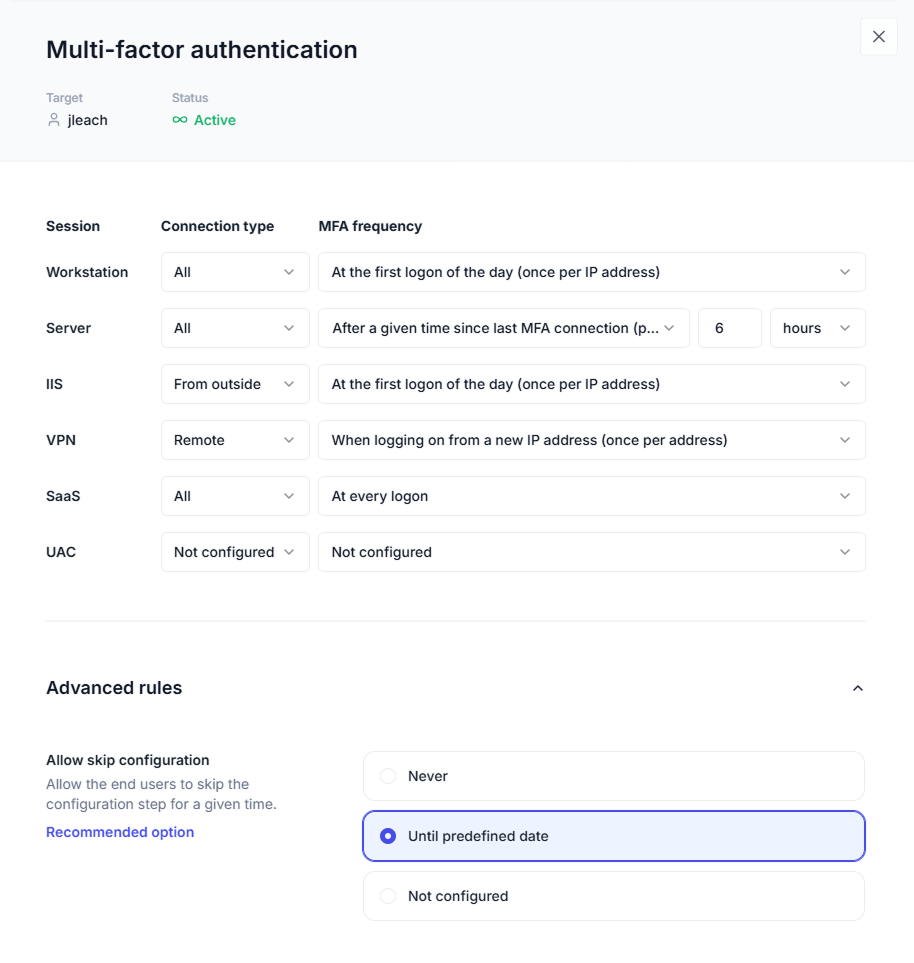
Whether your users are remote or on-site, privileged or non-privileged, accessing network or SaaS resources, UserLock delivers the simple, effective security you need to meet CMMC compliance requirements.
)
)