For better Windows network security, control user access
UserLock improves Windows network security by controlling user access to the network based on granular policies.
Published July 1, 2013)
One important way to improve Windows network security is to control users from accessing the network based on criteria and policies that you specify.
UserLock allows this kind of granular access control entry by restricting user logons according to customized user access policies. It continuously monitors all login and session events, automatically applying custom policies to permit or deny logins, workstation access and usage/connection time.
This post looks at the type of restrictions made and the level of granularity offered.
The defined protected accounts can be made up of users, user groups or Organizational Units (OU) onto which UserLock rules can be applied. User Protected accounts always override Group and OU Protected account settings. With Group and OU permissions you can choose the policy rule that UserLock should use.
Note: Because UserLock integrates with Active Directory, just type the user account name and UserLock will check for that account against Active Directory and add it in the console.
For each protected account, the following restrictions can then be set.
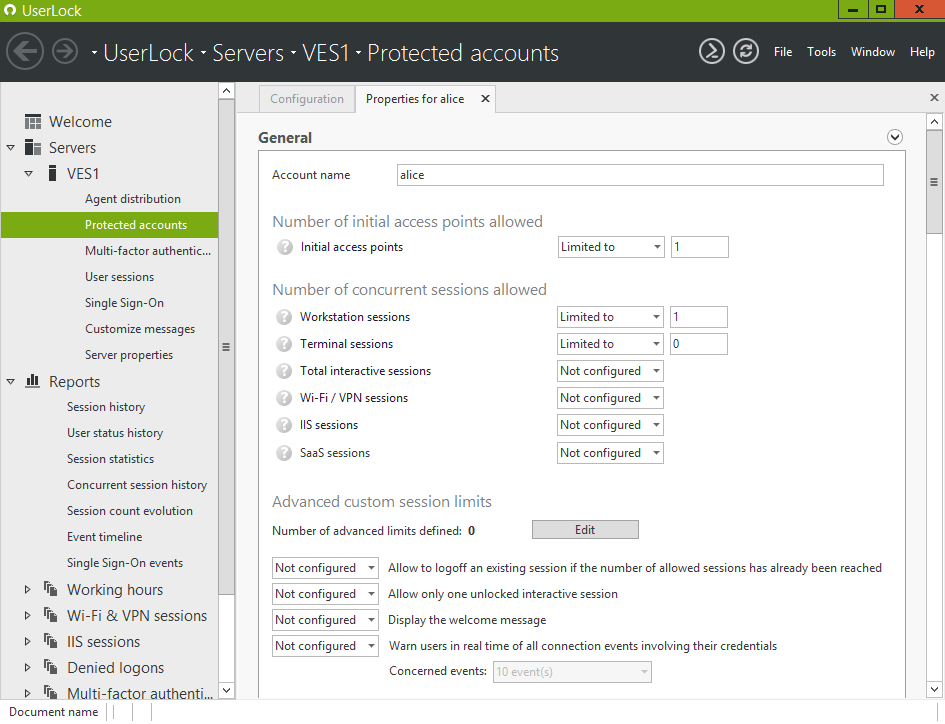
Define the number of concurrent sessions allowed. This includes the maximum number of simultaneous workstations where a user can be logged on, the maximum number of terminal sessions that a user can open and the total interactive sessions (workstations and terminal) allowed.
Restrict also the maximum number of simultaneous Wi-Fi/VPN sessions that a user can open (including 0 sessions) and allowed IIS sessions.
A maximum limit for combinations of several kinds of sessions can also be set.
An option is available to allow or deny a user to logoff an existing session if the number of allowed sessions has already been reached.
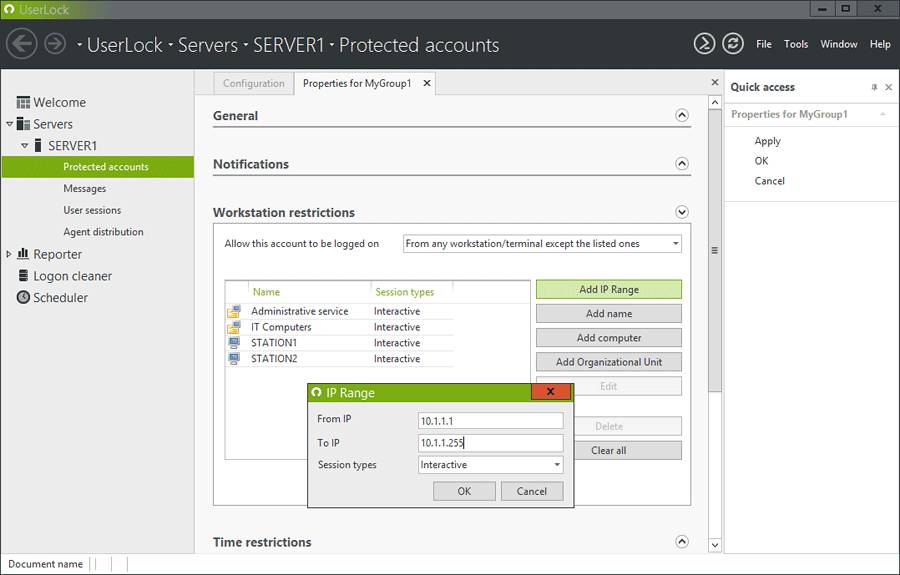
Restrict the workstations/terminals from where a protected account may logon. Set a restriction by an IP range, a computer name/IP or Organizational Unit.
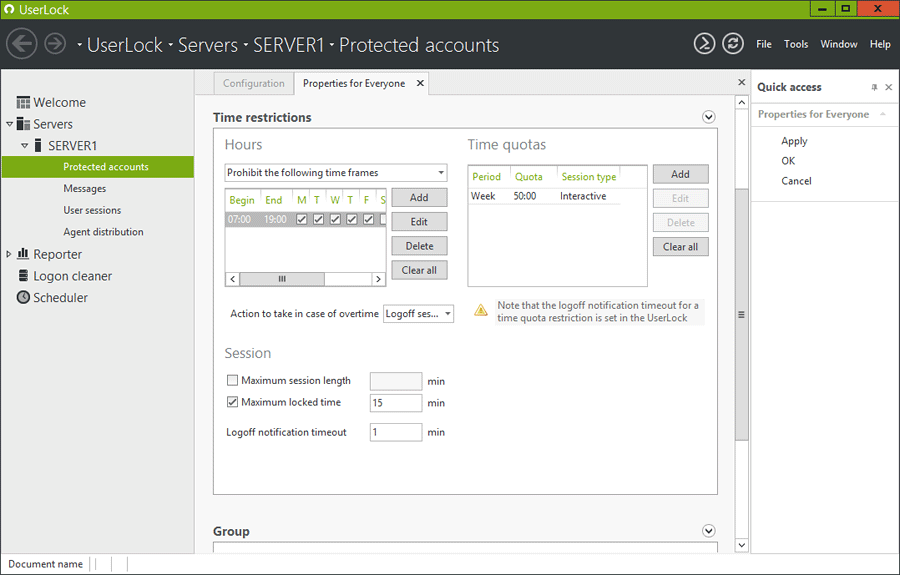
Define working hours and/or maximum session time for protected users. You can configure allowed logon hours during each day of the week. For each time frame you can specify the kind of session concerned by the restriction. In case of overtime on Interactive sessions you can choose to close the session, lock the session or do nothing.
A Time Quota can be set in hours/minutes for different periods (day, week, month, quarter, semester, year). Several time quotas can be defined for the same protected account allowing different time quotas for each type of session.
So with restrictions set you’re in control. Network protection and visibility automatically follows.
Reduces the ability of users to share credentials as it impacts their own ability to access the network.
Makes it impossible for a rogue user to use valid credentials at the same time as their legitimate owner
Offers security to a wireless network and the adoption of BYOD
Compliance with major regulations such as SOX, FISMA, HIPAA
)
)
)