The United Kingdom’s National Cyber Security Center (NCSC)’s Cyber Essentials program lays out cyber security guidelines to safeguard against the most common cyber threats. Backed by the U.K. government, the scheme has two levels of certification: Cyber Essentials, and Cyber Essentials Plus. Certification for both happens through the IASME consortium.
Organizations working with the U.K. government often need the Cyber Essentials Certification, as it’s a requirement for central government contracts involving handling sensitive and personal information or the provision of certain technical products and services. Other organizations go through the certification process to get a clear overview of their organization’s cyber security level. Some organizations may seek to reassure customers or attract new business with assurances that cyber security measures are in place.
IS Decisions’ multi-factor authentication (MFA) and access management solution, UserLock, can help your organization achieve and maintain compliance with key user access control requirements:
- Remove or disable user accounts when they’re no longer required
- Implement MFA
- Remove or disable special access privileges when no longer required
User access controls
“Ensure that user accounts:
- Are assigned to authorised individuals only
- Provide access to only those applications, computers and networks the user needs to carry out their role”
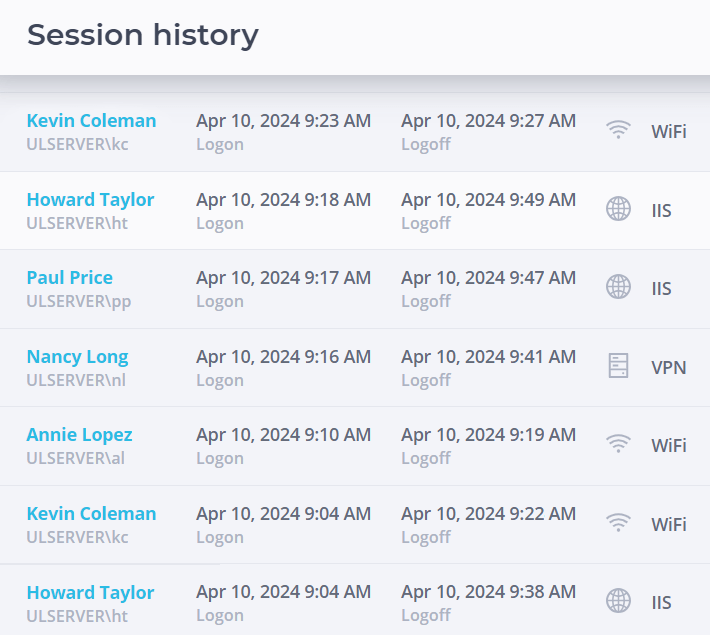
With UserLock, the administrator deploy MFA and also set granular, contextual access restrictions based on factors like IP address, time, machine, session type, or session type. UserLock also allows administrators to set access policies for different types of employees, by user, group, or organizational group (OU) in line with least privilege principles. In other words, you can prove your users only have access to the information they need to do their job. UserLock also allows administrators to record and report on all user connection events thanks to a central audit across the whole network.
“Your organisation must be in control of your user accounts and the access privileges that allow access to your organisational data and services. It’s important to note that this also includes third party accounts – for example accounts used by your support services. You also need to understand how user accounts authenticate and manage the authentication accordingly.”
UserLock can help your organization prove compliance with the following Cyber Essentials requirements for user access controls.
Remove or disable user accounts when they’re no longer required
Thanks to UserLock’s seamless integration with Active Directory, organizations can continue provisioning and de-provisioning accounts in Active Directory (AD). When users leave, UserLock works with AD to revoke their access to systems, resources, and data.
With one click, administrators can block network access by deactivating a user account, ending the current session, and preventing future login attempts.
Implement multi-factor authentication (MFA)
“As well as providing an extra layer of security for passwords that aren’t protected by the other technical controls, you should always use multi-factor authentication to give administrative accounts extra security, and accounts that are accessible from the internet.”
UserLock verifies the identity of all Active Directory accounts, whether privileged or non-privileged, with straightforward, effective MFA.
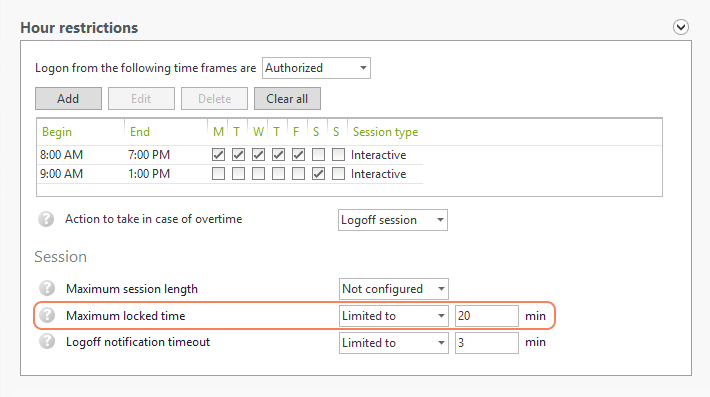
Administrators can choose how and when to require MFA.
There are two edit modes available for modifying the MFA settings. Make sure to read the documentation for the use case for each type of session to ensure users will receive an MFA prompt.
- All session types at once: By selecting this option, you can apply the same policy for all session types that are protected by UserLock.
- By session type: Select this option to apply different MFA policies for each session type.
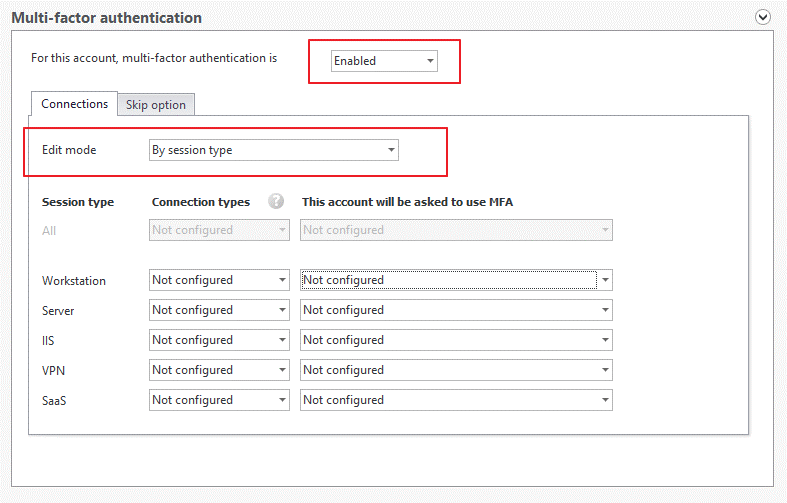
You can also apply MFA by connection type.
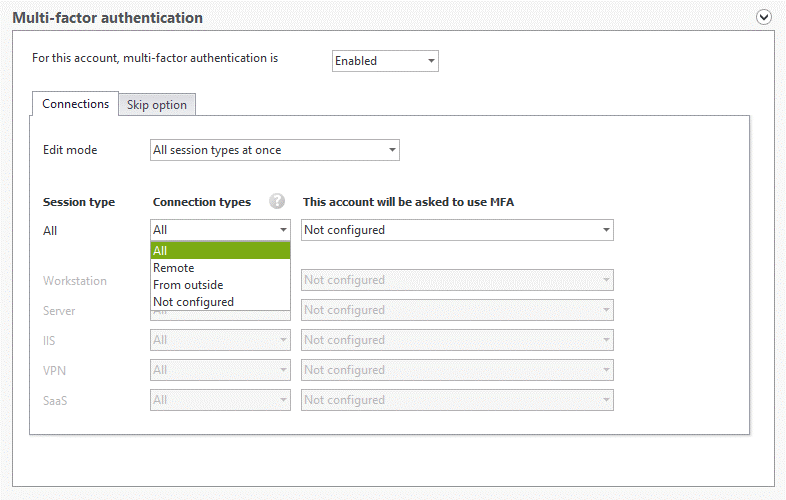
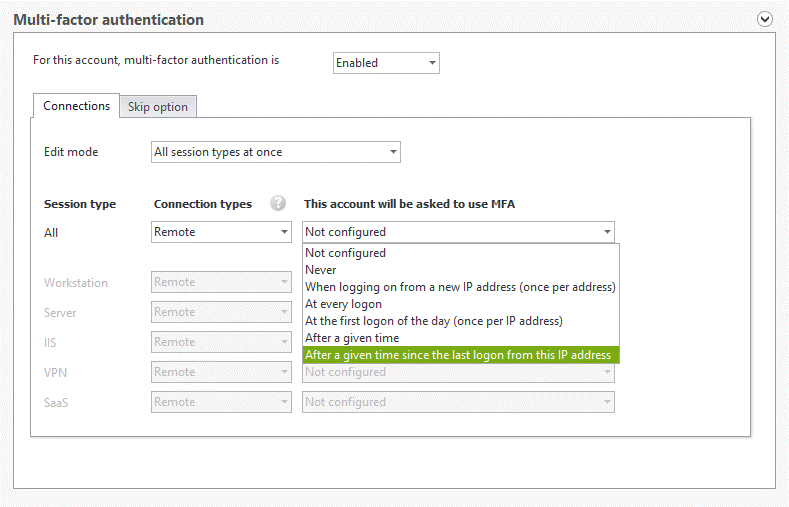
For each session type, you can choose how often to prompt your users with MFA.
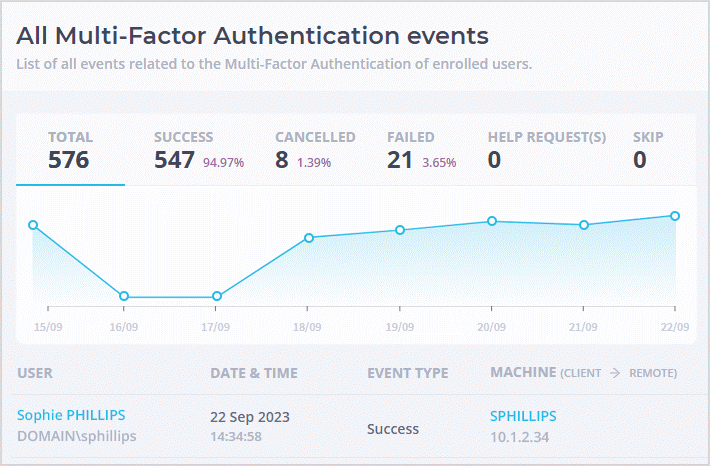
Administrators can also easily get visibility on all multi-factor events for support and reporting purposes.
Cyber Essentials guidelines also require that the additional, second factor used for MFA is either:
- A managed/enterprise device
- An app on a trusted device
- A physically separate token
- A known or trusted account
UserLock offers the flexibility to choose between two of the following MFA methods:
For more information on what MFA methods are acceptable as additional factors, see NCSC’s guidance on MFA.
Remove or disable special access privileges when no longer required
UserLock allows you to apply access policies by AD user, group, or organizational unit (OU). If a user’s role changes in Active Directory, that change will reflect in UserLock automatically. This eliminates the need for time-consuming, error-prone manual account creation and management.
UserLock can also track inactive users and monitor for suspicious user behavior.