Comply with SAMA Cybersecurity Framework
Here's how UserLock supports SAMA compliance across key domains at the highest levels.
The Saudi Central Bank, formerly known as the Saudi Arabian Monetary Authority, oversees the SAMA Cybersecurity Framework. Aiming to set a common standard for Saudi Arabian banking, insurance, and financial institutions, its goal is to improve the sector's cyber resilience.
Member organizations must implement robust identity and access controls, maintain audit-ready logs, and proactively monitor for threats.
To help organizations self-assess, review, and audit their cybersecurity maturity, SAMA defines six maturity levels. The expectation is for member organizations to reach at least Level 3, which requires implementing cybersecurity controls and monitoring compliance with documented cybersecurity policies, standards, and procedures.
For organizations with an on-premises Active Directory setup, meeting these requirements natively can be a challenge.
But compliance doesn't have to mean overhauling your entire IT infrastructure. That's where UserLock helps.
UserLock supports compliance across several key SAMA cybersecurity control areas under Domain 3.3: Cyber security operations and technology.
Specifically:
Identity and access management (3.3.5): Enforce granular MFA and access policies on AD users, groups, and OUs. Set policies by session type, device, location, and time. Prevent unauthorized access, limit access to "need-to-know", and report on an audit trail of all access events, including denied and failed attempts.
Cyber security event management (3.3.14): Monitor every user session in real time across the network and SaaS resources. Log access activity centrally and trigger alerts on abnormal access behavior.
Principle
"The Member Organization should restrict access to its information assets in line with their business requirements based on the need-to-have or need-to-know principles."
Objective
"To ensure that the Member Organization only provides authorized and sufficient access privileges to approved users."
Here's how UserLock supports SAMA's Identity and Access Management requirements.
UserLock allows you to implement strong multi-factor authentication and access controls on the on-premises AD identity.
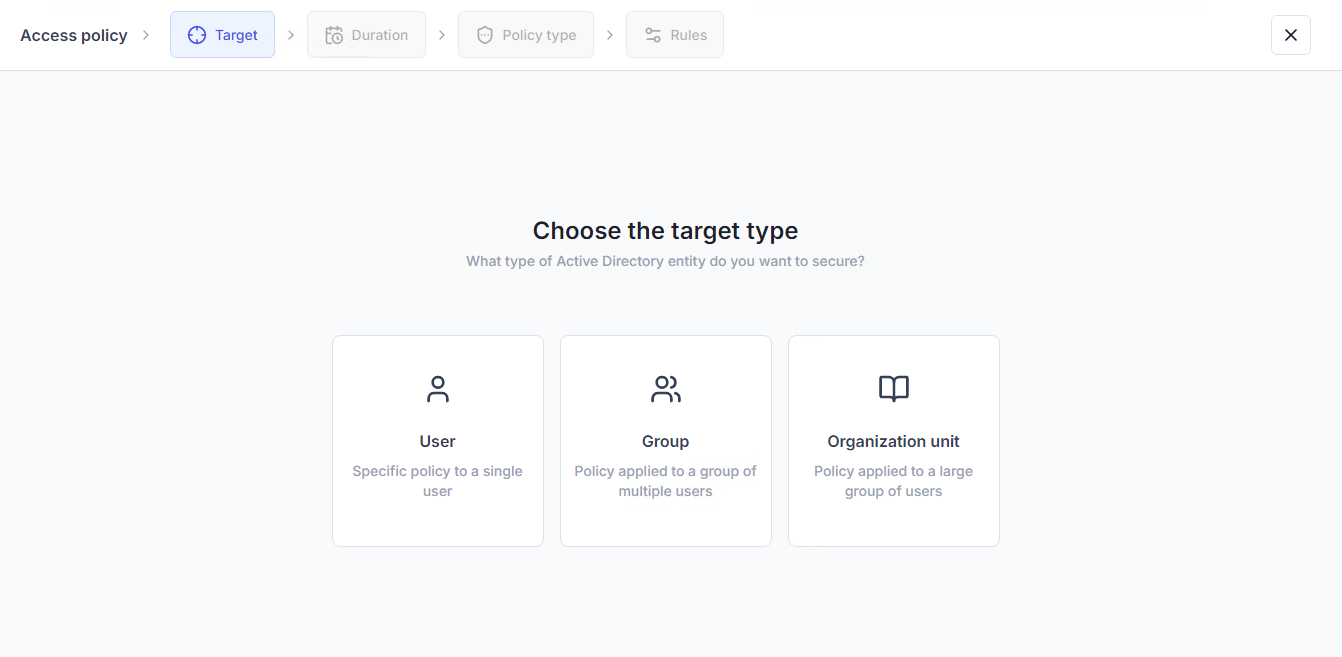
Thanks to UserLock's close integration with Active Directory, you can quickly apply policies to existing AD users, groups, and OUs.
This allows you to set access policies on a "need-to-know" or "need-to-have" basis according to user role.
Limit user access based on time, machine, geolocation, IP address, and more.
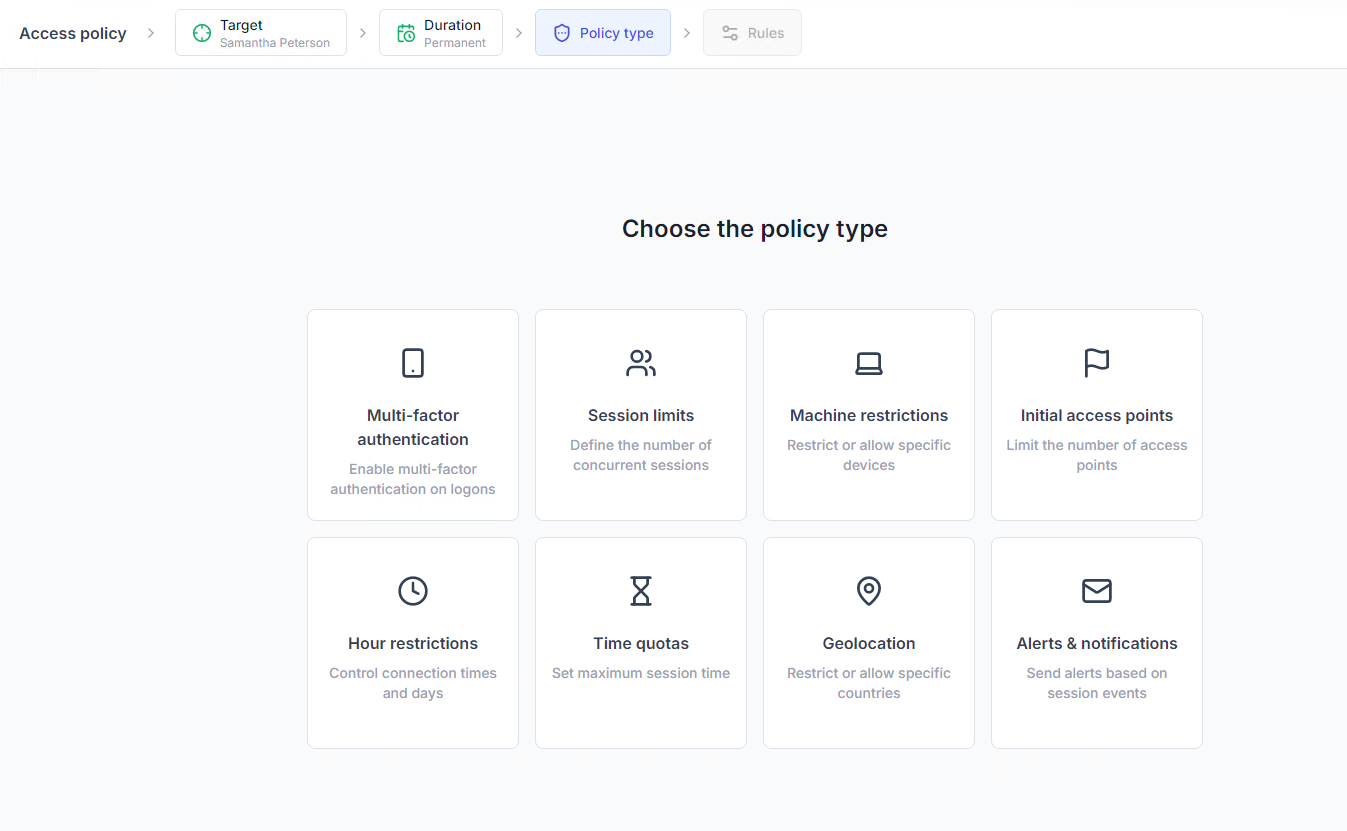
These restrictions help ensure access is appropriate and make it easy to implement SAMA requirements on privileged and remote access without frustrating end users.
Restrict concurrent logons and set a limit for simultaneous sessions to better prevent shared credentials and unauthorized access.

Implement MFA at the Windows logon, on remote access, SaaS, VPN, IIS, and UAC prompts. This helps satisfy Domain 4.3 requirements for strengthening identity verification, especially for remote access scenarios.
Granular controls put IT in control of finding the right balance between security and productivity for their team. Set different MFA prompt frequency for different connections and session types.

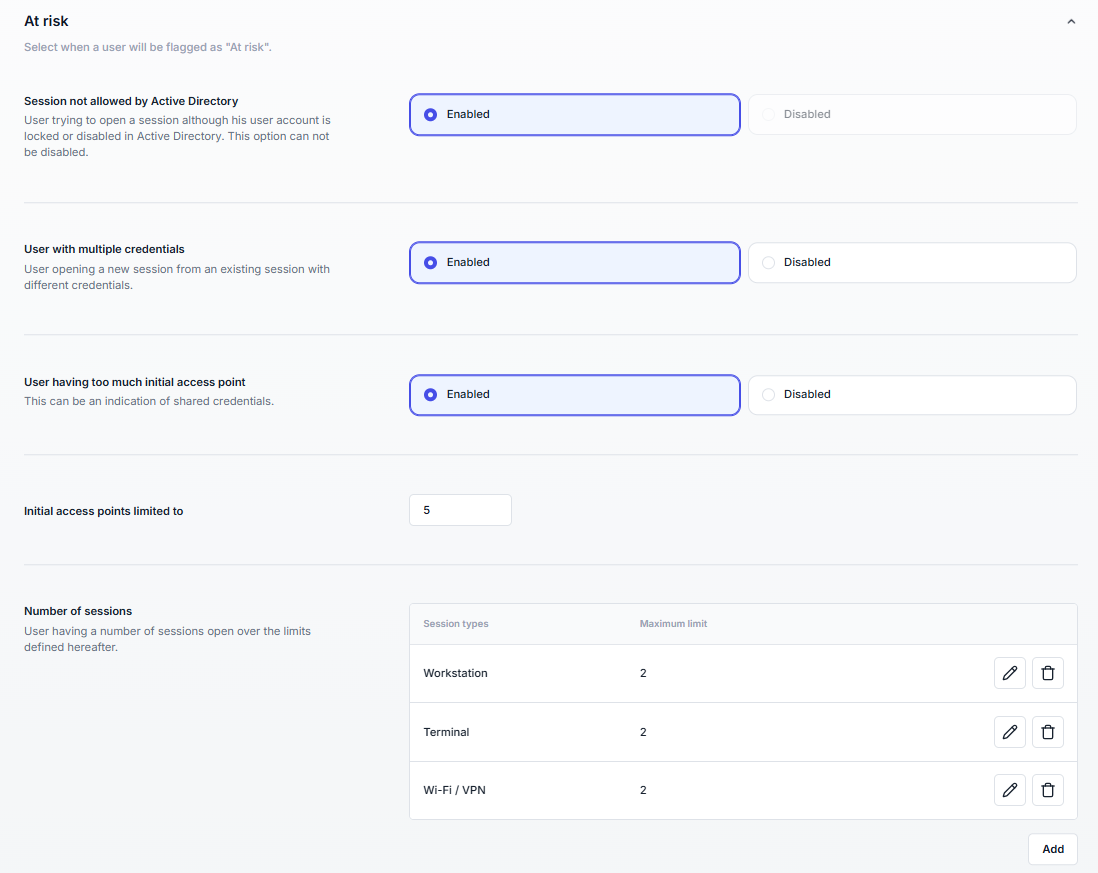
Set your own criteria for what counts as risky behavior, and get alerts when users are flagged as "At risk."
Principle
"The Member Organization should define, approve and implement a security event management process to analyze operational and security loggings and respond to security events. The effectiveness of this process should be measured and periodically evaluated."
Objective
"To ensure timely identification and response to anomalies or suspicious events within regard to information assets."
UserLock supports this requirement with:
Every logon, logoff, denied logon, and session connection is recorded in real time. Since all your access events are on one console, it's easy to review activity across the entire network and SaaS apps.
You can also drill down to see all access events per user. Logs are detailed, timestamped, and tamper-resistant.

View all user sessions as they happen, across all machines and session types. This helps security teams detect and react to anomalies right away.

Set up alerts for IT and end users based on unusual access attempts, logon failures, or access outside authorized hours or locations.
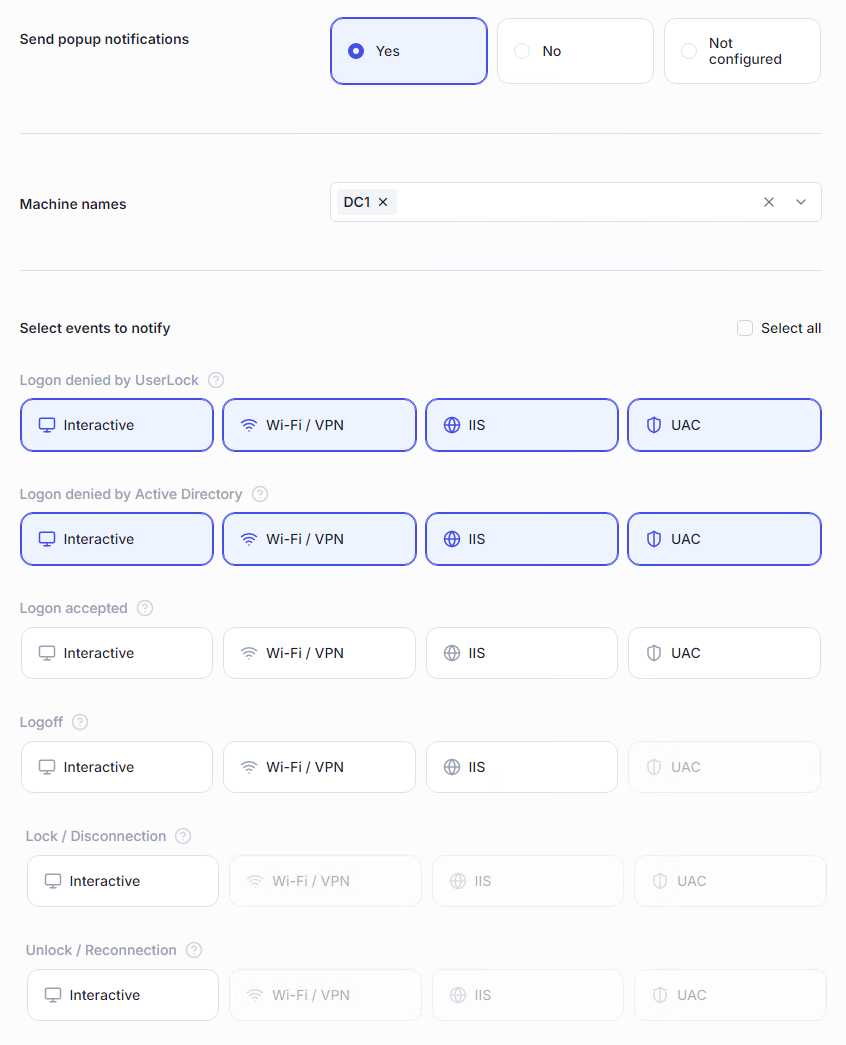
Block a user or force a logoff when suspicious activity is detected, reducing response time and potential damage.

Create custom reports to support compliance audits and schedule or export them for internal reviews.
Powerful filters and custom views support faster IT forensics and resolution.

Using webhooks and the UserLock API, you can also feed UserLock's granular logon data into your SIEM solution or other applications.
Together, UserLock's capabilities strengthen your organization's ability to meet SAMA requirements and demonstrate resilience in the face of security threats.
No infrastructure overhaul. Works with your existing on-prem or hybrid AD setup.
Fast to deploy. Get up and running quickly, without deep technical changes.
Built for security, compliance follows. Trusted by financial institutions and regulated industries worldwide.
Scalable. Whether you have 50 users or 5,000, UserLock adapts to your needs.