Active Directory hybrid identity: Extend on-premise Active Directory identity to Entra ID
There's middle ground between sticking with the limitations of Active Directory and moving identity to Entra ID.
Published November 27, 2024)
Windows is poised uneasily between two versions of how identity and access management (IAM) should work. On the one hand, Entra ID is the future, a world in which a growing amount of network infrastructure is hosted in third-party environments, beyond the traditional datacenter. At the same time, there are still a lot of AD networks out there that work perfectly well.
But there’s no doubt that organizations looking at a hybrid future are caught between the limitations of their existing AD and a move to Microsoft’s cloud platform and Entra ID.
The good news is that with UserLock sticking with AD does not have to lead to additional layers of management and complexity. Through UserLock, organizations can create a bridge to connect two completely different worlds in a way that gives on-premise-first organizations the best parts of both.
Unavoidably, today’s Windows admins must operate within an increasingly complex hybrid world. The networks they grew up with were based around Active Directory (AD) as the Windows IAM solution. But Microsoft’s increasing focus on its hosted cloud directory service, Entra ID (formerly Azure AD), implies that organizations must choose one over the other. Let's look at the advantages of each.
Entra ID integrates the Microsoft 365 applications most organizations use into a single platform.
Microsoft does the service provision for organizations, freeing them from having to run complex infrastructure across multiple locations.
Entra ID makes it easy to apply security policies and controls, including single sign-on (SSO) and multi-factor authentication (MFA).
MFA connectivity, in particular, no longer depends on VPNs.
Security teams retain full control over the IAM in AD without having to rely on third-party security.
The organization gets certainty about data residency, which is important for strict regulatory standards.
Less reliance on online connectivity.
On-premise AD is compatible with many older, legacy applications.
How do organizations figure out which side of this divide they fall? This depends on their long-term objectives, which fall into three main groups.
1. They plan to move to the cloud, and their goal is to move wholesale to Entra ID over time while retreating from on-premise applications.
Why would they take this route? Simplicity is usually cited as a big driver here, but it also suits organizations that must invest in new infrastructure on an ongoing basis, for example those with a heavy bias towards software development, services or ecommerce.
Why would they take this route? The big motivations here to meet regulatory requirements (including those regarding data residency), and to support legacy applications not supported by Entra ID or the cloud.
For organizations in sectors such as finance, critical infrastructure and government, remaining in control of the AD directory service is non-negotiable. For these organizations, keeping the directory service on-premise is paramount.
3. They are more on-premise than cloud but still want to take advantage of Entra ID for specific features.
Why would they do this? Usually because they prefer to extend the life of their current IAM setup for operational or financial reasons but would still like to standardize on cloud applications such as Microsoft 365. Security protections such as MFA also become more convenient because they no longer depend on data center connectivity.
Most organizations fall into this third group, meaning it’s about weighing up pros and cons. What’s clear is that even organizations committed to using on-premise will often still need to accommodate Entra ID within their setup.
The two IAM systems, AD and Entra ID, share a common lineage and many underlying principles but are designed to operate within very different environments. They are managed in different ways and enforce controls such as security in different ways.
What most organizations end up with is a hybrid identity approach in which they prioritize elements of both on-premise AD and Entra ID as a way of getting the best out of both worlds. However, this carries risks. Getting hybrid integration wrong can create either security weak spots or generate complexity leading to extra management overhead.
Organizations need tools that allow them to secure access to on-premises and SaaS resources without compromising either. This shouldn't be difficult. But Microsoft 365 applications assume Entra ID as the IAM and will not work directly with AD.
To address this problem, Microsoft provides tools to help integration:
Active Directory Federated Services (AD FS) is an older tool that allows organizations to continue using their on-premise AD identity while federating and synchronizing with Entra ID and Microsoft 365 through a single SSO credential.
Entra Connect Sync (Formerly Azure AD Connect) is an on-premise tool that synchronizes on-premise AD with cloud Entra AD.
Entra Cloud Sync does, as its name suggests, an almost identical job while being hosted in the cloud.
Unfortunately, all of these Microsoft native tools can be complex to set up and manage. They also come with a range of limitations.
UserLock brings a clear advantage to on-premise and hybrid environments: the ability to keep things simple.
That's because UserLock is designed around the principle that on-premise networks should retain as much control as possible. This allows IT to retain the centralization and control that is so important in on-premise environments.
Through UserLock, organizations can continue to use existing on-premise AD identity while securely integrating access to Entra ID, Microsoft 365 and other SaaS applications.
UserLock combines SAML-based single sign-on (SSO) with MFA and access controls to cover the main use cases in on-premise and hybrid networking. So, there's no need for complex middleware riddled with hidden compromises.
Schedule a personalized demo
See how UserLock fits your needs and explore common use cases
Through UserLock, authentication can be federated to UserLock SSO via Entra ID, giving employees secure MFA on Microsoft 365 access in a way that seamlessly integrates secure access to both on-premise and remote access environments.
)
)
)
)
)
)
)
When a user tries to access a Microsoft 365 application from home or work,this request contacts Entra ID for authentication. Because this is federated with UserLock SSO, Entra ID passes UserLock the request. UserLock SSO processes the request after checking the user’s credentials and authorization in the on-premise AD. With UserLock, you get the simplicity of only maintaining one identity, the on-premise identity, for access to all line of business apps.
When using SSO as described above, it is essential to enable MFA an extra security check. Once SSO has been configured, MFA can be turned on in UserLock for the enrolled user, group or organizational unit (OU).
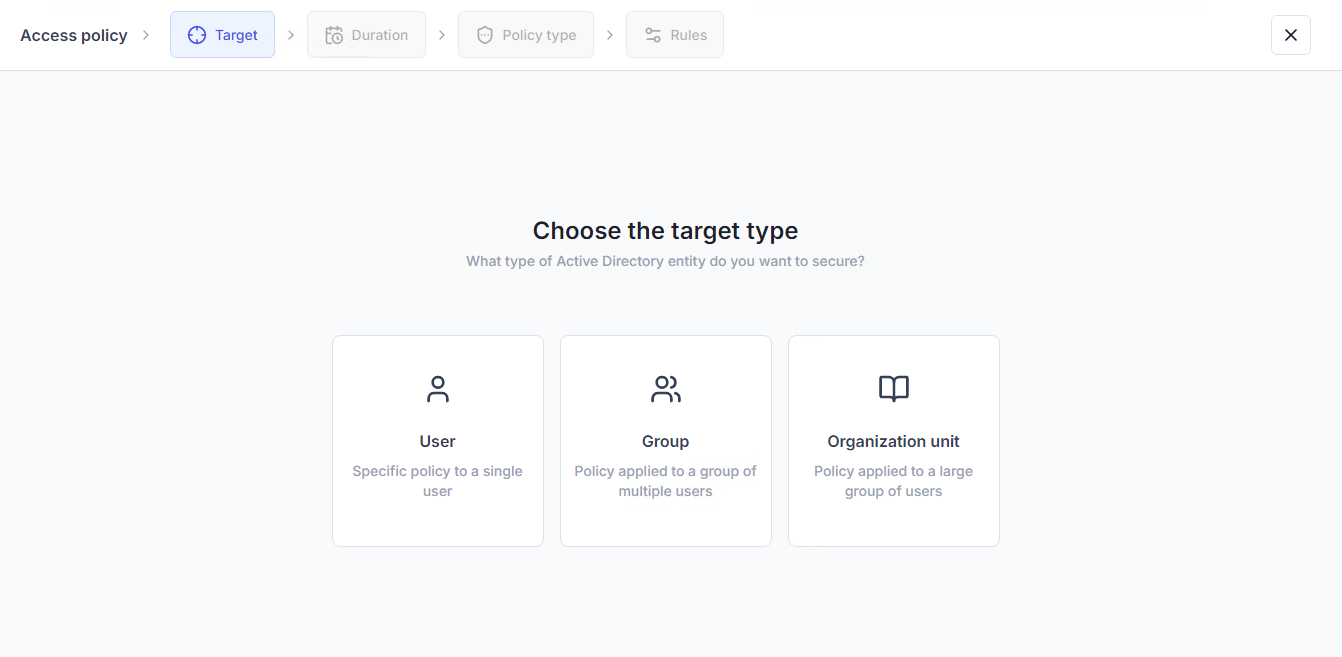
UserLock allows admins to set MFA by connection type, including by workstation, server, IIS application, VPN, and in the case of Microsoft 365, SaaS.
)
)
)
)
)
)
)
Admins can also apply MFA policies in a highly granular way which differentiates between, say internal and external/SaaS access.
Admins can also specify how often to prompt their end users for MFA, and offer up to two MFA methods (push notifications, authentication apps, or YubiKey/Token2 hardware tokens).
)
)
)
)
)
)
)
Setting up MFA and SSO is simple with the UserLock configuration wizard.
)
)
)
)
)
)
)
MFA in hybrid environments is often a complex problem. UserLock makes this as simple as possible while keeping the IAM handling authentication (on prem AD) onsite.
All organizations embracing a hybrid future face the difficult question of whether on prem AD or Entra ID will be their primary IAM system. There is no right or wrong answer, but which approach is adopted has major implications for security management.
Each has its pros and cons but there is no escaping that sticking with on-premise AD offers more control. In some organizations, this remains a major requirement.
With UserLock, admins can keep things simple. By keeping authentication in on-premise AD, even for access to SaaS, UserLock gives organizations built around on-premise infrastructure the benefits of secure hybrid access, without identity sprawl.
)
)
)