How to develop a sound access management strategy in Azure Active Directory?
Improve your Azure Active Directory access-management protocols to protect sensitive data with these tips and tricks.
Published March 11, 2021)
If you’ve worked with Azure Active Directory (now Microsoft Entra ID), odds are good that you’ve heard “IAM” uttered more than a few times. Indeed, Identity and Access Management plays a central role in organizational IT security. Carefully controlling who can access what keeps unauthorized individuals from viewing sensitive data. Admins do this by granularly managing groups, users, policies, and roles.
Creating and overseeing these groups according to privilege is vitally important. However, many admins struggle to implement these controls effectively — especially as organizations scale. There are many tools and practices that IT professionals can leverage. Awareness, unfortunately, is occasionally lacking.
Here we’ll offer some fundamental tips and tricks for improving your Azure AD access management protocols.
This is the unequivocal first step in forming a strategy. Your organization houses mountains of data, especially if you’re an enterprise entity. You can’t give everyone the proverbial master key, of course. That would be too reckless and even violate many compliance guidelines (HIPAA, SOX, GBLA, PCI, etc.). For example, you wouldn’t want the development team to access financial records, yet management or HR likely need such access.
)
The goal should be to match access level with role. This helps prevent sensitive information from inadvertently falling into the wrong hands, even if intent isn’t malicious. Role-based access control (RBAC) was created with this in mind. Each employee is granted unique permissions by their respective admin.
You can create role groups — populated by employees with comparable roles — that share similar access privileges. RBAC’s advantage stems from this arrangement. When someone leaves a position or changes jobs, there’s no need to assign new policies. Simply assign that individual to another role, or drop them from the current group altogether.
Unfortunately, RBAC is either not secure or configurable enough for some use cases. You can instead adopt attribute-based access control (ABAC) — which works in conjunction with object characteristics. ABAC is determined by considering the following:
Resource attributes: These apply to folders, files, repositories, libraries, and other data (according to creation date, owner, and sensitivity)
Environmental attributes: These are contextually based, according to access time and location, device, protocol, risk signal, encryption, and user behavioral patterns
User attributes: These include name, role, security clearance, etc.
As you can imagine, there are many possible attribute combinations at play here. These feed into ABAC’s overall level of configurability. Even though RBAC isn’t considered a blanket policy, it pales in comparison to ABAC for organizations needing the latter.
RBAC and ABAC can be used in concert, with ABAC acting as a fine-grained supplement. ABAC is more demanding and requires more processing power. However, your sensitive resources will be well-protected using this tandem.
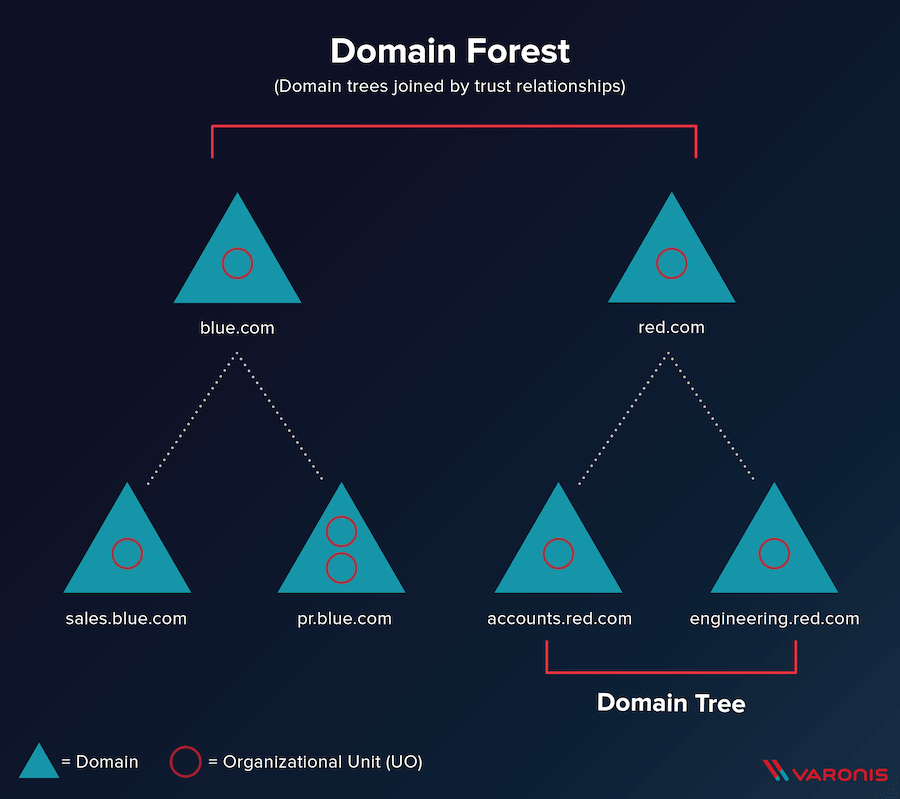
Say you want to understand how everything in your Azure AD environment is organized. AD implements a “tree” model — in which domains reside at the top, and subdomains are connected underneath hierarchically. Each of these domains contains objects, notably of which are users, groups, and contacts.
Additionally, multiple trees form a forest in Azure AD. This type of structure makes it easier to maintain the various elements in AD. We know that users are assigned to domains, and each user has permissions. By learning how to navigate this structure, you and other admins can better understand how user access is determined.
When working with directory services, teams may find that Lightweight Directory Access Protocol (LDAP) provides quick authentication and pinpointing of important, internal information. While teams traditionally paired LDAP with on-premises infrastructure (and still do), equivalent functionality is available for cloud-based deployments. In fact, Azure AD’s domain services facilitate cloud transitions.
Azure AD uses domain services as a means of storing information, and making it available. LDAP provides a layer of access management between users and these network data stores. It’s also ideal for remote employees.
For example, a virtual user might connect to company networks via VPN. LDAP bridges the gap between this virtual network and Azure AD Domain Services. Meanwhile, AD feeds information on users, passwords, and groups to Azure AD using Azure AD Connect. That converged rendezvous point is where user productivity happens.
LDAP is thus integral to authenticating users — when they’re attempting to access web apps, NAS devices, and SAMBA servers. Version 3 of the protocol also leverages TLS and SSL when connecting. Such measures help further secure your user data while preventing injection attacks.
A simpler way to control access across Azure AD is with ACLs, which are lists of permissions given to users and groups. These permissions impact access to files and directories. Access control lists are great because they’re relatively easy to set up. They may also control the following:
NFS permissions
Read, write, and execute permissions for individuals
Read, write, and execute permissions for groups
You can build multiple ACLs as needed. While such lists can delegate access, they can also deny it.
Azure AD’s management tools are powerful, yet often demand a lot from admins as a result. There’s plenty of manual control to seize, and while that’s appealing, it can render access management more tedious. Conversely, external tools commonly introduce automation to streamline these processes.
Popular options like SolarWinds Permissions Analyzer are free, and provide instant visibility into your ecosystem. Because it integrates with AD, the software can scan through your directories to obtain permissions and privileges. These are displayed visually in an organized fashion.
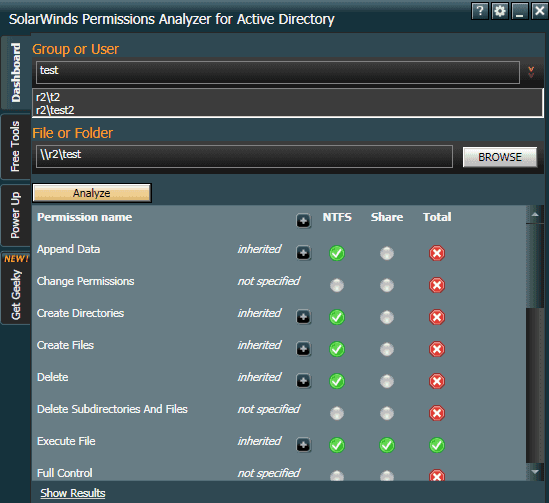
While you can’t manipulate permissions directly through something like Permissions Analyzer (which is read-only, like many others), it provides a basis from which you can act. Should permissions not align with expectations, it’s easy to make adjustments within AD.
Similarly, alternatives like SolarWinds Access Rights Manager or ManageEngine AD360 have numerous benefits:
File share auditing
SharePoint access management
User account provisioning and de-provisioning
Active Directory change monitoring
Password management
The tooling ecosystem based around Azure AD is strong. Preferred functionality, GUI affinity, and cost will determine which is right for you.
As you can see, one can approach Azure AD access management from many directions. This isn’t an exhaustive list of what to consider; however, we hope it provides a solid starting point for you and other AD admins. As a final mention, it would also be smart to assess credential-checking systems.
Be sure to follow best practices when determining how much power your users have. That process is high-priority for any admin. Proprietary (protected) data is highly valuable, and account information should be safeguarded against prying eyes. These choices will influence how secure and compliant your entire system is in the long run.
UserLock provides another option to help organizations manage and secure users accessing cloud services. It allows users to log in only once with their existing on premise AD credentials to seamlessly access both network resources and multiple cloud services.
Supporting SAML 2.0 protocol it continues to use on-premise Active Directory as the authoritative user directory to enable federated authentication of Office 365 and other cloud applications.
Installed in minutes on a standard Windows Server, UserLock's Active Directory single sign-on (SSO) for all resources is combined with multi-factor authentication (MFA) for Active Directory to provide effective, granular, and affordable security.
)
)
)
)
)
)