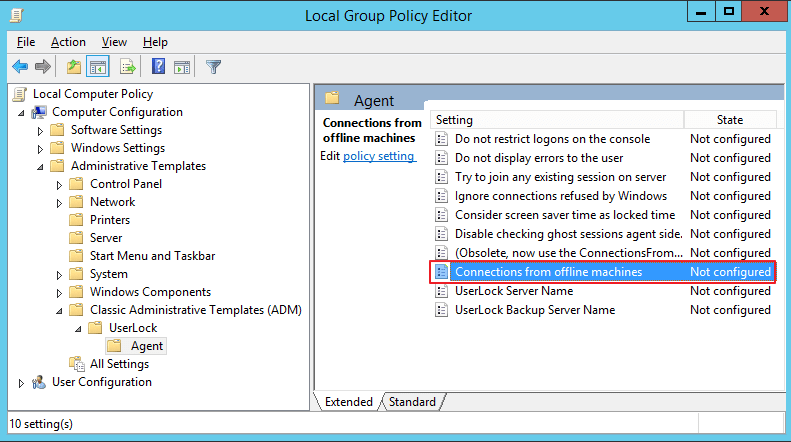
How to manage offline connections
Offline connections occur during any one of the following scenarios:
- If the network is not available on the agent or service side;
- If the Primary or Backup servers are not available;
- If the prerequisites are not met between the agent and the service.
By default, for these connections UserLock will not enforce any restrictions. All session events will be logged locally on machines, and communicated back to the server once communication is restored. For further information please refer to What happens if the UserLock Primary server is down?
It is possible to manage offline connections by accessing the server properties of the Userlock console in order to achieve one of the following settings:
- Always allow connections
- Ask for MFA
- Always deny connections
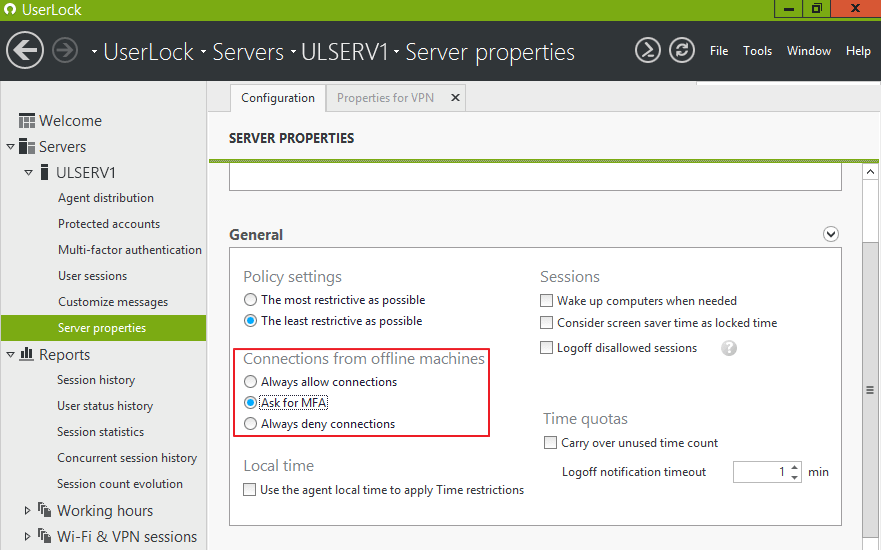
This setting applies if an interactive logon, unlock or reconnect event occurs on a computer where the Desktop UserLock Agent is installed (whether the “ApplyRestrictionsOnUnlock” advanced setting is enabled or disabled).
Always allow connections
By default this option is selected. Users will be able to login despite their machine being offline.
Ask for MFA
MFA can be enforced for offline connections by selecting the option “Ask for MFA”. This will apply to users who are already enrolled in MFA.
The connection will be allowed if the user already connected to the machine while on the network and with the agent (10.2 or higher) installed. MFA will be requested if configured.
This table explains how the “Ask for MFA” setting in the server properties behaves in the following scenarios. This setting is global, so depending on the scenarios listed below, the end user will have to enter an MFA code, logon without MFA or their logon will be denied.
For MFA to work offline, the desktop agent must be already installed on the client machine that is offline, and the user must have authenticated at least once on that machine with MFA within the corporate network.
| If... | ...Then | ||||
| User logged on once within network | User authenticated w/MFA within network | User with MFA activated | MFA required | Logon Accepted | Logon Denied |
| Yes | Yes | Yes | check_circle | ||
| Yes | No | Yes or No | check_circle | ||
| No | No | Yes or No | check_circle | ||
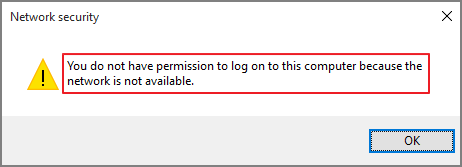
Always deny connections
This option will deny offline connections.
Error displayed:
Additional Information
This setting applies uniquely to interactive sessions. As these sessions are controlled by the Desktop agent installed locally on the machine, a network failure could prevent the agent from communicating with the UserLock server and therefore allow a logon to take place. Other types of sessions Wi-Fi, VPN and IIS sessions are managed through NPS, IIS and RRAS UserLock agents, which are installed on Windows servers. Since these session types operate differently they are not subject to the same type of behavior.
Once UserLock is reachable, the corresponding session events are sent to the UserLock service, which writes them to the database with EventType 4 (logon denied by UserLock) and LogonInfo 2048 (new reason “UserLock inaccessible” for logons denied by UserLock).
If the welcome message is enabled, end users will be notified of such events upon the next successful login. The text included avoids any mention of the solution "UserLock":
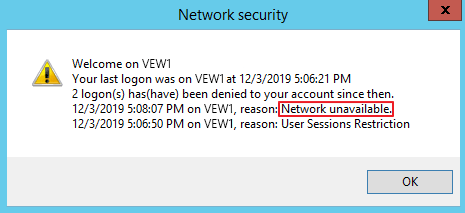
UserLock administrators can see these events in the following reports:
- “Session history” report: logons denied by UserLock for reason "UserLock inaccessible".
- "All denied logon" report: "UserLock inaccessible" is available in the "UserLock deny reason filter" field.
- "Logon denied by UserLock" report: "UserLock inaccessible" is available in the "UserLock deny reason filter" field.
Reminder about Windows cache and interactive logons
As explained on this page, in the case where the domain controller is not available, Windows allows interactive logons if the credentials used are part of the previous logons cached on that computer. The default value for this setting is 10 logons; possible values range from 0 to 50.
Optionally configuring this setting via Group Policies
Configuring this setting within the server properties applies it to all users. You can use this procedure through Group Policies (overriding server properties) to apply this restriction to specific organizational units.
This setting located within these policies is “Connections from offline machines”: