Active Directory user logon logoff security
With UserLock, control, monitor and audit all Active Directory User Logon Logoff Events in a more granular way than Microsoft Windows' Group Policy.
)
)
)
)
)
So you want to control Active Directory (AD) user access in a more granular way than native Windows Group Policy? You want to add multi-factor authentication? You want to further restrict users from accessing the network based on criteria you specify? And you want to be alerted to any other suspicious logon activity — crucially before that activity becomes a serious problem?
You're right. This type of logon/logoff security is no longer just a concern for highly regulated industries that want to meet compliance. It is for any organization at risk of a security breach that stems from compromised AD user accounts.
As one expert review notes, “UserLock allows you to do what it says it will do — control all aspects of Active Directory user login activity.“
Extend Active Directory user logon logoff security
UserLock gives network administrators a way to control all authenticated user sessions:
If an AD user account is stolen, access to the network from this compromised account will be automatically denied.
Careless user behavior is also protected, UserLock renders password sharing useless and secures logged in workstations left unattended.
With UserLock helping to verify authenticated users claimed identity, all access can be attributed to an individual user. This helps discourage any malicious activity and offers a comprehensive audit on all session access history — and access attempts.
And what’s more, it does this with a simple and non disruptive technology that works alongside Microsoft Active Directory to extend logon security, not replace or overwrite it.
UserLock is a client server application capable of auditing and controlling different type of user access connections. UserLock implements its authorization functionality on top of Microsoft Active Directory authentication and relies on micro-agents.
Non-disruptive technology
With UserLock, no modifications are made to Active Directory or its schema.
Fast implementation
UserLock can be hosted on any server member of the domain and is managed remotely on workstations or through a web console anywhere on the network.
Fast agent deployment
A micro agent is deployed automatically (or if preferred manually) on all machines. Once installed all access connections are detected and saved in the UserLock database.
Across all session types
UserLock offers several agent types according to the types of session it has to monitor (Workstation, terminal, Wi-Fi & VPN, SaaS, and IIS).
How does UserLock work?
The user enters their credentials to log on or to establish a connection to the domain network. These credentials are verified and validated against Active Directory. If the authentication process fails, the connection will be refused by Windows and UserLock does not intervene. The agent will however notify the UserLock server about this logon failure (and be available for reporting).
If the authentication is successful, the UserLock agent will transmit to the UserLock server all information about the context of the connection requested. The UserLock server will then process and analyze the data transmitted by the agent to check access control rules, trigger any alerts, refresh session information and save the user connection event in the database. The server then communicates its decision to the agent regarding the acceptance or refusal of the connection requested.

Audited user logon logoff data
UserLock records and reports on every session access event. On a connection event of a domain user to the network, the UserLock agent transmits to the server a set of data. This set includes information on:
Connection event type: Logon, reconnection, disconnection, logoff, lock, unlock
Connection type requested: Workstation, terminal, Wi-Fi, VPN, IIS, RDP & RD Gateway, SaaS
The user: Domain, username
The source: Machine or device name, IP address.
This information is retrieved by the agent itself when the connection event is submitted by the user, and sent encrypted to the UserLock server, which determines the time of the connection request and saves all in its database. Thus all user connection information performed on agent hosts are collected and stored centrally.
Real-time access controls to AD user logons
All data audited at the moment of attempted connection is analyzed to verify if the user requesting the connection is subject to access control rules. Transparent to the user, these controls help verify authenticated users’ claimed identity to protect against unauthorized access and compromised credentials.
Defined for a user account, a user group and/or an organizational unit of users, the rules allow or deny a connection requested by a domain user account. UserLock then transmits this decision to the agent of the relevant system.

Access security is not a one-time activity. Restrictions should be evaluated and revised periodically so that improvements can be implemented. User access control rules can be modified at any time for a user or a group, or to create a temporary rule to define an exception for a particular user. All changes are applied in real time and are effective immediately.
Number of initial access points
UserLock can analyze what the sequence is of an AD user’s logon connections to determine whether a session is a new point of entry to the network or a connection performed from an existing session.
A new point of entry is considered as the initial access point for the user initiating the connection. Limiting the number of initial access points to one will ensure that the user won’t be able to open a session from a second location.

Number of concurrent AD user sessions allowed
The limit of concurrent sessions allowed can be used in association with the limit of initial access points to define how many and which types of session (workstation, terminal, Wi-Fi/VPN, SaaS, and IIS) an AD user can open from the same initial access point.
Control AD user logon access by origin (location)
Define and manage the workstations/terminals, IP range and session type from which a user, group or organizational unit may log on. For example, to restrict a user to connect only from a specific machine.
Control AD user logon access by time
The "Hour restrictions" section allows you to define, by session type, periods of time during which users can or cannot logon to the network. For example, to prevent access connections outside certain hours.
Control AD user logon access by time quota
A connection time quota can be assigned to determine the maximum period of time connected to the network during a recurring period (day,week, month… ) for specified session types.
Automatic logoff of idle AD user sessions
To manage unattended workstations, UserLock can automatically log off sessions after a specific idle time. Every session of the user account is closed after a chosen idle time period.
Alert for defined AD logon events
The user rules also include alert notifications for defined connection events. Two types of alerts can be defined: pop-up messages and email message.
The data audited during the connection, whatever the decision taken (authorized, refused or failed), are analyzed and compared against the criteria of alert triggers — defined for the user requesting the connection.
These alerts are triggered to inform the predefined recipients for the following connection events: logon, logoff, lock, unlock, disconnect, reconnect, logon denied by Windows and logon denied by UserLock. For example alerts can be set for failed logon attempts, attempts to log on to default accounts, logon activity during non-working hours…

Alerts on other suspicious AD logon situations
To better identify other suspicious or inappropriate logon behavior, each user’s access events are correlated with their customized access controls. This type of risk alert includes:
Simultaneous initial access points from inside and outside the local network

A new session from an existing session with different user credentials.

Other alerts include when the number of sessions open is over the limit defined for their account, the number of sessions open by session type is over the adjustable threshold, the frequency of failed logons by UserLock and/or Windows is over the frequency tolerated, the number of initial access points open is over the limit defined for their account and a connection attempt is blocked due to the Active Directory account status.
Respond to AD user logon activity
An immediate response to an alert can help reduce the risk of security breaches. A network administrator can react directly from the UserLock console, from any device (smartphone, tablet or computer).

Simply selecting on one or several sessions in the UserLock console allows you to launch the following actions on the following session types:
Workstation sessions: Logoff the session, lock the session, send a pop-up message, run a computer command.
Terminal sessions: Logoff the session, lock the session, send a pop-up message, run a computer command.
IIS sessions: Logoff the session, run a computer command.
Block AD user logon attempt
For any specific user you can block all logon attempts and close all existing sessions remotely, to react quickly to compromised or suspected compromised credentials.
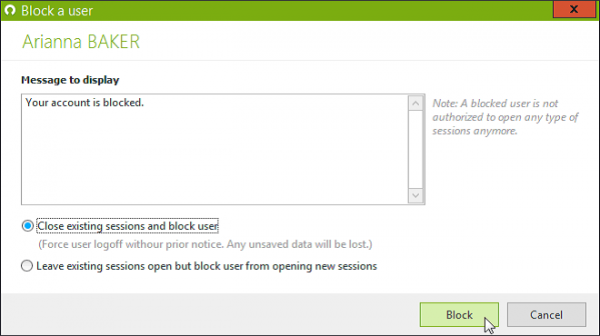
Just select the user from the "user sessions" view and launch the command. Until the user is unblocked, all connection attempts will be denied.
Reporting and auditing on all logon and logoff activity
All user connection information transmitted by the agent are audited and saved centrally in a database. Information stored can be used to generate predefined reports directly from the console.

Fill gaps in your Active Directory user logon logoff security with UserLock
Both external attacks and internal security breaches involve authenticated AD users — who have authorized access and rights to an organization’s network, data or applications. I hope this post outlines how UserLock offers enhanced security for Windows Active Directory user logons to harden the defense against unauthorized network access and compromised credentials.